Breach Roundup: Canada Bans WeChat and Kaspersky Apps
Data Breach Today
NOVEMBER 2, 2023
Also: Iranian State Hackers Stalk Middle Eastern Governments This week, Canada banned WeChat and Kaspersky apps, REvil members faced trial in a Russian military court, the British Library experienced an IT outage, Iranian state-backed hackers targeted Middle East governments and European officials extended the ban on Meta's behavioral advertising practices. (..)






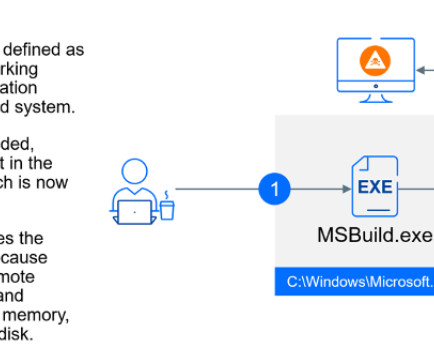






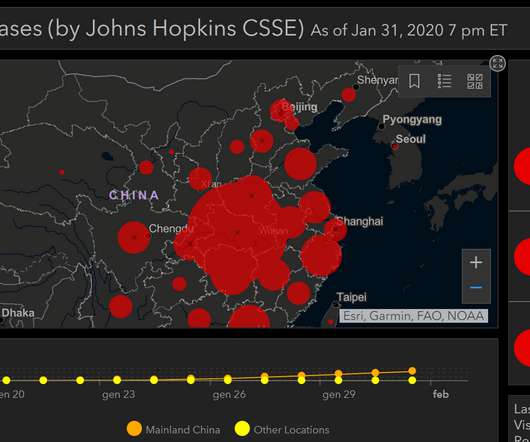

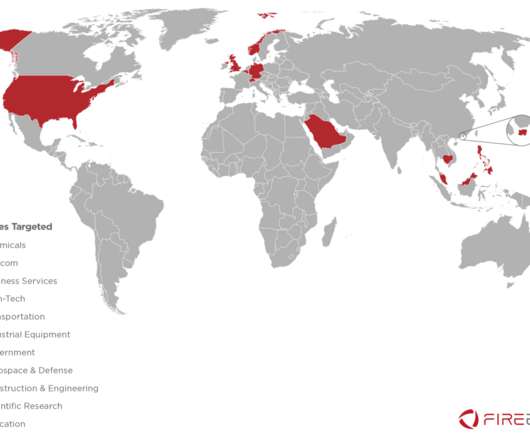
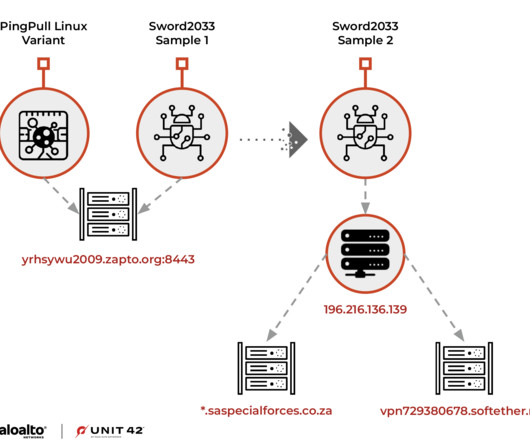





























Let's personalize your content