First Multistate HIPAA Data Breach Lawsuit May Signal Increased State Interest in Data Security Enforcement
Data Matters
FEBRUARY 6, 2019
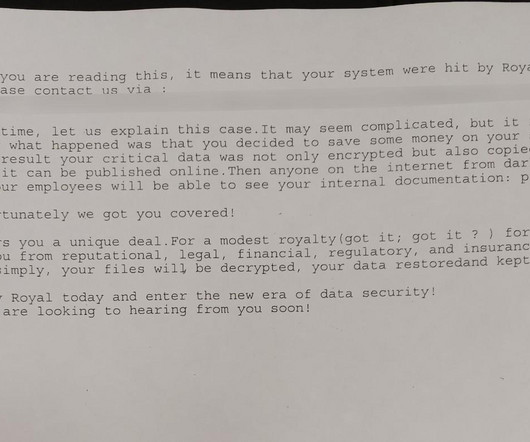
According to the complaint, over a period of 19 days, hackers were able to infiltrate the Company’s computer systems. They argue that the Company failed to protect its computer systems adequately, take steps to prevent the breach, disclose material facts to consumers, and provide timely and adequate notice, among other things.


















Let's personalize your content