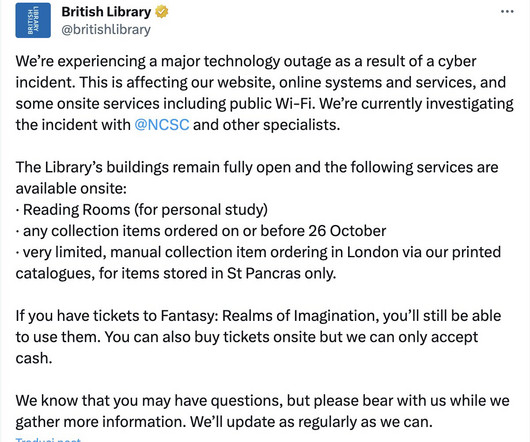
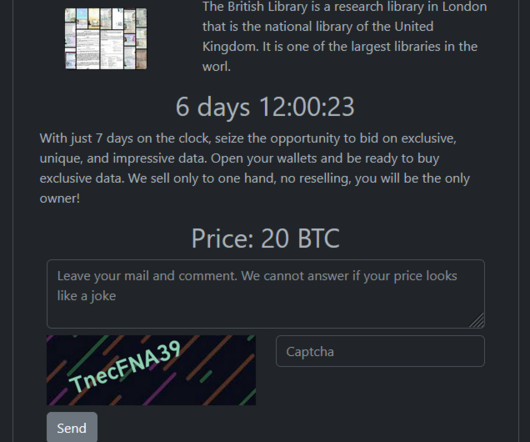
Foreign adversary hacked email communications of the Library of Congress says
Security Affairs
NOVEMBER 18, 2024
The Library of Congress discloses the compromise of some of its IT systems, an alleged foreign threat actor hacked their emails. Only email communications between congressional offices and some library staff, including the Congressional Research Service, from January to September, were affected. ” reported the NBC News.







































Let's personalize your content