GUEST ESSAY: Taking a systematic approach to achieving secured, ethical AI model development
The Last Watchdog
MAY 31, 2024
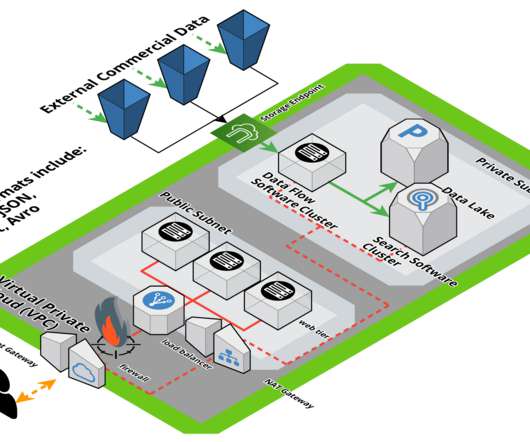
Securing training data is crucial for protecting AI models. Storing training data in encrypted containers or secure databases adds a further layer of security. Digital signatures ensure the integrity and authenticity of models, confirming they have not been altered. Data security. Model Security.











































Let's personalize your content