Good Governance: 'It's All Hygiene'
Data Breach Today
NOVEMBER 30, 2023
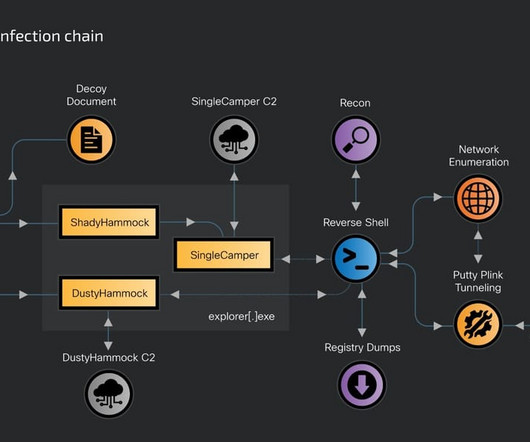
In the constant struggle to manage the other five pillars - identify, protect, detect, respond and recover - security leaders often do not have governance at top of mind, said Netography CEO Martin Roesch, but he added, "Good governance is the root of having good security."














































Let's personalize your content