Google Removes Fake Crypto-Mining Apps
Data Breach Today
AUGUST 24, 2021
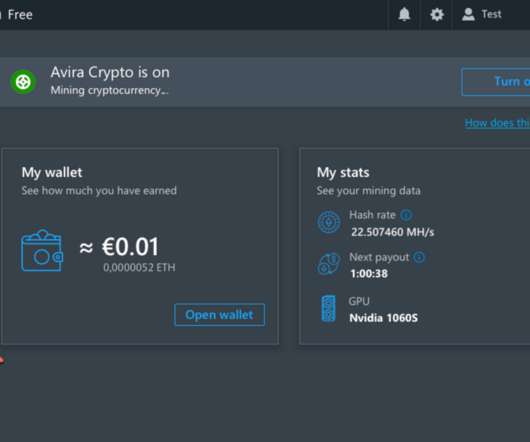
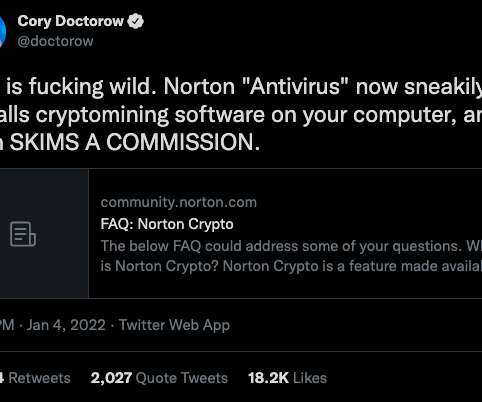
Researchers Say Users Paid Fees for Fake Mining Services Google has removed eight fake crypto-mining apps from its Play Store, but security researchers have flagged 120 similar apps still available on the store, according to Trend Micro. Users paid for services the eight apps never delivered.

































Let's personalize your content