Panasonic Warns That IoT Malware Attack Cycles Are Accelerating
WIRED Threat Level
AUGUST 9, 2023
The legacy electronics manufacturer is creating IoT honeypots with its products to catch real-world threats and patch vulnerabilities in-house.

WIRED Threat Level
AUGUST 9, 2023
The legacy electronics manufacturer is creating IoT honeypots with its products to catch real-world threats and patch vulnerabilities in-house.

Security Affairs
SEPTEMBER 30, 2019
After 2 years of waiting, MalwareMustDie returns with an excellent page of malware analysis of a new IoT malware: Linux/AirDropBot. The beginning of the story: another IoT malware in the wild? Coming to the core topic: IoT botnet threat and their ecosystem.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
JUNE 22, 2019
In September 2018, researchers observed the Hide and Seek (HNS) IoT botnet targeting Android devices with ADB option enabled. The malicious code attempt to determine if it is running in a honeypot , then it downloads the payload and changes its permission settings to allow its execution. The script for a.
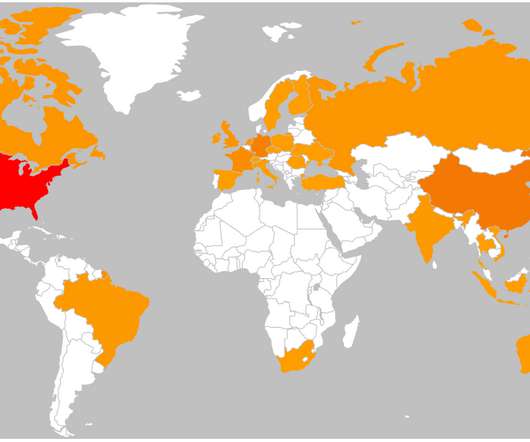
Security Affairs
APRIL 28, 2020
The Outlaw Botnet uses brute force and SSH exploit (exploit Shellshock Flaw and Drupalgeddon2 vulnerability ) to achieve remote access to the target systems, including server and IoT devices. The first version spotted by TrendMicro includes a DDoS script that could be used by botmaster to set-up DDoS for-hire service offered on the dark web.

Thales Cloud Protection & Licensing
FEBRUARY 28, 2022
To enable this revolution, automobile manufacturers and their supply chain partners have rapidly adopted new technologies to better serve customers and win competitive advantages: Embedding high-speed connectivity in vehicles to improve customer experience and entertainment as well as real-time diagnostics and OTA updates.

eSecurity Planet
MARCH 22, 2023
Some applications, cloud infrastructure, networking equipment, or Internet of Things (IoT) devices may require more sophisticated ITAM or additional tools to detect them. IoT devices such as security cameras, temperature sensors, or heat monitors will be added to networks and often possess security flaws.
Let's personalize your content