The Family That Mined the Pentagon's Data for Profit
WIRED Threat Level
AUGUST 18, 2022
The Freedom of Information Act helps Americans learn what the government is up to. The Poseys exploited it—and became unlikely defenders of transparency.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

WIRED Threat Level
AUGUST 18, 2022
The Freedom of Information Act helps Americans learn what the government is up to. The Poseys exploited it—and became unlikely defenders of transparency.

Security Affairs
APRIL 26, 2024
Indeed, while anonymity provides privacy and security for transactions, it can also be exploited by criminals for illicit activities, such as money laundering , drug trafficking, illegal arms sales, and terrorist financing. Compromised websites and malware are often at the root of these types of attacks.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
DECEMBER 21, 2018
2018 was the year of the Internet of Things (IoT) – massive attacks and various botnets, a leap in regulation and standards, and increased adoption of IoT devices by consumers and enterprises, despite the existence of security and privacy concerns. Insights from VDOO’s leadership. 2019 will continue these trends but at a faster pace.

Security Affairs
OCTOBER 9, 2024
Another important aspect is whether the collected user input will be retained for further training and whether such data will later be sanitized to minimize the disclosure of PII (Personally Identifiable Information) and other data that may impact user privacy in the event of a breach.

The Last Watchdog
JANUARY 11, 2022
The blue-sky mission is to bring modern data mining and machine learning technologies to bear delivering personalized services that ameliorate not just physical ailments, but also mental and even emotional ones. Fixing data governance. Yet robust data governance is still not uniformly practiced across the healthcare industry.

The Last Watchdog
SEPTEMBER 14, 2018
It’s easy to think of it as a problem the federal government must address or something that enterprises deal with, but cybersecurity has to be addressed closer to home, as well. His company supplies a co-managed SIEM service to mid-sized and large enterprises, including local government agencies. I spoke to A.N. Election threat.

The Last Watchdog
JANUARY 28, 2019
Related: Long run damage of 35-day government shutdown. The end game for this particular hacking ring is to install crypto currency mining routines on compromised Linux servers. Each of us have a responsibility to embrace best privacy and security practices. Targeting one device.

Schneier on Security
NOVEMBER 9, 2018
Many sets of data, both research and grey, fall outside privacy regulations such as HIPAA, FERPA, and PII. Commercial entities are besieging universities with requests for access to data or for partnerships to mine them.

The Guardian Data Protection
APRIL 12, 2020
Palantir, the US big data firm founded by the rightwing billionaire Peter Thiel, is working with Faculty, a British artificial intelligence startup, to consolidate government databases and help ministers and officials respond to the pandemic. The NHS declined to say which companies had offered the location data or how it would be used.

The Last Watchdog
FEBRUARY 6, 2019
We’re just a month and change into the new year, and already there have been two notable developments underscoring the fact that some big privacy and civil liberties questions need to be addressed before continuing the wide-scale deployment of advanced facial recognition systems. Related: Snowden on unrestrained surveillance.

Gimmal
NOVEMBER 7, 2024
In the rapidly evolving digital landscape, information governance has become more critical than ever. Emerging technologies, regulatory changes, and shifting business models are reshaping how we approach information governance. We’ll also highlight how Gimmal’s innovative solutions can help navigate this complex terrain.
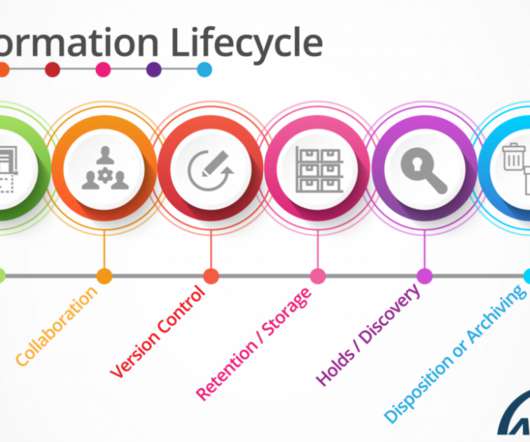
The Texas Record
JUNE 28, 2021
In a nutshell, this is information governance. ARMA defines “information governance” as “the overarching and coordinating strategy for all organizational information. But how is information governance any different than records management? ” That sounds great! The Records Lifecycle. Extra Phases.

The Last Watchdog
FEBRUARY 20, 2019
When Facebook founder Mark Zuckerberg infamously declared that privacy “is no longer a social norm” in 2010, he was merely parroting a corporate imperative that Google had long since established. But what if companies chose to respect an individual’s right to privacy, especially when he or she goes online? Privacy as good business.
ARMA International
DECEMBER 23, 2019
Follow this trajectory and you’ll push the envelope toward information governance (IG) and position yourself as a Very Important Person in your enterprise. That’s no coincidence because the tenets of records management are encompassed within IG (along with legal, privacy, risk/compliance, security, technology, etc.). 3 … 2 … 1 ….

IT Governance
FEBRUARY 1, 2018
This week, we discuss the Australian government’s loss of thousands of classified documents, DCMS Secretary of State Matt Hancock’s buggy new app and the growing trend of cybercriminals using cryptocurrency miners. Hello and welcome to the IT Governance podcast for Friday, 2 February 2018. Here are this week’s stories.

Krebs on Security
JUNE 18, 2021
Aside from its core business competency — checking to make sure the property at issue in any real estate transaction is unencumbered by any liens or other legal claims against it — First American basically has one job: Protect the privacy and security of all these documents. “That’s a high-risk vulnerability.

Security Affairs
FEBRUARY 2, 2020
The Russian government has already blocked the p rofessional social network L inkedIn in 2016 under the data-localization legislation. This week the Russian government has blocked the ProtonMail end-to-end encrypted email service and ProtonVPN VPN service. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->.

Security Affairs
SEPTEMBER 20, 2018
Everybody knows Monero cryptocurrency and probably everybody knows that it has built upon privacy, by meaning It’s not that simple to figure out Monero wallet balance. In this scenario, it is used to make money at the expense of computer users by abusing the infected computer to mine Monero, a cryptocurrency. XMRIG prove 1.

John Battelle's Searchblog
JANUARY 25, 2019
My current work is split between two projects: One has to do with data governance, the other political media. Big data, data breaches, data mining, data science…Today, we’re all about the data. And second… Governance. But Governance? Data Governance. We’ll start with Governance.

IG Guru
NOVEMBER 21, 2019
The post Here’s why LinkedIn is a ‘gold mine’ for foreign spies digging for corporate and government secrets via CNBC appeared first on IG GURU. A great article about how information can be used for nefarious purposes on LinkedIn.

IT Governance
DECEMBER 11, 2023
UK Information Commissioner warns about data privacy when using AI On 6 December, the UK Information Commissioner, John Edwards, told techUK’s Digital Ethics Summit 2023 that developers must embed privacy in their products to maintain consumer trust. The protected health information of up to 34,862 people was compromised.

The Last Watchdog
NOVEMBER 4, 2019
Jeff Bezos of Amazon, and Larry Page and Sergey Brin of Google did more than anyone else to actualize digital commerce as we’re experiencing it today – including its dark underbelly of ever-rising threats to privacy and cybersecurity. It very well could take us to improved privacy and cybersecurity. How often does that happen today?
Krebs on Security
DECEMBER 29, 2022
You just knew 2022 was going to be The Year of Crypto Grift when two of the world’s most popular antivirus makers — Norton and Avira — kicked things off by installing cryptocurrency mining programs on customer computers. Twitter acknowledges that it was relieved of phone numbers and email addresses for 5.4 million users.

eSecurity Planet
NOVEMBER 18, 2022
He has “worked around the clock” to secure assets, identify crypto on the blockchain , find records, and work with regulators and government authorities. One way is through hijacking computer resources to mine cryptocurrencies. where there is now a divided government, there may actually not be much action for the next few years.

The Last Watchdog
MARCH 17, 2020
And he explained how advanced encryption technologies, like MPC and homomorphic encryption, are on the cusp of enabling much higher use of the mountains of data hoarded in cloud storage by companies and governments. This would comply with data privacy regulations, like Europe’s GDPR and California’s CPPA.

AIIM
DECEMBER 20, 2017
I want a new football game and football because my little brother always tries to steal mine. Information Governance resides with Records management personnel who have not moved with the times and upgraded their skills.”. “It Information governance overall is not well understood or embraced as a broad discipline. Dear Santa.

Data Matters
MAY 4, 2021
Many companies hope to benefit from amassing large amounts of data by mining it for market insights, creating internal business models, and supporting strategic, data-driven decisions. Done properly, data de-identification can minimize risks to privacy interests—e.g., litigation discovery obligations. VIEW ARTICLE.

Hunton Privacy
DECEMBER 19, 2013
surveillance efforts, which range from defending national security to protecting the right to privacy to strengthening strategic alliances with other countries. The report begins by describing the varying goals of U.S. The report then details 46 recommendations designed to balance these goals.

eSecurity Planet
JANUARY 21, 2021
Governance, risk, and compliance (GRC) software helps businesses manage all of the necessary documentation and processes for ensuring maximum productivity and preparedness. Third-party governance. Like other competitive GRC solutions, it speeds the process of aggregating and mining data, building reports, and managing files.

IT Governance
FEBRUARY 6, 2024
Enforcement Uber fined €10 million for GDPR breaches The Dutch data protection authority, Autoriteit Persoonsgegevens, has fined Uber €10 million for failing to be transparent about its data retention practices and making it difficult for drivers to exercise their data privacy rights. Key dates 31 March 2024 – PCI DSS v4.0 of the Standard.

Data Protection Report
JUNE 27, 2018
United States, holding that the federal government needs a warrant to access cellphone location records. At issue in Carpenter was the government’s warrantless collection of historical cellphone location records. The Court disagreed with the government and sided with Carpenter.

IT Governance
JANUARY 9, 2024
noyb files complaint with Austrian data protection authority against creditors’ association The privacy rights campaign group noyb has filed a complaint against the creditors’ association KSV1870 for charging data subjects to access their personal data, in contravention with Article 15 of the EU GDPR.

OpenText Information Management
OCTOBER 31, 2024
Establishing comprehensive data governance frameworks, including automated data profiling and validation processes, can significantly enhance data quality and support more accurate analytics. These issues undermine the reliability of analytics and AI models, leading to misinformed decisions and lost opportunities.

John Battelle's Searchblog
MAY 25, 2018
It’s more likely than not that any reader of mine already knows all about GDPR, but for those who don’t, it’s the most significant new framework for data regulation in recent history. Our privacy and our “right to be left alone” are in peril.

IT Governance
FEBRUARY 22, 2018
This week, we discuss new reports from Cisco, McAfee and the CSIS, and Big Brother Watch, and hear more about malicious Monero mining. Hello and welcome to the IT Governance podcast for Friday, 23 February 2018. I neglected to reveal the sum the criminals managed to mine in the few hours before they were detected.

eSecurity Planet
AUGUST 11, 2022
A data governance manager will intensely focus on the access, transmission, and storage of data, but an IT security manager must have a broader perspective that encompasses the infrastructure and tools. Privacy categories (subcategories of Semantic categories) Direct identifiers (name, social security number, etc.) Data Lake Controls.

Troy Hunt
MARCH 2, 2020
I hate to be vague (I'm usually super transparent on these things), but I'd also hate to disrespect the privacy of this organisation or land myself in hot water legally. A Lot Happens in 11 Months I onboarded 5 new governments onto HIBP: Austria, Ireland, Norway, Switzerland and Denmark (and a 6th one about to be announced any day now).

The Security Ledger
DECEMBER 18, 2019
In this Spotlight edition of The Security Ledger podcast, sponsored by RSA Security, the Chief Privacy Officer at Nemours Healthcare, Kevin Haynes, joins us to talk about the fast evolving privacy demands on healthcare firms and how the Chief Privacy Officer role is evolving to address new privacy and security threats.

erwin
JUNE 11, 2020
With tools such as Artificial Intelligence, Machine Learning, and Data Mining, businesses and organizations can collate and analyze large amounts of data reliably and more efficiently. As exponential amounts of data will be consumed and processed, quality data governance and management will be essential. Data quality management.

eSecurity Planet
JANUARY 21, 2021
Governance, risk, and compliance (GRC) software helps businesses manage all of the necessary documentation and processes for ensuring maximum productivity and preparedness. Third-party governance. Like other competitive GRC solutions, it speeds the process of aggregating and mining data, building reports, and managing files.

Adam Levin
AUGUST 12, 2019
It highlights the general lack of privacy laws out there, and may herald the start of meaningful legislation. While many were alarmed by the specter of Russia owning pictures of them and the privacy implications that went with that set of affairs, the bigger picture got lost in the scramble. There Ought to Be A Law. Ron Wyden said.

Info Source
MAY 25, 2018
Today he practices in the areas of regulatory litigation, including cybersecurity and data breaches, privacy and telecommunications, civil and criminal enforcement proceedings and international Regulatory Compliance. “If I am not covered by GDPR I don’t have to update my Privacy Policy.

IBM Big Data Hub
OCTOBER 30, 2023
In today’s digital age where data stands as a prized asset, generative AI serves as the transformative tool to mine its potential. Adopting AI in business at scale is not without its challenges, including data privacy concerns, integration complexities and the need for skilled personnel.

Information is Currency
FEBRUARY 17, 2017
Companies Still Struggle With Information Governance, Survey Finds. Despite years of talking about information governance and compliance, less than half of companies surveyed have a compliance culture — and many companies apparently have no governance strategy at all. The Need for Information Governance Has Never Been Greater.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content