Good Governance is About the “Why”
Weissman's World
JANUARY 30, 2025
I get inquiries all the time from people seeking support as they ready to tackle what sound like fairly specific records and information governance issues.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Weissman's World
JANUARY 30, 2025
I get inquiries all the time from people seeking support as they ready to tackle what sound like fairly specific records and information governance issues.

Security Affairs
AUGUST 16, 2020
The Australian government aims at giving itself the power to manage the response of private enterprises to cyber attacks on critical infrastructure. The Australian government wants to increase the security of critical infrastructure, for this reason, it plans to manage the response of private enterprises to cyber attacks targeting them.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Weissman's World
SEPTEMBER 4, 2024
Someone came to me once and said “We’ve got boxes of paper records all over the place – in the hallways, in people’s workspaces, never mind in the THREE outside warehouses we have just to store the old stuff.
Security Affairs
MAY 21, 2020
“Victims of the analyzed campaigns fit into the pattern preferred by this actor, such as air transport and government sectors in the Middle East,” reads the researcher paper published by the experts. The post Iran-linked Chafer APT group targets governments in Kuwait and Saudi Arabia appeared first on Security Affairs.
Advertisement
In this paper, we explore the top considerations for building a cloud data lake including architectural principles, when to use cloud data lake engines and how to empower non-technical users. Read this paper to learn about: The value of cloud data lakes as the new system of record.

AIIM
NOVEMBER 5, 2020
This same terminology disorientation has been true in the governance arena as well, with varying uses and interpretations of “Records Management” and “Information Governance.”. The confusion has left some organizations asking, “Do we need Records Managers, or do we need Information Governance professionals?”. People love paper.

AIIM
OCTOBER 6, 2020
The reality is that the task can no longer be handled by traditional manual approaches, many of which were based upon a paper paradigm. That “something” is the automation of information governance. However, making this case about governance automation to executives and senior management is no easy task.

Hunton Privacy
MARCH 29, 2023
On March 29, 2023, the UK government published a white paper on artificial intelligence (“AI”) entitled “A pro-innovation approach to AI regulation.” The UK government believes this will encourage investment in AI and support its adoption throughout the economy. Strengthen the UK’s position as a global leader in AI.

Data Matters
OCTOBER 21, 2021
On 22 September 2021, the UK Government (the “ Government ”) published its Artificial Intelligence (“ AI ”) strategy. The paper outlines the Government’s plan to make Britain a “global superpower” in the AI arena, and sets out an agenda to build the most “pro-innovation regulatory environment in the world”.

Hunton Privacy
JANUARY 20, 2023
On January 20, 2023, The Centre for Information Policy Leadership (“CIPL”) at Hunton Andrews Kurth published “Digital Assets and Privacy,” a discussion paper compiling insights from workshops with CIPL member companies that explored the intersection of privacy and digital assets, with a particular focus on blockchain technology.

Hunton Privacy
FEBRUARY 23, 2024
On February 21, 2024, the Centre for Information Policy Leadership at Hunton Andrews Kurth LLP (“CIPL”) published a white paper on Building Accountable AI Programs: Mapping Emerging Best Practices to the CIPL Accountability Framework. A risk-based technology-agnostic approach is the most effective and appropriate approach for AI governance.

Security Affairs
JUNE 28, 2022
This paper provides a taxonomic classification of non-state actors in the cyberspace, analyzing their role and impact on a state’s socioeconomic structure. For this reason, the behavior of each actor in the cyber arena is becoming a national security concern for every government. Follow me on Twitter: @securityaffairs and Facebook.

Data Breach Today
JANUARY 4, 2023
Government Offices Revert to Pen and Paper; Up to 400 Counties Affected by Attack Hundreds of U.S. counties continue to work with pen and paper after a cyberattack on their digital records management vendor last week disrupted methods to view, add and edit government records.

Security Affairs
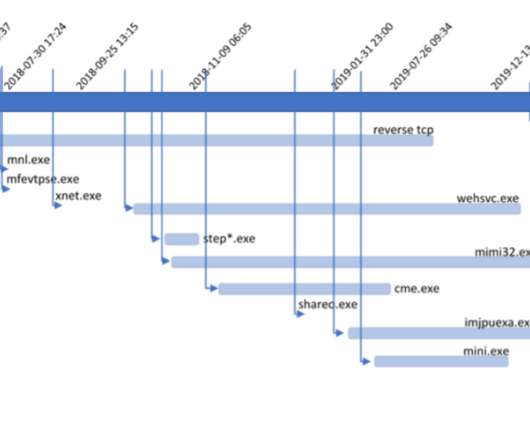
NOVEMBER 8, 2018
Security researchers revealed in a recent paper that over the past years, China Telecom used BGP hijacking to misdirect Internet traffic through China. Demchak and Yuval Shavitt revealed in a recent paper that over the past years, China Telecom has been misdirecting Internet traffic through China. ” states the paper.

Hunton Privacy
OCTOBER 9, 2023
On September 29, 2023, the Centre for Information Policy Leadership at Hunton Andrews Kurth (“CIPL”) released a new paper on its Ten Recommendations for Global AI Regulation. The paper seeks to guide AI policymaking and regulation to ensure the development and deployment of accountable, responsible, and trustworthy AI.

erwin
DECEMBER 6, 2019
In the data-driven era, CIO’s need a solid understanding of data governance 2.0 … Data governance (DG) is no longer about just compliance or relegated to the confines of IT. Today, data governance needs to be a ubiquitous part of your organization’s culture. Creating a Culture of Data Governance. Data Storage.
Security Affairs
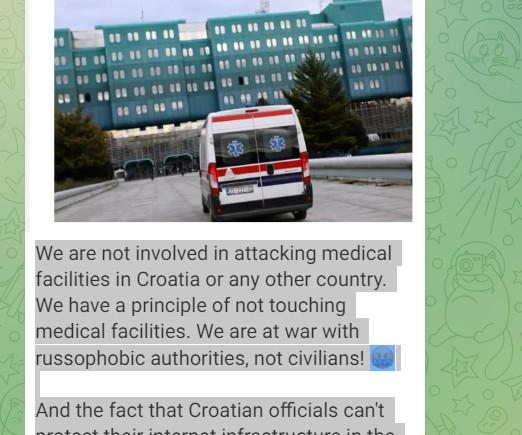
JUNE 28, 2024
Milivoj Novak, assistant director of health care quality and supervision of KBC Zagreb, said in tonight’s show “Otvoreno” that the shutdown of the IT system took the hospital back 50 years – to paper and pencil. It’s unclear if the hospital was victim of a ransomware attack.
Security Affairs
FEBRUARY 12, 2024
” reads the paper published by the researchers “We successfully decrypted the data using the regenerated random number generator. ” reads the paper. ” continues the paper. ” concludes the paper. To the best of our knowledge, this is the first successful decryption of Rhysida ransomware.”

Security Affairs
JANUARY 31, 2021
Last year, the group published a detailed analysis on how the Chinese government has improved its surveillance system to detect and block the popular circumvention tools Shadowsocks and its variants. ” reads the paper published by the experts. ” reads the paper published by the experts.

Data Breach Today
SEPTEMBER 12, 2019
Government Invites Feedback on Addressing Cyber Challenges The Australian government is looking to update its national cybersecurity strategy by 2020. In preparation, it's released a discussion paper that seeks input from citizens, the business community, academics and other stakeholders.

Krebs on Security
OCTOBER 31, 2021
” The research paper, which dubbed the vulnerability “ Trojan Source ,” notes that while both comments and strings will have syntax-specific semantics indicating their start and end, these bounds are not respected by Bidi overrides. The Trojan Source research paper is available here (PDF).

IG Guru
SEPTEMBER 7, 2023
The post White Paper: THIRD-PARTY RISK MANAGEMENT: TAMING THE BEAST USING INFORMATION GOVERNANCE first appeared on IG GURU. Download the report here.

ARMA International
JANUARY 20, 2021
Just tell me which records we must retain in paper! This is a common frustration among records managers and information governance (IG) professionals. Retaining Paper or Electronic Records in the United States. These exceptions do not explicitly require retention in paper copies. checks and assignable promissory notes).

Data Protection Report
FEBRUARY 4, 2024
The Draft GenAI Governance Framework may be accessed here. Views on the Draft GenAI Governance Framework may be provided to the IMDA at info@aiverify.sg. Views on the Draft GenAI Governance Framework may be provided to the IMDA at info@aiverify.sg. A second edition of the Model AI Governance Framework was issued in 2020 [1].

Hunton Privacy
FEBRUARY 6, 2024
On February 6, 2024, the UK government published a response to the consultation on its AI Regulation White Paper, which the UK government originally published in March 2023. A 12-week consultation on the White Paper was then held and this response summarizes the feedback and proposed next steps.

Hunton Privacy
DECEMBER 16, 2021
On December 6, 2021, the Centre for Information Policy Leadership (“CIPL”) at Hunton Andrews Kurth LLP published a white paper on “ Bridging the DMA and the GDPR – Comments by the Centre for Information Policy Leadership on the Data Protection Implications of the Draft Digital Markets Act ” (the “White Paper”).

Security Affairs
NOVEMBER 1, 2018
Attackers used a malware similar to Stuxnet , the cyber weapon that hit the Iranian nuclear plant at Natanz in 2010 interfering with nuclear program of the Government of Teheran. A few days ago, Gholamreza Jalali, the head of Iran’s civil defense agency confirmed that government experts have uncovered and neutralized a new strain of Stuxnet.

AIIM
MAY 11, 2021
A staple of many Information Technology (IT) policy suites is the Acceptable Use Policy (AUP), intended to govern what people working in the organization can and cannot do with the technology we provide them. When the organization gave out ballpoints and pads, did it make people agree to a Pens and Paper Acceptable Use Policy ?

The Last Watchdog
FEBRUARY 25, 2019
based supplier of identity access management (IAM) systems, which recently announced a partnership with Omada, a Copenhagen-based provider of identity governance administration (IGA) solutions. Governance and attestation quickly became a very big deal. Compliance became a huge driver for governance and attestation,” Curcio said. “It

DLA Piper Privacy Matters
SEPTEMBER 10, 2021
The government has today published its eagerly awaited Consultation Paper on Reforms to the UK Data Protection Regime – ‘Data: A New Direction’ (“ Consultation Paper ”), setting out the specific areas for regulatory reform of the UK’s data protection regime. Reducing barriers to responsible innovation.

The Last Watchdog
NOVEMBER 4, 2021
The California Consumer Privacy Act (CCPA), soon to be superseded by the California Privacy Rights Act (CPRA) on January 1, 2023, applies to both electronic and paper records. This is a significant difference, given the increased difficulty of manually classifying paper records. Dealing with legacy systems. Less can be more.
Security Affairs
JUNE 23, 2021
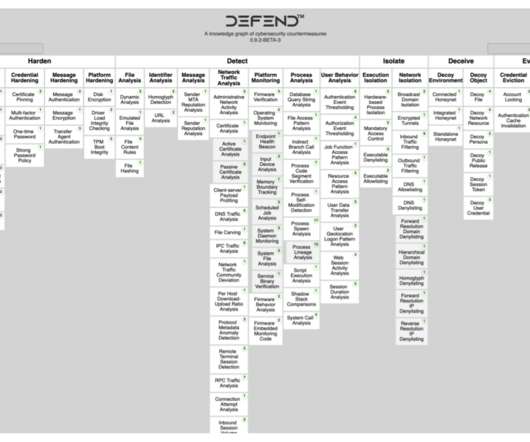
Industry and government use ATT&CK as a foundation to develop specific cyber threat models and methodologies.” MITRE experts also published a research paper that describes their study and development toward a precise, unambiguous, and information-dense knowledge graph of cybersecurity countermeasures.

Data Protection Report
JUNE 22, 2022
UK GDPR Reform: government publishes response to consultation – likely to form basis of forthcoming UK Data Reform Bill. The Department for Culture, Media and Sport (DCMS) has finally published the UK government’s long-awaited response to the consultation on the future of the UK data protection regime.

Security Affairs
MARCH 10, 2019
Ransomware threat makes the headlines again, this time an attack hit the computers of Jackson County, Georgia, paralyzing the government activity. Computers of Jackson County, Georgia, were infected with ransomware that paralyzed the government activity until officials decided to pay a $400,000 ransom to decrypt the files.

AIIM
AUGUST 31, 2021
This primary driver depends on other key transformative aspirations such as 2) business agility/innovation, 3) operational excellence, and 4) automated compliance/governance. eForms - Adopt and Create Digital Forms: Paper forms are still prevalent in many organizations. These drivers require information – in a leverageable form.

Security Affairs
MARCH 31, 2019
Paper Copy. LUCKY ELEPHANT campaign targets South Asian governments. Exodus, a government malware that infected innocent victims. A new round of the weekly SecurityAffairs newsletter arrived! The best news of the week with Security Affairs. Kindle Edition. Once again thank you! Malware Static Analysis.

DLA Piper Privacy Matters
JANUARY 27, 2022
The government has announced that it is launching the International Data Transfer Expert Council ( ‘the Council ‘). The government has already outlined the first territories which it will prioritise for its data transfer adequacy decisions.
Krebs on Security
DECEMBER 11, 2024
The Russian government’s embrace of cryptocurrency was a remarkable pivot: Bloomberg notes that as recently as January 2022, just weeks before Russia’s full-scale invasion of Ukraine, the central bank proposed a blanket ban on the use and creation of cryptocurrencies. So much business acumen at such a young age! ”

Data Protection Report
OCTOBER 27, 2023
The summit will bring together representatives from large lab AI companies, world governments and civil society to discuss safety risks arising from frontier AI. It will publish research on these risks so that governments can make appropriate regulatory policy responses. The key policy issues are: How do you regulate AGI?

AIIM
FEBRUARY 11, 2021
But, it’s not just a change from paper to digital that’s driving the momentum for Electronic Records Management (ERM). With any paper?based Sharing Records: ERM systems allow several users to read a record at once, whereas with paper records, only one person can. A business without its records typically cannot survive.

IG Guru
JULY 7, 2022
The post Modernizing Mahoning: Thousands of paper land records to be digitized via Vindy.com appeared first on IG GURU. Check out the article here.

AIIM
JULY 1, 2019
Utilizing a content management tool has helped them eliminate the time-consuming burden of pulling paper files manually and instead utilize automation so that Melissa and her team can do their jobs better. “[Our Yet, today there are many other counties in the US still struggling with manual processes and paper files.

Hunton Privacy
JUNE 21, 2022
On June 10, 2022, the Centre for Information Policy Leadership at Hunton Andrews Kurth published a white paper entitled “ Local Law Assessments and Online Services – Refining the Approach to Beneficial and Privacy-Protective Cross-Border Data Flows A: Case Study from British Columbia.”

AIIM
MAY 6, 2020
This is particularly important in government, financial services, utility, and legal sectors. We’re taking this discussion on the Digital Mailroom live during our FREE webinar, Cut Paper Mail Off at the Pass - How Digital Mailroom Services Transform Your Organization to the New Normal of Remote Working.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content