US CISA published a guide to better use the MITRE ATT&CK framework
Security Affairs
JUNE 5, 2021
In 2018, MITRE announced the MITRE ATT&CK , a globally accessible knowledge base of adversary tactics and techniques based on real-world observations.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Security Affairs
JUNE 5, 2021
In 2018, MITRE announced the MITRE ATT&CK , a globally accessible knowledge base of adversary tactics and techniques based on real-world observations.
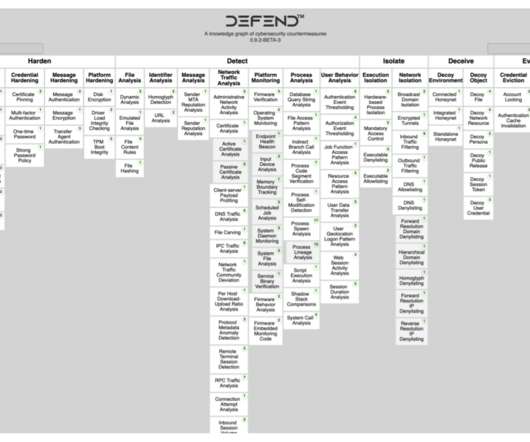
Security Affairs
JUNE 23, 2021
“D3FEND is a knowledge base, but more specifically a knowledge graph, of cybersecurity countermeasure techniques. “MITRE released D3FEND as a complement to its existing ATT&CK framework, a free, globally-accessible knowledge base of cyber adversary tactics and techniques based on real-world observations.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
JUNE 17, 2019
New Report Calls for Other Methods of Authentication at Federal Agencies Some federal agencies inappropriately continue to rely on knowledge-based authentication to prevent fraud and abuse even though this method is no longer trustworthy because so much personal information that's been breached is readily available to fraudsters, a new U.S.

Security Affairs
FEBRUARY 1, 2024
The government agency recommends continuing to look for indicators of compromise on any systems connected to—or recently connected to—the affected Ivanti device. Ivanti will update this knowledge base article as more information becomes available.” ” reads the directive. reads the advisory. “Be 20240126.5.xml”

Security Affairs
AUGUST 26, 2021
DIVD Chairman Victor Gevers told BleepingComputer that the advisory was originally shared with 68 government CERTs under a coordinated disclosure, but became public after one of them shared it with an organization’s service desk operating in the Financial Services. An employee published the alert on an online analyzing platform.
Krebs on Security
JULY 4, 2020
But KrebsOnSecurity recently discovered that this is not the case with all federal government sites built to help you manage your identity online. Password reset questions selected, the site proceeded to ask four, multiple-guess “knowledge-based authentication” questions to verify my identity.

Security Affairs
AUGUST 3, 2023
noarch.rpm as per the Ivanti Knowledge Base article 000087042.” revealed that zero-day flaws in EPMM, tracked CVE-2023-35078 and CVE-2023-35081 , were exploited by threat actors in recent attacks against the ICT platform used by twelve ministries of the Norwegian government. ” continues Rapid7.

AIIM
APRIL 8, 2021
It serves in many ways to apply a formal governance framework to the document creation and collaborative editing processes. When the knowledge base grows, it quickly makes finding specific documents a challenge. Do your employees need to upload and download documents? Do they need to be able to do this anywhere?

Info Source
JANUARY 30, 2025
For context, this is how I define RAG in the context of IDP: RAG is an advanced AI methodology that enhances the capabilities of large language models (LLMs) by integrating knowledge bases. Cost Efficiency : By leveraging RAG, organisations can avoid the high costs associated with retraining LLMs for domain-specific use cases.
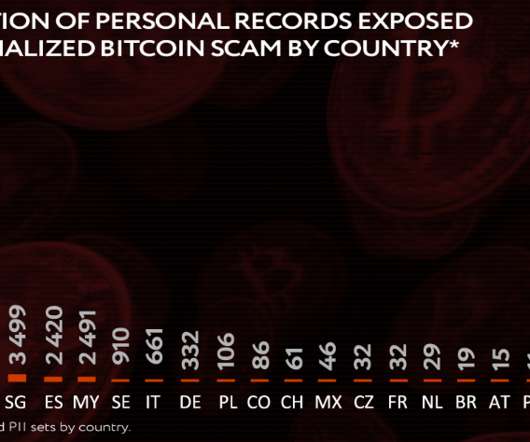
Security Affairs
JUNE 30, 2020
The Singapore government has also launched the Do Not Call registry under the PDPA for consumers who do not wish to receive telemarketing messages via phone call, SMS or fax. A couple of simple rules: If you spot a long redirect chain, it’s a red flag. However, regular users are not the only ones who suffer here. About Group-IB.

AIIM
AUGUST 26, 2021
However, you can establish a more intelligent semantic layer to your search parameters by using this knowledge base to further classify the ingested content, enrich the search functionality and results, and bring more depth and speed to the search process overall. Do this by “sifting and aggregating” what you find.

IT Governance
MARCH 2, 2023
Due to go live in the next few months, this guidance will include articles explaining assessment questions, as well as a dedicated knowledge base. IT Governance is one of the founding Cyber Essentials certification bodies and remains one of the largest in the UK.

Hunton Privacy
SEPTEMBER 10, 2020
The bill would explicitly permit businesses to require the parent or guardian to implement any of the below measures for purposes of ensuring the person providing consent is the parent or legal guardian of the California Child: Sign and send a consent form via fax, U.S.

OpenText Information Management
MARCH 31, 2025
Key enhancements include: OpenText Service Management and OpenText Core Content Management integration , which enhances service agents' access to information while ensuring data governance. OpenText IT Operations Aviator integrates custom knowledge bases, offering rapid insights for issue resolution across your IT landscape.

The Last Watchdog
MARCH 7, 2024
By eliminating passwords and stored secrets, Badge bolsters Radiant Logic’s extensible identity data platform to accelerate strategic initiatives such as digital transformation, Zero Trust, automated compliance, and data-driven governance. This sets the stage for a more connected and secure online future for everyone.”

ChiefTech
SEPTEMBER 27, 2012
This year, Pleio, a customised version of Elgg developed by the Dutch government , also won an award. Pleio: A social network for Dutch government on Prezi. Incidentally, an award winning Headshift Asia Pacific client that is based on Elgg also presented at Step Two's intranet conference earlier this year (PDF).

The Texas Record
SEPTEMBER 30, 2019
In this article, we’ll be discussing four of the most common RM certificates and certifications: the Local Government Archives and Records Administration certificate (LGARA), the Certified Records Manager (CRM), the Certified Records Analyst (CRA), and the Information Governance Professional (IGP). LGARA Certificate Program.
Collibra
APRIL 10, 2024
Collibra Data Notebook: Query and collaborate around data Introducing Collibra Data Notebook: a tool enabling you to query and gain additional insights into your data — directly within your governed Collibra environment.

eSecurity Planet
SEPTEMBER 16, 2022
Finally, it also is useful for companies looking for a governance, risk, compliance ( GRC ) solution. Government organizations are arguably the most at risk of fraud attempts. According to FTC findings in 2019, government impostor fraud was the most-reported type of fraud. million in losses. Want to learn more?

Collibra
FEBRUARY 21, 2024
More importantly, it lays a foundation for data governance and data quality that can fuel your organization with the trusted data that drives decision-making. Such initiatives not only build a common knowledge base but also demonstrate the organization’s commitment to supporting its teams through the transition.

Collibra
SEPTEMBER 16, 2022
Your organization can also leverage Data Governance to standardize the management of data assets and improve their quality. . Overseeing data governance and managing metadata are also part of their responsibility. A key recommendation from Gartner is to give business users the ability to flag and address quality problems.

IBM Big Data Hub
AUGUST 22, 2023
We leverage retrieval-augmented generation tasks to create a question-answer feature or multi-lingual conversational chatbot (based on a documents or dynamic content from a broad knowledge base) that provides field service assistance in real time.

Hunton Privacy
JANUARY 10, 2014
In its letter to Imperium , the FTC stated that Imperium’s method of knowledge-based authentication (“KBA”) is an acceptable method of obtaining verifiable parental consent as it is “reasonably calculated. to ensure that the person providing consent is the child’s parent.” View the FTC’s letter to Imperium.

DLA Piper Privacy Matters
APRIL 26, 2021
It is based on the OECD’s 2019 Recommendation on Artificial Intelligence and covers: Software ; Developed with one or more of the specified techniques and approaches in Annex I to the AI Regulation (which the Commission can amend over time through delegated acts). Governance, enforcements and sanctions .

Troy Hunt
NOVEMBER 21, 2017
It's an amazing opportunity to influence decision makers at the highest levels of government and frankly, I don't want to stuff it up which is why I'm asking the question - what should I say? For a bit more context, I've been chatting with folks from the House Energy and Commerce Committee for a while now about the mechanics of data breaches.

OpenText Information Management
MARCH 5, 2025
Enterprise Scan upload approvals: Documents scanned via Enterprise Scan now adhere to Smart Document Type approval workflows, maintaining content governance. From Smart View optimizations and AI-driven workflows to advanced governance and security features, this release supports organizations in managing their content more effectively.

IBM Big Data Hub
AUGUST 2, 2023
However, through the implementation of NLP and business knowledge bases in chatbots, automated responses to the frequently asked questions (FAQS) can be deployed quickly. Watson has solved the problems of business owners across a variety of industries, including banking, retail, government, insurance, and healthcare.

eSecurity Planet
SEPTEMBER 26, 2024
While SurfShark is headquartered in the Netherlands, a Nine Eyes member (potentially required to pass personal data to the government), it has a strict no-logging privacy policy for customers. Surfshark has a significant amount of help articles in its customer knowledge base. The VPN runs on Windows, Mac, and Linux computers.

IBM Big Data Hub
APRIL 4, 2024
BPM also provides agents with access to a centralized knowledge base and customer history, enabling them to resolve inquiries more efficiently and effectively. Workflows can be established that govern the movement of goods from supplier to customer. This accelerates time-to-market and reduces development costs.

IBM Big Data Hub
OCTOBER 25, 2023
It can improve IT automation by building and executing runbooks and helping users transition to new knowledge bases and software. Data availability and governance factors are also considerations when assessing ROI. Much more can be said about IT operations as a foundation of modernization.

Collibra
JULY 13, 2021
Your organization can also leverage Data Governance to standardize the management of data assets and improve their quality. . Overseeing data governance and managing metadata are also part of their responsibility. A key recommendation from Gartner is to give business users the ability to flag and address quality problems.

IBM Big Data Hub
JULY 17, 2023
Question & Answering : Based on a set of documents or dynamic content, create a question-answering feature grounded on product specific content, such as building a Q&A resource from a broad knowledge base to provide customer service assistance. ” Vitaly Tsivin, EVP Business Intelligence at AMC Networks.

CGI
JULY 2, 2018
The Modernizing Government Technology (MGT) Act (2017), which encourages CIOs to establish IT working capital funds to drive savings from operational efficiency and new IT investments. A government-wide fund may be used as an IT investment loan.

eSecurity Planet
JULY 12, 2023
Committed to bringing prospective buyers knowledge before they commit, Trend Micro is one of the few CSPM vendors that offers a complimentary public cloud risk assessment to anyone who wants additional guidance on security, governance, and compliance before building their cloud infrastructure in AWS or Azure.

CGI
DECEMBER 15, 2015
Making effective use of big data has become a top priority for commercial and government organizations. Throughout the book, we share our knowledge based on the experiences of the 5,000 CGI professionals who work with clients on data and analytics initiatives every day. Sharing best practices in our new Data to Diamonds book.

IBM Big Data Hub
JANUARY 18, 2024
This consistency, derived from the knowledge base, helps to maintain brand integrity and accuracy in customer communications. Government Empower citizens to access basic information on paying bills and upcoming events by using chatbots.

Collibra
AUGUST 18, 2022
Public Policy Disclosure and Internal Privacy Process : Organizations must “publish on its website governance rules regarding personal information.” The flexibility of Collibra enables you to operationalize the exact governance model with appropriate role labels that will enable your business to truly adopt and leverage the platform.

Collaboration 2.0
AUGUST 12, 2008
Parallax, a novel browsing interface designed by David Huynh to manipulate Freebase , shows how contextual connections can be made with machine readable data to provide a much richer results set which in turn can spawn fascinating visual representations, and more.

eDiscovery Daily
MAY 20, 2024
To leverage LLMs reliably, pretraining must ensure world (refers to the accuracy of the AI’s responses based on real-world facts and information.) case (based on case data), and legal knowledge (based on general legal knowledge) accuracy. The correctness of responses depends on the data embedded in the LLM.

eDiscovery Daily
MARCH 27, 2018
What I would love to see is the ability for more interaction to capitalize on that knowledge base. Some of that goes back to the fact that information governance is not as prominent in every organization as it should be, or that those of us in this space would like to think that it should be. That varies by organization.

IBM Big Data Hub
JULY 19, 2023
Conversational Knowledge: Reviews, knowledge base, product descriptions and more. An AI generated sample narrative of adverse events In addition to this, IBM Consulting recently launched watsonx.data on AWS, an open, hybrid, governed data store to help enterprises scale analytics and AI.

CILIP
SEPTEMBER 8, 2021
We physically went out to capture the knowledge learnings in the oil fields of Oman. It was about getting project teams to share their learnings into a knowledge base from which we could then extrapolate key learnings with monetary value. I think Knowledge Managers should focus on the digital workspace, the collaborative thing.

IBM Big Data Hub
AUGUST 1, 2023
Organizations try to keep their IT infrastructure in good standing by using IT service management (ITSM) to govern the implementation, delivery and management of services that meet the needs of end users. How do incident management and problem management work together?

CILIP
FEBRUARY 7, 2020
Jisc is working on issues relating to the National Bibliographic Knowledge Base and the National Acquisitions Group are looking at the framework and Gavin expects to be working on how to meet their recommendations in a way that is workable for suppliers. ? t come from the government it comes from sources such as research grants.?
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content