Academic Study Finds Security Flaws in Online Voting Tool
Data Breach Today
JUNE 12, 2020
The platform is currently in use in three states for military personnel and disabled residents.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Data Breach Today
JUNE 12, 2020
The platform is currently in use in three states for military personnel and disabled residents.

Data Breach Today
OCTOBER 24, 2023
Federal Civilian Agencies 'Are Likely to Resist This Dramatic Change,' Report Says A study of federal government cybersecurity suggests the Department of Homeland Security could play a more prominent role in securing civilian networks, in a report that touts a "more centralized defensive strategy."
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
MAY 16, 2021
The Operation Transparent Tribe (Operation C-Major, APT36, and Mythic Leopard) was first spotted by Proofpoint Researchers in Feb 2016, in a series of cyber espionage operations against Indian diplomats and military personnel in some embassies in Saudi Arabia and Kazakhstan. ” read the analysis published Cisco Talos.

Security Affairs
JANUARY 8, 2023
Polish authorities charged Russian and Belarusian individuals with spying for the Russian military intelligence service (GRU). Polish authorities charged Russian and Belarusian individuals, who were arrested in April, with spying for the Russian military intelligence service (GRU) from 2017 to April 2022.

Security Affairs
MAY 21, 2020
. “The suspected leak involves sensitive information about a prototype of a cutting-edge high speed gliding missile intended for deployment for the defense of Japan’s remote islands amid China’s military assertiveness in the region.” ” states the AP press agency. China, and Russia.

Security Affairs
OCTOBER 9, 2020
government and military personnel will remain in a federal prison. Ardit Ferizi , aka Th3Dir3ctorY, is the hacker that supported the ISIS organization by handing over data for 1,351 US government and military personnel. The man of Kosovar origin was studying computer science in Malaysia. military and other government personnel.

Security Affairs
FEBRUARY 19, 2019
A recent study from technology research company Comparitech looked at cybersecurity around the world and scored 60 countries on their cybersecurity practices. The study found significant differences in how well nations are protecting themselves. The Study’s Methodology. The Study’s Methodology.

Security Affairs
NOVEMBER 17, 2021
The DEV-0343 focuses on defense companies that support United States, European Union, and Israeli government partners producing military-grade radars, drone technology, satellite systems, and emergency response communication systems. The group was aggressive using brute force attacks to obtain access to Office 365 accounts.

Security Affairs
DECEMBER 4, 2020
Ardit Ferizi , aka Th3Dir3ctorY, is the hacker that supported the ISIS organization by handing over data for 1,351 US government and military personnel. The man of Kosovar origin was studying computer science in Malaysia. Ferizi is the first man charged with cyber terrorism that was extradited to the US early this year.

Security Affairs
AUGUST 19, 2019
A study conducted by researchers at Cyjax revealed that organizations expose sensitive data via sandboxes used for malware analysis. CENTCOM requisition form for use of military aircraft. The researchers analyzed PDF documents and email files (. eml ) uploaded to three unnamed sandbox services over a period of three days last week.

Security Affairs
MARCH 15, 2021
Most targeted sectors have been Government/Military (17% of all exploit attempts), followed by Manufacturing (14%), and then Banking (11%). Jang explained that he has published the PoC code to raise the alert on the recent wave of hacks and give the opportunity to colleagues to study the code use in the attacks.

Dark Reading
FEBRUARY 11, 2019
But it can't operate in a bubble, a new Washington Post study indicates.
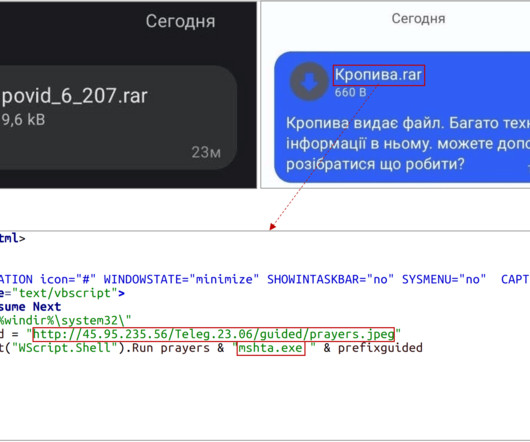
Security Affairs
JULY 15, 2023
The Gamaredon APT group continues to carry out attacks against entities in Ukraine, including security services, military, and government organizations. Gamaredon has been active since 2014 and its activity focus on Ukraine, the group was observed using the multistage backdoor Pteranodon / Pterodo.

Security Affairs
JULY 20, 2019
“According to the data received, the majority of non-public projects of Sytech were commissioned by military unit No. In January 2014, researchers from Karlstad University in Sweden, presented the results of a four-month study conducted to test Tor network exit nodes for sneaky behavior.

Security Affairs
APRIL 12, 2019
The APT28 group has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. According to a report published by Symantec in October, the group was actively conducting cyber espionage campaigns against government and military organizations in Europe and South America.
Security Affairs
MAY 6, 2021
Chinese military unit PLA Unit 61419 is suspected to be involved in cyber-espionage campaigns against multiple antivirus companies. Experts speculate the cyberspies have purchased the security software to study them and find zero-day vulnerabilities that could be exploited in an attack or to test the detection of new malware.

The Last Watchdog
AUGUST 1, 2023
A recent study found that 55% of SOC analysts have considered leaving their jobs due to stress. Cybermindz implements the evidence-based iRest protocol , which has found success within the US Military for almost 20 years and is used to treat conditions like anxiety, depression, and post-traumatic stress.

Schneier on Security
FEBRUARY 26, 2019
A research group at NATO's Strategic Communications Center of Excellence catfished soldiers involved in an European military exercise -- we don't know what country they were from -- to demonstrate the power of the attack technique. Go back and read this scenario from the Center for Strategic and International Studies.

OpenText Information Management
APRIL 2, 2025
We have two sides to the business: we create AI solutions for clients in the military and defense sector, and robotics and automation tools for commercial businesses. Some of our clients in the military and defense sector recommended OpenText, and the solution itself met all our needs. We regard innovation as part of our DNA.
Krebs on Security
FEBRUARY 22, 2024
Security experts who reviewed the leaked data say they believe the information is legitimate, and that i-SOON works closely with China’s Ministry of State Security and the military. “In the area of cyberwarfare, the western governments see cyberspace as a ‘fifth domain’ of warfare,” the Margin study observed.
Security Affairs
FEBRUARY 13, 2021
The Military Chinese General and Philosopher Sun Tzu (544 BC – 496 BC) wrote these tactics over two thousand years ago, and it is as applicable today as it ever was. If their forces are united, separate them. If sovereign and subject are in accord, put division between them.
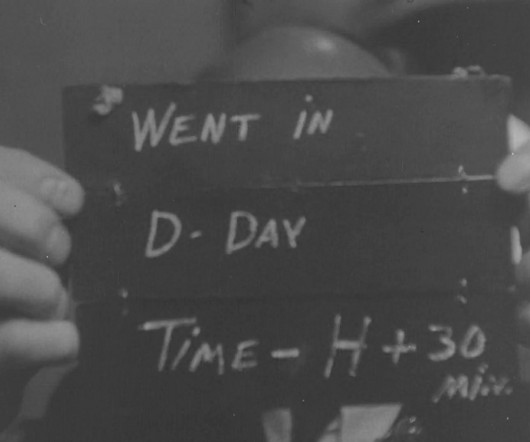
Unwritten Record
JUNE 4, 2024
In what became known as the largest amphibious invasion in military history, the operation, codenamed Overlord , was the beginning of the liberation of Northern Europe from Nazi occupation. Military since the 1880s to document combat and support operations visually. Combat camera operators, many of whom were U.S.

Schneier on Security
OCTOBER 5, 2023
A Columbia Journalism Review study found that most major news outlets used Russian tweets as sources for partisan opinion. The military officers in Russia, China, and elsewhere in charge of election interference are likely to have their best people thinking of others. That’s just one scenario.

The Last Watchdog
SEPTEMBER 17, 2018
Should law enforcement and military officials have access to a digital backdoor enabling them to bypass any and all types of encryption that exist today? Venafi: Cambridge Analytica is just an amazing case study of what can happen when machines can actually pull all this information together, and the massive power of that.

Unwritten Record
MAY 31, 2022
Typical records found in this series include terrain studies, maps showing defenses, maps relating to military operations, maps showing engineer activities, maps showing roads and bridges, and maps showing administrative boundaries. Among these are maps of Tunisia annotated to show military operations at Kasserine Pass.

Security Affairs
OCTOBER 28, 2019
Precision engineering is a very important business market in Europe, it includes developing mechanical equipment for: automotive, railways, heavy industries and military grade technology. Today I’d like to share a quick analysis of an interesting attack targeting precision engineering companies based in Italy.

Schneier on Security
OCTOBER 9, 2023
It’s widely believed that Jaan Tallinn , the wealthy long-termer who co-founded the most prominent centers for the study of AI safety, has made dismissive noises about climate change because he thinks that it pales in comparison with far-future unknown unknowns like risks from AI. The technology historian David C.

Unwritten Record
OCTOBER 3, 2019
A special edition of “Air Force Television News” distributed the press conference to members of the military. After World War II, more women expressed interest in serving in the military and the act enabled them to serve as permanent, regular members of the armed forces during times of peace.

eSecurity Planet
FEBRUARY 25, 2022
The development of cryptology has been critical to safeguarding data for government agencies, military units, companies, and today’s digital users. The study of codes divides into: Cryptography : the methodology and applications for encrypting data. Cryptanalysis : the processes and methods to break codes and decrypt messages.

The Last Watchdog
NOVEMBER 28, 2018
Meanwhile, Pinckney’s Darga has taken the initiative to spearhead efforts to cater to military veterans and to disabled individuals, as well, particularly persons with autism. The student thrived in Washtenaw’s cybersecurity track and landed a new career as a pen tester for a German auto supplier.

Data Matters
SEPTEMBER 21, 2022
Spencer Overton , President, Joint Center for Political and Economic Studies. military and intelligence personnel. Harlan Yu , Executive Director, Upturn. Karen Kornbluh , Director, Digital Innovation and Democracy Initiative, German Marshall Fund. Stacey Gray , Senior Director for U.S. Policy, Future of Privacy Forum (FPF).

Unwritten Record
JANUARY 9, 2020
Goldman is a PhD Candidate in Cinema Studies at New York University. The military went to tremendous lengths to supply a steady diet of fiction and nonfiction film to its troops with great speed. This post was written by guest blogger Tanya Goldman. The ease with which most of us stream movies and television makes it hard to.

Unwritten Record
DECEMBER 7, 2021
The USACE is not only responsible for the building of large-scale military projects but also a major chunk of the country’s civil engineering works as well. It then goes into detail about the specific functions that the corps performs, beginning with the military side. This is to ensure that the harbor remains operational and stable.

The Texas Record
SEPTEMBER 28, 2021
Also research the impact of the information’s proximity to potential man-made hazards, for example the airport, military bases, plants or factories that handle hazardous or flammable material. Also, assess infrastructure that if faulty would cause lose of information. Outline and implement security measures to protect this information.

eSecurity Planet
MAY 25, 2022
To no one’s surprise, the study of cryptography and advancements in encryption are essential to developing cybersecurity. Cryptology is the overarching field of study related to writing and solving codes, whereas encryption and decryption are the central processes driving the computer science discipline. The Move to HTTPS.

Unwritten Record
MARCH 25, 2021
You may have heard that the National Archives is partnering with the University of Maryland Cinema and Media Studies Program to present Films of State , an online conference on government-produced moving images (if not, check out my last blog post for more background).

Archives Blogs
SEPTEMBER 10, 2018
After two years in the Navy and earning Lieutenant Commander rank, Austin was transferred to “military government school” at Princeton University to prepare him for service in the future occupations of Korea and Japan. Dr. Oliver Austin, 1945-1952 [ original record ].

Unwritten Record
MARCH 11, 2021
We’ve partnered with the University of Maryland Cinema and Media Studies program and gathered an international slate of scholars to discuss some of the latest research on films made by the US government, covering federal organizations from the United States Army Signal Corps to the Office of Economic Opportunity and everything in between.

Hunton Privacy
APRIL 16, 2009
Late in 2008, the Center for Strategic and International Studies Commission on Cyber Security for the 44th Presidency (the Commission) released a report citing the U.S.’s In a global economy, where economic strength and technological leadership are as important to national power as military force, failing to secure cyberspace puts the U.S.

Archives Blogs
DECEMBER 6, 2019
During their visit, they scanned 1,627 pages of Compiled Military Service Records! These records will be available online in the National Archives Catalog in just a few weeks. Students in the National Archives Innovation Hub. Photo by Catherine Brandsen.

ForAllSecure
JULY 13, 2021
In 2019, the International Information System Security Certification Consortium (ISC2) released a workforce study found that there’s a shortage of infosec experts, a shortage that’s estimated to be nearly 4.8 In the Federal space, military software systems, for example, need to last decades out in the field.

The Security Ledger
MAY 3, 2022
and Western nations’ military support of Ukraine’s army. These attacks would be enabled by the same platform that was used to frustrate thieves in Russian military garb, according to experts in agriculture and information security who have studied the problem. critical infrastructure in retaliation for U.S.

Unwritten Record
AUGUST 20, 2024
These efforts were especially prevalent during World War II, with members of the military resorting to….unique One of these specific conditions is that the photocopy or reproduction is not to be “used for any purpose other than private study, scholarship, or research.” unique ways of repelling the pests.

IBM Big Data Hub
FEBRUARY 6, 2024
Disaster recovery can refer to everything from equipment failures, power outages, cyberattacks, civil emergencies, natural disasters and criminal or military attacks, but it is most commonly used to describe events with non-malicious causes. What is cyber recovery?
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content