Designing Tabletop Exercises That Actually Thwart Attacks
Dark Reading
APRIL 4, 2023
Have you ever wondered how they design blue team exercises? One ransomware and cyber extortion simulation demonstrates the best practices.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Dark Reading
APRIL 4, 2023
Have you ever wondered how they design blue team exercises? One ransomware and cyber extortion simulation demonstrates the best practices.
Security Affairs
OCTOBER 13, 2023
FBI and CISA published a joint Cybersecurity Advisory (CSA) to disseminate IOCs, TTPs, and detection methods associated with AvosLocker ransomware. The joint Cybersecurity Advisory (CSA) is part of an ongoing #StopRansomware effort aimed at sharing technical details associated with various ransomware operations.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
APRIL 11, 2022
From financial institutions to meat producers, it seems every industry has been impacted by ransomware in the past year — maybe even the past week. Related: Tech solutions alone can’t stop ransomware. Put simply, ransomware attacks are on the rise because of profits. Why the stark increase? Low cost attacks.

Security Affairs
DECEMBER 13, 2023
A Joint Committee on the National Security Strategy (JCNSS) warns of the high risk of a catastrophic ransomware attack on the UK government. The British government is accused of failing to mitigate the risk of ransomware attacks. Beckett recommends the UK government consider defense from ransomware attacks a top political priority. “in

Krebs on Security
JULY 19, 2021
Browse the comments on virtually any story about a ransomware attack and you will almost surely encounter the view that the victim organization could have avoided paying their extortionists if only they’d had proper data backups. That’s why tabletop exercises are incredibly important.

KnowBe4
JUNE 1, 2022
The rise of Ransomware-as-a-Service has given rise to a number of more successful groups who have their “business” down to a simple exercise of playing the numbers.

Security Affairs
NOVEMBER 22, 2021
US CISA and the FBI issued a joint alert to warn critical infrastructure partners and public/private organizations of ransomware attacks during holidays. The Cybersecurity and Infrastructure Security Agency (CISA) and the FBI warn critical infrastructure partners of ransomware attacks during the holiday season. Pierluigi Paganini.

Dark Reading
JULY 19, 2023
The ransomware-as-a-service offering was first assumed to be a red-team exercise before being detected for true malicious activity.

Security Affairs
DECEMBER 5, 2021
German BSI warns of ransomware attacks over the Christmas and end-of-year holidays, fearing Emotet return and attacks on Microsoft Exchange servers. The German cybersecurity authority BSI warns of ransomware attacks over the Christmas holidays, fearing the return of the Emotet botnet return. ” reads the BSI’s alert.
Security Affairs
OCTOBER 17, 2023
What is the impact of ransomware on organizations? Based on Ransomlooker, a free Cybernews tool for monitoring the dark web and other hidden areas of the internet, 64% of organizations have already suffered from a ransomware attack. One employee’s mistake can cost a company millions of dollars.

The Last Watchdog
AUGUST 2, 2024
VECTR Enterprise is designed to support organizations that want to mature and communicate the success of their purple team exercises with benchmarking and executive reporting features. Premium testing content : The platform provides access to testing “Indexes” for AWS, Azure, AI, Ransomware, Linux, Mac, Kubernetes, and more.

Security Affairs
AUGUST 21, 2021
The US Cybersecurity and Infrastructure Security Agency (CISA) released guidance on how to prevent data breaches resulting from ransomware attacks. Over the past several years, government agencies and its partners have responded to a significant number of ransomware attacks, including recent attacks against Colonial Pipeline and and U.S.

eSecurity Planet
JUNE 30, 2021
Virtual machines are becoming an increasingly popular avenue cybercriminals are taking to distribute their ransomware payloads onto compromised corporate networks. In order to avoid raising suspicions or triggering antivirus software , the ransomware payload will ‘hide’ within a VM while encrypting files on the host computer.”

Security Affairs
OCTOBER 8, 2021
The Dutch government will not tolerate ransomware attacks that could threaten national security, it will use intelligence or military services to curb them. “For several years, the threat of ransomware attacks has been increasing around the world.

Thales Cloud Protection & Licensing
JUNE 14, 2022
Ransomware – To Pay, or Not to Pay? And when thinking about criminal innovation, ransomware attacks clearly fall into that definition of “disruptive”, especially for any business on the receiving end of that “innovation”. While ransomware attacks are not new, they remained largely underreported in the mainstream media for many years.

Hunton Privacy
JULY 12, 2021
On June 30, 2021, the New York State Department of Financial Services (“NYDFS,” the “Department”) issued guidance to all New York state regulated entities on ransomware (the “Guidance”), identifying controls it expects regulated companies to implement whenever possible.

Hunton Privacy
NOVEMBER 16, 2021
Department of the Treasury announced a bilateral cybersecurity partnership with the Israeli Ministry of Finance “to protect critical financial infrastructure and emerging technologies” and combat the use of ransomware. The initiative includes the launch of a U.S.-Israeli

Security Affairs
FEBRUARY 12, 2022
CISA, FBI and NSA published a joint advisory warning of ransomware attacks targeting critical infrastructure organizations. and Australia have published a joint advisory warning of an increased globalised threat of ransomware worldwide in 2021. Cybersecurity agencies from the U.K., ” reads the joint advisory.

The Last Watchdog
JANUARY 31, 2019
A report co-sponsored by Lloyd’s of London paints a chilling scenario for how a worldwide cyberattack could trigger economic losses of some $200 billion for companies and government agencies ill-equipped to deflect a very plausible ransomware attack designed to sweep across the globe. Related: U.S. cyber foes exploit government shutdown.

The Last Watchdog
AUGUST 1, 2023
To highlight ransomware precursors and how the attacks evade common cyber defenses, Lumu has also released an update to its 2023 Ransomware Flashcard.

The Last Watchdog
JULY 25, 2024
Will we also see a wave of ransomware attacks that follow? Ransomware uses endpoints and other attack vectors as their launch mechanism for their attack and you need layers of security over your critical data and file shares. Right now we are dealing with outages at airlines and other critical businesses. Time will tell.

Thales Cloud Protection & Licensing
NOVEMBER 24, 2020
Mitigating Ransomware Attacks – Decoupling Encryption Keys From Encrypted Data. While ransomware attacks have been around for decades, their frequency has exponentially increased in the last few years, let alone the past several months during the pandemic. The potency of a ransomware attack lies in its diabolical ingenuity.

Adam Levin
FEBRUARY 24, 2020
Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory following a ransomware attack on a natural gas compression facility. The threat actor then deployed commodity ransomware…on both networks,” adding that the facility was out of commission for two days. .

Thales Cloud Protection & Licensing
SEPTEMBER 30, 2021
Cybersecurity Awareness Month: The value of cyber hygiene in protecting your business from potential ransomware. Can good cyber hygiene protect us from ransomware? Ransomware attacks are on the rise and adversaries are developing more sophisticated cyberattacks. Thu, 09/30/2021 - 07:58. What are good cyber hygiene practices?

Security Affairs
JANUARY 13, 2024
Every week the best security articles from Security Affairs are free for you in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.

Thales Cloud Protection & Licensing
MAY 22, 2018
In 2016, I provided predictions in an article entitled The (Immediate) Future of Ransomware. I indicated ransomware was going to grow and find other vectors for infection outside of simply malware links. Ransomware Is About Numbers. Instead of ransomware going away, ransomware has actually increased by 750% since 2016.

Security Affairs
MAY 27, 2023
Is the BlackByte ransomware gang behind the City of Augusta attack? Every week the best security articles from Security Affairs are free for you in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.

Security Affairs
DECEMBER 17, 2023
CISA and ENISA enhance their Cooperation CISA adds Qlik bugs to exploited vulnerabilities catalog Report: 2.6 CISA and ENISA enhance their Cooperation CISA adds Qlik bugs to exploited vulnerabilities catalog Report: 2.6

eSecurity Planet
MAY 30, 2024
Ransomware attacks and data breaches make headlines when they shut down huge connected healthcare providers such as Ascension Healthcare or Change Healthcare. 2024 looks like it will only increase the number of affected individuals considering the scale of ransomware attacks from the first half of the year in the USA, Canada, and Australia.

Hunton Privacy
FEBRUARY 2, 2022
Attorney General Weiser also announced that, by this fall, his office will exercise its new rulemaking authority under the CPA to post a formal Notice of Proposed Rulemaking, including a proposed set of model rules. Lastly, it will examine the degree to which the company vets and monitors its vendors’ data security practices.

eSecurity Planet
OCTOBER 24, 2023
Exercise Caution with Emails The first two items on this list could be lumped together with a single warning: Don’t click. Watch File Extensions: Exercise caution with file extensions; avoid files with suspicious extensions like.exe or.bat, especially from unfamiliar sources.

Security Affairs
AUGUST 27, 2023
military procurement system Spoofing an Apple device and tricking users into sharing sensitive data Israel and US to Invest $3.85 Million in projects for critical infrastructure protection through the BIRD Cyber Program N. military procurement system Spoofing an Apple device and tricking users into sharing sensitive data Israel and US to Invest $3.85

ForAllSecure
MAY 30, 2023
Say you’re an organization that’s been hit with ransomware. At what point do you need to bring in a ransomware negotiator? Mark Lance, the VP of DFIR and Threat intelligence for GuidePoint Security, provides The Hacker Mind with stories of ransomware cases he’s handled. The same is true with ransomware.

The Last Watchdog
FEBRUARY 21, 2022
The headlines are disturbing: Breach of patient records ; Surgeries and appointments cancelled due to IT outage ; and even, Death attributed to ransomware attack on hospital. One example of this is isolating or quarantining systems with malware (virus or ransomware) from the remainder of the network.

The Last Watchdog
OCTOBER 9, 2019
That’s the dilemma hundreds of organizations caught in the continuing surge of crippling ransomware attacks have faced. Related: How ransomware became such a scourge The FBI discourages it, as you might have guessed. That pay or not to pay debate aside, there’s a more central question raised by the ransomware plague.

Security Affairs
AUGUST 31, 2023
Also, the credentials could have been used to gain initial access into corporate networks to deploy ransomware, steal or sabotage internal documents, or gain access to user data. It’s advisable for them to externally verify the information contained in emails and exercise caution when clicking links or opening attachments.

Security Affairs
FEBRUARY 26, 2023
If you want to also receive for free the newsletter with the international press subscribe here.

eSecurity Planet
MARCH 22, 2022
Companies should also regularly test their defenses and hold tabletop exercises with their various IT business units.” Ransomware in Focus. The law directs CISA to deploy a ransomware vulnerability warning program to identify information systems that contain security vulnerabilities. Trade Cyberthreats.

eSecurity Planet
FEBRUARY 26, 2024
Furthermore, threat actors use the authentication bypass issue to spread LockBit ransomware on infiltrated networks, specifically targeting vulnerable ScreenConnect servers. The problem: LockBit ransomware, formerly known as “ABCD” ransomware, has gained traction in recent months as a separate threat in the extortion tool market.

Thales Cloud Protection & Licensing
MARCH 29, 2023
Exercising the principle of least privilege is always recommended: every user, app, program, and device should be able to access only the areas and data that are necessary for their function. Backup Data Backing up your data is the number one most effective method of protecting against ransomware, by a long shot.

Hunton Privacy
NOVEMBER 23, 2022
The proposed amendments provides three new cybersecurity events that Covered Entities must report to NYDFS via the NYDFS online cybersecurity portal within 72 hours: Unauthorized access to privileged accounts; Deployment of ransomware within a material part of the Covered Entity’s systems; and.
Security Affairs
SEPTEMBER 6, 2021
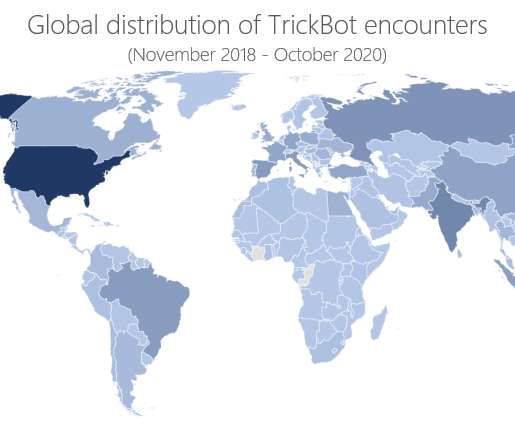
Threat actors leverage the botnet to distribute a broad range of malware including info-stealer and ransomware such as Conti and Ryuk. “If you send him to the United States, it will be very difficult to exercise your right of defense and there is a high possibility that you will be subjected to excessive punishment.”

Security Affairs
MAY 6, 2023
Twitter confirmed that a security incident publicly exposed Circle tweets FBI seized other domains used by the shadow eBook library Z-Library WordPress Advanced Custom Fields plugin XSS exposes +2M sites to attacks Fortinet fixed two severe issues in FortiADC and FortiOS Pro-Russia group NoName took down multiple France sites, including the French (..)

IBM Big Data Hub
JULY 19, 2023
According to an IBM Security X-Force study , the time to execute ransomware attacks dropped by 94% over the last few years—with attackers moving faster. The importance of red teaming By conducting red-teaming exercises, your organization can see how well your defenses would withstand a real-world cyberattack.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content