CISA: AI Tools Give Feds 'Negligible' Security Improvements
Data Breach Today
JULY 31, 2024
Federal AI Security Tools Require Substantial Training, Offer Minimal Improvements The U.S.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Data Breach Today
JULY 31, 2024
Federal AI Security Tools Require Substantial Training, Offer Minimal Improvements The U.S.

eSecurity Planet
APRIL 26, 2024
Network security architecture is a strategy that provides formal processes to design robust and secure networks. Effective implementation improves data throughput, system reliability, and overall security for any organization. Network Elements Networks connect physical and virtual assets and control the data flow between them.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

eSecurity Planet
OCTOBER 9, 2024
Configuration management tools are key to delivering the DevOps promise of shortened development windows and a pipeline of continuous integration and continuous deployment (CI/CD). Benefits of Configuration Management Tools <BODY>Why use configuration management tools? Triaging system-wide action items and remediation.

Data Breach Today
JUNE 12, 2024
High-Assurance Security Tech Boosts Everfox's Government and Infrastructure Tools Everfox's purchase of Garrison Technology is set to fortify its cybersecurity offerings, especially for government and critical infrastructure.

Data Breach Today
DECEMBER 8, 2020
Security Vendor Believes No Customer Data Was Exfiltrated FireEye, one of the world's top cybersecurity firms, says in a striking announcement on Tuesday that attackers stole its penetration testing tools and sought information about its government clients. However, FireEye doesn't believe the attackers exfiltrated data.

Security Affairs
MAY 27, 2021
Threat actors have compromised offices of multiple Japanese agencies via Fujitsu ‘s ProjectWEB information sharing tool. Threat actors have breached the offices of multiple Japanese agencies after they have gained access to projects that uses the Fujitsu ‘s ProjectWEB information sharing tool. The Cabinet Cyber ??Security

Collibra
JUNE 27, 2024
More broadly, AI software is expensive to develop, especially as HIPAA requirements present added security considerations for protected health information. What’s more, AI tools are not guaranteed to improve the patient-provider experience and could potentially even worsen it. The two can coexist, but there needs to be a balance.

Security Affairs
NOVEMBER 18, 2024
GDPR protects sensitive data like health and financial details, and its enforcement underscores the growing need for stronger data security measures. These penalties apply to all aspects of GDPR compliance, including inadequate data security, improper consent, and data breach failures. government surveillance.

eSecurity Planet
AUGUST 26, 2021
In fact, there are more than a few flaws present, as well as the occasional gaping security hole. Code debugging and code security tools exist to find and help developers fix the problems that occur. Such tools typically capture exceptions as they occur and provide diagnostic and contextual data to make resolution easier.
Security Affairs
AUGUST 13, 2024
CERT-UA warned that Russia-linked actor is impersonating the Security Service of Ukraine (SSU) in a new phishing campaign to distribute malware. The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new phishing campaign targeting organizations in the country, including government entities.

IT Governance
DECEMBER 9, 2020
The cyber security giant FireEye announced yesterday that it had been targeted by a sophisticated cyber attack , which resulted in criminals stealing an arsenal of hacking tools. FireEye uses these tools to test the defences of its clients, which include an array of government and US national security agencies.

eSecurity Planet
JULY 12, 2023
Cloud security posture management (CSPM) tools continuously monitor, identify, score, and remediate security and compliance concerns across cloud infrastructures as soon as problems arise. usage fee per Enterprise Cloud Security Platform unit used. usage fee per Enterprise Cloud Security Platform unit used.
Security Affairs
OCTOBER 17, 2024
Russia-linked threat actor RomCom targeted Ukrainian government agencies and Polish entities in cyber attacks since late 2023. The group uses multiple tools and malware languages (GoLang, C++, RUST, LUA) to establish long-term access for espionage, possibly followed by ransomware deployment for disruption and profit.

eSecurity Planet
JULY 12, 2024
Cloud database security refers to the set of techniques and procedures used to shield cloud-based storage from malicious or unintentional attacks. This security approach protects against common threats like data breaches, DDoS assaults, viruses, hackers, and unauthorized access in cloud environments. Deploy data discovery tools.
Krebs on Security
APRIL 2, 2020
And according to data gathered by a new automated Zoom meeting discovery tool dubbed “ zWarDial ,” a crazy number of meetings at major corporations are not being protected by a password. zWarDial, an automated tool for finding non-password protected Zoom meetings.
Data Breach Today
SEPTEMBER 6, 2024
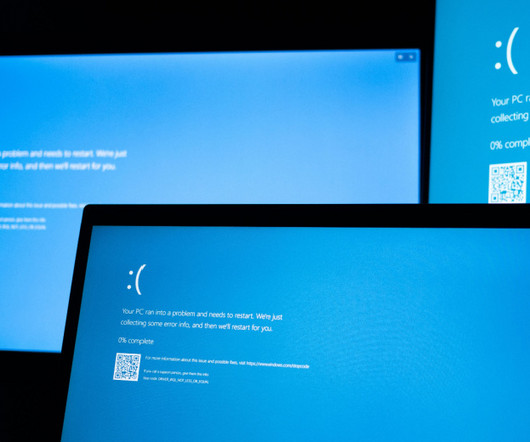
Global Outage Triggers Calls for 'Less-Invasive Access' to Essential Functions The global disruption caused by a faulty CrowdStrike software triggering a kernel panic and computer meltdowns has led government agencies, experts and vendors to call for rethinking Windows operating system resiliency, including the deep-level OS access security tools now (..)
Gimmal
AUGUST 8, 2024
In the digital era, the concepts of information governance and data governance have become increasingly significant. This blog post delves into the distinctions between information governance and data governance, offering clarity on each term’s scope, objectives, and practices.

Data Breach Today
JANUARY 17, 2023
Push Technology and One-Time Passcodes for MFA Just Aren't Secure Enough Attackers have caught up with legacy multifactor authentication tools that use push technology or one-time passcodes, boosting the need for phishing-resistant MFA, says Jeremy Grant.
Security Affairs
OCTOBER 9, 2024
A threat actor tracked as Awaken Likho is targeting Russian government agencies and industrial entities, reported cybersecurity firm Kaspersky. The threat actor continues to target Russian government entities and enterprises. ” reads the report.

Security Affairs
APRIL 22, 2024
Russia-linked APT28 group used a previously unknown tool, dubbed GooseEgg, to exploit Windows Print Spooler service flaw. Microsoft reported that the Russia-linked APT28 group (aka “ Forest Blizzard ”, “ Fancybear ” or “ Strontium ” used a previously unknown tool, dubbed GooseEgg, to exploit the Windows Print Spooler flaw CVE-2022-38028.

eSecurity Planet
MAY 27, 2021
With almost every aspect of business becoming more digital, enterprise network security software minimizes the impact of cyberattacks — especially as guarding against them protects a company’s operations and safeguards its competitiveness in a fast-moving marketplace. Top network security tools. Network Security Product.

Security Affairs
FEBRUARY 19, 2022
CISA has created a list of free cybersecurity tools and services that can help organizations increase their resilience. The list includes open source tools and free resources provided by government organizations and private cybersecurity firms. The list also includes tens of tools are open source. Pierluigi Paganini.

AIIM
NOVEMBER 22, 2022
Now imagine cloud-based collaboration tools were never invented. There are no video meetings, digital whiteboards, or real-time document collaboration tools. The US economy took some punches during the height of the COVID pandemic, but nothing like it would have if these incredible tools didn’t exist. How does business get done?

Collibra
NOVEMBER 4, 2024
Data governance is vital for organizations to access trustworthy and secure data. By designating business ownership of core data assets, data governance helps resolve conflicting definitions and overlaps. By designating business ownership of core data assets, data governance helps resolve conflicting definitions and overlaps.

Collibra
AUGUST 28, 2024
Case in point — AI governance and AI model management. A major factor in the confusion lies in not understanding the three main different approaches to AI governance. This flavor of AI governance helps AI and data teams implement AI use-cases by preparing, developing, running and monitoring AI models.

erwin
DECEMBER 6, 2019
In the data-driven era, CIO’s need a solid understanding of data governance 2.0 … Data governance (DG) is no longer about just compliance or relegated to the confines of IT. Today, data governance needs to be a ubiquitous part of your organization’s culture. Creating a Culture of Data Governance. Data Storage.

Collibra
JULY 2, 2024
But as most businesses recognize, innovation is nothing without the right governance to ensure that risks don’t get out of hand. Enter the unstructured data experts from Ohalo , who recently showcased their unstructured data management and classification tool, Data X-Ray with Collibra at the Data Citizens 2024 conference.

The Last Watchdog
JUNE 6, 2022
Related: Why security teams ought to embrace complexity. As RSA Conference 2022 gets underway today in San Francisco, advanced systems to help companies comprehensively inventory their cyber assets for enhanced visibility to improve asset and cloud configurations and close security gaps will be in the spotlight. Smart questions.

Schneier on Security
SEPTEMBER 8, 2023
Last March, just two weeks after GPT-4 was released , researchers at Microsoft quietly announced a plan to compile millions of APIs—tools that can do everything from ordering a pizza to solving physics equations to controlling the TV in your living room—into a compendium that would be made accessible to large language models (LLMs).
Security Affairs
SEPTEMBER 25, 2023
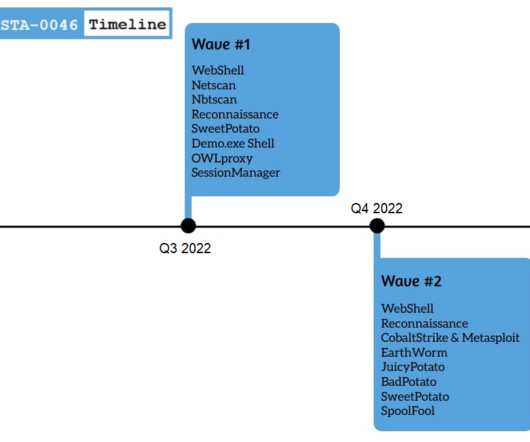
A stealthy APT group tracked as Gelsemium was observed targeting a Southeast Asian government between 2022 and 2023. Palo Alto Unit42 researchers an APT group tracked as Gelsemium targeting a Southeast Asian government. OwlProxy is a unique and custom tool used by the group. appeared first on Security Affairs.

The Last Watchdog
APRIL 16, 2020
In many cases, the lateral movement phase is being facilitated by the hijacking of an ubiquitous network administrator’s tool: Windows Active Directory, or AD. NotPetya wrought $10 billion in damages , according to Tom Bossert a senior Department of Homeland Security official at the time. I’ll keep watch.

Schneier on Security
NOVEMBER 1, 2022
It’s Iran’s turn to have its digital surveillance tools leaked : According to these internal documents, SIAM is a computer system that works behind the scenes of Iranian cellular networks, providing its operators a broad menu of remote commands to alter, disrupt, and monitor how customers use their phones.

Collibra
AUGUST 4, 2023
These are the primary reasons we start data governance programs: To make sure we’re managing data as a critical resource and generating maximum business value from it. When we start,it’s important to remember that data governance is a program, not a project. It requires ongoing efforts. They think that the job is done.

Security Affairs
JANUARY 9, 2022
The US NCSC and the Department of State published joint guidance on defending against attacks using commercial surveillance tools. In the last years, we have reported several cases of companies selling commercial surveillance tools to governments and other entities that have used them for malicious purposes. Pierluigi Paganini.

IBM Big Data Hub
APRIL 11, 2024
The global AI governance landscape is complex and rapidly evolving. Key themes and concerns are emerging, however government agencies must get ahead of the game by evaluating their agency-specific priorities and processes. Compliance with official policies through auditing tools and other measures is merely the final step.

Gimmal
NOVEMBER 7, 2024
In the rapidly evolving digital landscape, information governance has become more critical than ever. As we approach 2025, organizations face new challenges and opportunities in managing, securing, and extracting value from their data. Security Concerns Will Persist: Challenges in protecting data across diverse environments.

WIRED Threat Level
OCTOBER 28, 2023
Plus: Details emerge of a US government social media-scanning tool that flags “derogatory” speech, and researchers find vulnerabilities in the global mobile communications network.

eSecurity Planet
MARCH 17, 2022
The growth of DevSecOps tools is an encouraging sign that software and application service providers are increasingly integrating security into the software development lifecycle (SDLC). This article looks at the best commercial and open source DevSecOps tools and what to consider when evaluating DevSecOps solutions.

AIIM
SEPTEMBER 7, 2021
What is Information Governance, and Why is it Important? There are many benefits to constructing an Information Governance program plan. How to Avoid Information Governance Pitfalls. Vendor-neutral research, or case studies, can be valuable tools when communicating with internal decision-makers.
Security Affairs
APRIL 17, 2023
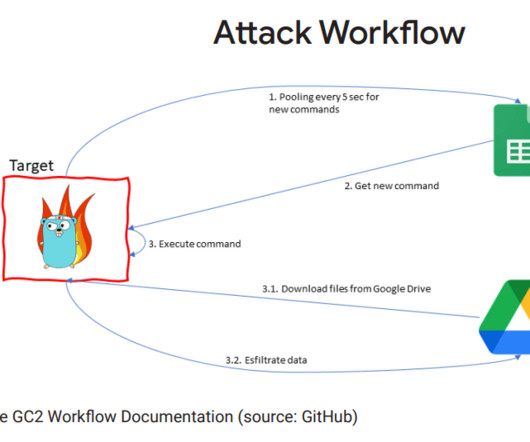
China-linked APT41 group used the open-source red teaming tool GC2 in an attack against a Taiwanese media organization. Google Threat Analysis Group (TAG) team reported that the China-linked APT41 group used the open-source red teaming tool Google Command and Control ( GC2 ) in an attack against an unnamed Taiwanese media organization.

AIIM
AUGUST 10, 2021
The information flow is complicated, and the governance implications are substantial. Every aspect of content flow and collaboration – including Microsoft Teams and its information—must be integral to the organization’s approach to information governance. What is your existing Information Governance strategy?

OpenText Information Management
SEPTEMBER 10, 2024
Public sector agencies across federal, state, and local governments want to deliver reliable and secure services to their employees, contractors, citizens, and other fellow agencies. Because such agencies may be the target from multiple threat actors and have access to sensitive data, they have stringent security requirements.

Security Affairs
MARCH 21, 2021
US CISA has released a new tool that allows detecting malicious activity associated with the SolarWinds hackers in compromised on-premises enterprise environments. Below an excerpt of the CISA’s announcement : “This Alert announces the CISA Hunt and Incident Response Program (CHIRP) tool.

Thales Cloud Protection & Licensing
NOVEMBER 27, 2023
How better key management can close cloud security gaps troubling US government (Part 1 of 2) sparsh Tue, 11/28/2023 - 05:20 Bruce Schneier recently blogged : A bunch of networks, including US Government networks , have been hacked by the Chinese. But “negligent security practices” are not a new concern for the US Government.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content