Half of all Financial Services Cyber Attacks Start with a Very Costly Phish
KnowBe4
SEPTEMBER 23, 2024
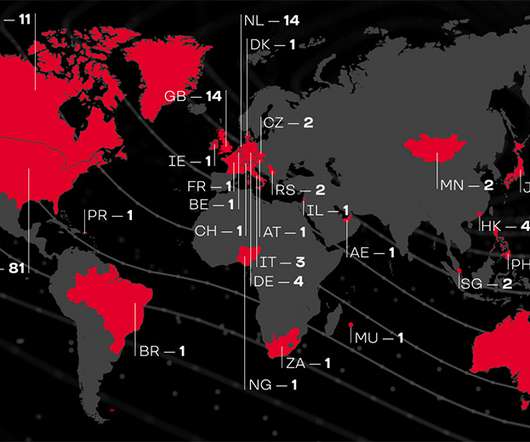
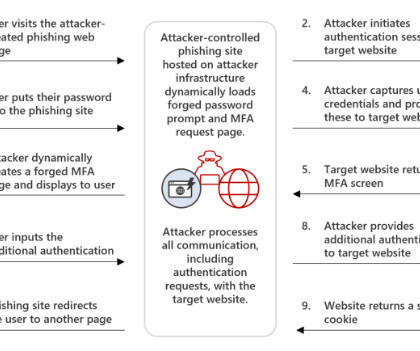
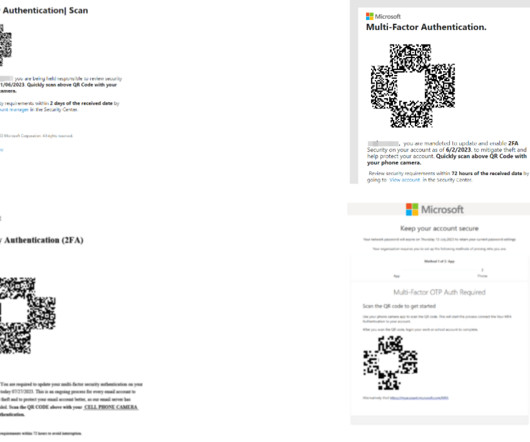
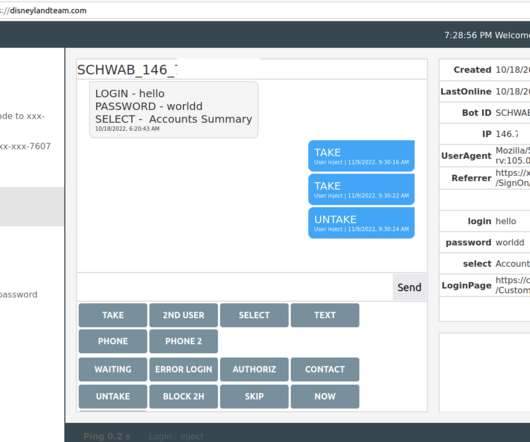
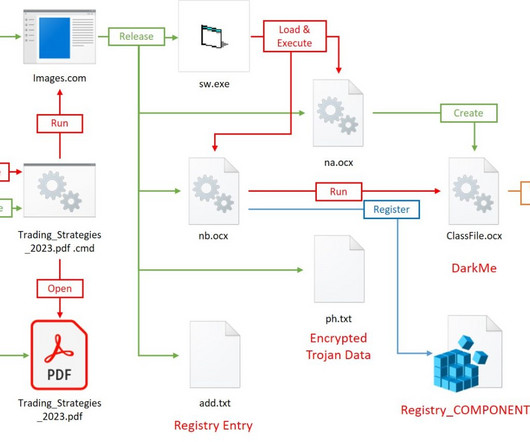
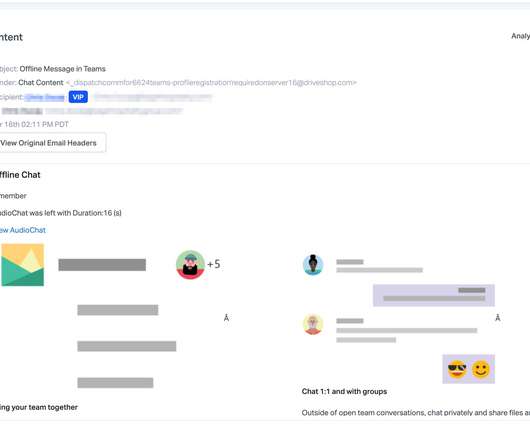
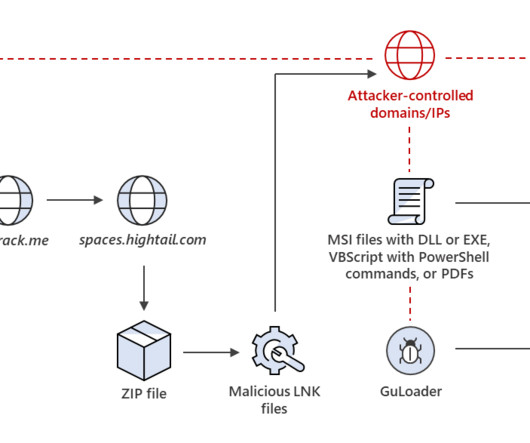
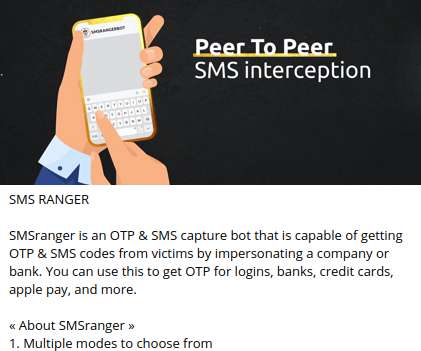
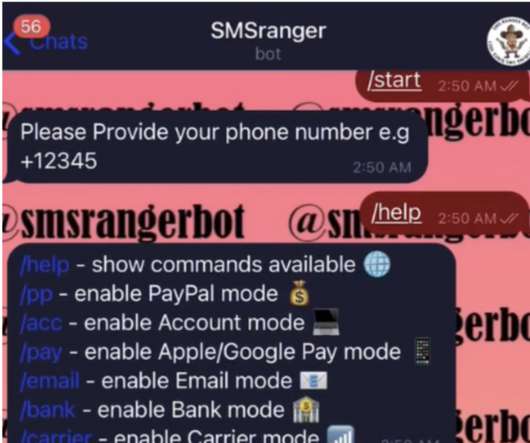
New analysis of attacks on the financial sector shows that the combination of phishing emails and compromised credentials is a recurring — and financially impactful — threat.









































Let's personalize your content