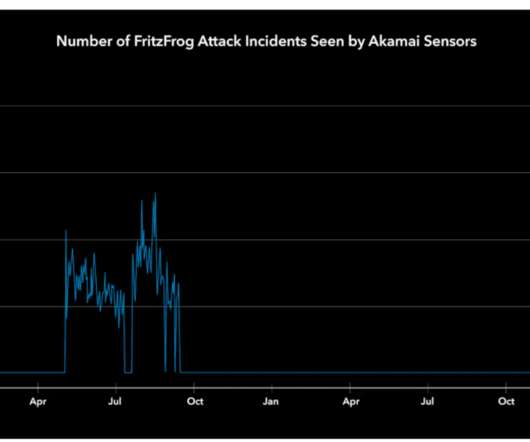
FritzFrog P2P Botnet is back and targets Healthcare, Education and Government Sectors
Security Affairs
FEBRUARY 11, 2022
Experts discovered infected machines in a European television channel network, a Russian manufacturer of healthcare equipment, and multiple universities in East Asia. “The new implementation uses a public SCP library written in Golang in GitHub. It is, however, notable that the writers of the SCP library are located in China.”

















Let's personalize your content