Military Exercises Trigger Russian DDoS Attacks on Japan
Data Breach Today
OCTOBER 18, 2024
Russian Actors Disrupt Websites of Political Party, Business and Government Groups Plans by Japan and U.S.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Data Breach Today
OCTOBER 18, 2024
Russian Actors Disrupt Websites of Political Party, Business and Government Groups Plans by Japan and U.S.

Security Affairs
AUGUST 20, 2023
-South Korea military exercise. The military drill, the Ulchi Freedom Guardian summer exercises , will start on Monday, August 21, 2023 , and will last 11 days. The military exercises aim at improving the ability of the two armies to respond to North Korea’s evolving nuclear and missile threats.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
FEBRUARY 24, 2023
Defence Cyber Marvel 2 (DCM2) is the largest Western Europe-led cyber exercise that took place in Tallinn with 34 teams from 11 countries. This year, 750 cyber specialists have participated in the military cyberwarfare exercise. ” reads the press release published by the UK Ministry of Defence. .
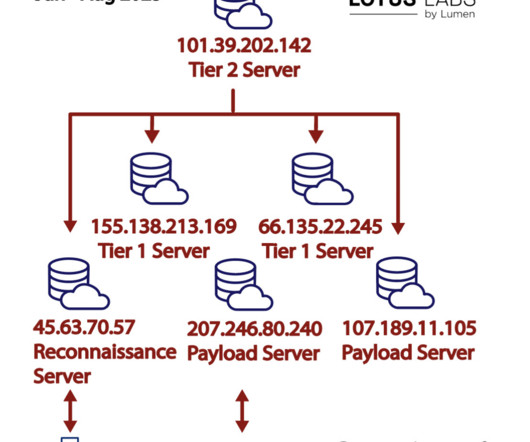
Security Affairs
AUGUST 21, 2023
military procurement system. military procurement system and was spotted targeting Taiwan-based organizations The choice of the new targets in the latest campaign suggests a strategic interest of the People’s Republic of China according to the 2023 ODNI threat assessment. military server used for contract proposals and submissions.

Security Affairs
MAY 14, 2022
Our Legion conducts military cyber exercises in your countries in order to improve their skills. The post Pro-Russian hacktivists target Italy government websites appeared first on Security Affairs. Killnet published a message on its Telegram channel, threatening further attacks may: “Dear media of Italy and Spain.
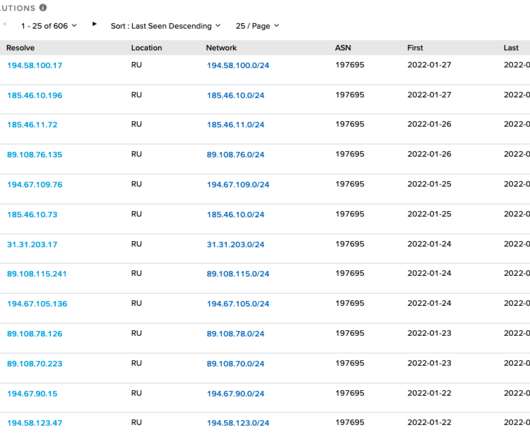
Security Affairs
FEBRUARY 4, 2022
The Russia-linked Gamaredon APT group attempted to compromise an unnamed Western government entity in Ukraine. In Mid January the Ukrainian government was hit with destructive malware, tracked as WhisperGate , and several Ukrainian government websites were defaced by exploiting a separate vulnerability in OctoberCMS.

Security Affairs
OCTOBER 8, 2021
The Dutch government will not tolerate ransomware attacks that could threaten national security, it will use intelligence or military services to curb them. The Dutch government announced that it will not tolerate cyberattacks that pose a risk to its national security and will employ intelligence or military services to counter them.
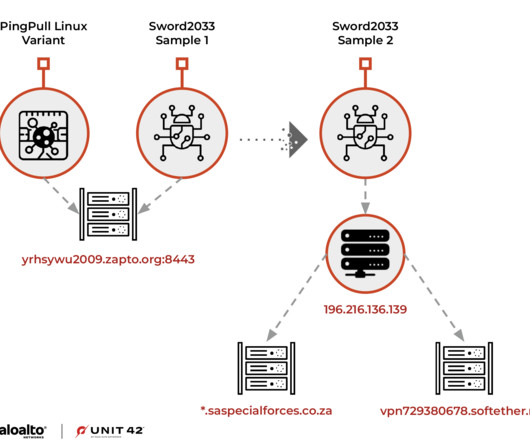
Security Affairs
APRIL 26, 2023
In recent years, the researchers observed the group expanding its operations to include financial institutions and government entities. This domain has been hosted on eight other IPs throughout its history, none of these IPs were directly affiliated with the South African government. Experts added that the IP 196.216.136[.]139
Security Affairs
DECEMBER 30, 2019
Open Media pointed out that that Windows XP is the last operating system developed by Microsoft that was approved by the Kremlin for use on official Russian government computers. Microsoft Windows 10 is only allowed only for government systems that don’t manage secret information. ” reads the post published by The Guardian.

Schneier on Security
JUNE 8, 2021
Our military systems are vulnerable. We need to face that reality by halting the purchase of insecure weapons and support systems and by incorporating the realities of offensive cyberattacks into our military planning. Over the past decade, militaries have established cyber commands and developed cyberwar doctrine.

John Battelle's Searchblog
NOVEMBER 4, 2011
( image ) As I begin to dig into the work of my next book, I’ve found myself thinking about politics and government far more than I anticipated. For initial thoughts and stats, see Government By Numbers: Some Interesting Insights ). I focus on the US for this exercise, as I am writing from my own experience.

Security Affairs
AUGUST 10, 2020
There are four operators in Myanmar: state-owned Myanma Posts and Telecommunications ( MPT ) , Qatar based Ooredoo, military-aligned Mytel, and privately owned Telenor Myanmar. Blocked websites have no means to identify and contact the organization responsible of the blocking and exercise their rights to object.

The Last Watchdog
NOVEMBER 26, 2018
Other hubs followed at military bases, other state universities and even a high school and a non-profit community arts and tech center. The early Cyber Range hubs were mainly used to help educate and certify military technicians and cybersecurity professionals at selected companies. They answered, yes. Shoring up weak links.

The Last Watchdog
SEPTEMBER 13, 2018
military carry out training exercises for real life cyber warfare. That led to a transition into what it is today: a leading supplier of immersive “gamification” training modules designed to keep cyber protection teams in government, military, and corporate entities on their toes.

eSecurity Planet
JULY 17, 2024
The North Atlantic Treaty Organization (NATO), a military alliance formed in 1949 to counter the Soviet threat during the Cold War, has traditionally focused on deterring and defending against conventional military attacks. The fight against cyberthreats extends beyond military alliances.

IT Governance
APRIL 27, 2018
This week, we discuss TSB’s chaotic system upgrade, a security flaw in electronic hotel locks and a major NATO cyber security exercise. Hello and welcome to the IT Governance podcast for Friday, 27 April 2018. According to CCDCOE, the exercise is running from 23 to 27 April. Here are this week’s stories.

eSecurity Planet
MARCH 22, 2022
The latest action came yesterday, when Biden warned of “evolving intelligence that the Russian Government is exploring options for potential cyberattacks.” “Cyber war is not military versus military; all organizations, across public and private sectors, will have to defend themselves from attack,” he said.

John Battelle's Searchblog
JANUARY 24, 2012
This shift affects everything from the strategy that guides it to the individuals who oversee it (civilian political appointees) and the lawyers who advise them (civilians rather than military officers). This is virtual reality as a new way of knowledge: a new and terrible kind of transcendent military power. Why not purple dragons? (Ed:

Thales Cloud Protection & Licensing
SEPTEMBER 12, 2019
First, it said that it would invest in cultivating military assets in the digital space, as reported by the Organization for World Peace. Second, Japan announced that the government-backed National Institute of Information and Communications Technology would conduct a national scan of Internet of Things (IoT) devices.

Unwritten Record
AUGUST 2, 2022
Government-issued combat boots. Here in the Still Picture Branch at the National Archives, we have a handful of photographs within our holdings that show a glimpse into Elvis’ time with the military. Army’ 3rd Armd Div Winter Shield Exercise plan the day’s reconnaissance during field exercise in Bavaria in West Germany.

Unwritten Record
FEBRUARY 6, 2024
The country needed to quickly increase the number of soldiers in the military while also increasing the production of wartime goods and manufacturing. To do this, the United States Government employed several strategies to garner the support of the American people. The First Motion Picture Unit, part of the U.S.

The Last Watchdog
NOVEMBER 28, 2018
State-of-the-art telepresence gear, supplied by Merit Network , funnels everything from capture-the-flag exercises to full course work and certification testing to earn 42 different professional designations. Today Merit supplies IT infrastructure to schools, universities, government and other entities across the state.

Brandeis Records Manager
JULY 13, 2017
Red teaming (RT), with origins in the military, involves thinking differently and more objectively about your program, looking under rocks, and grasping alternative views of the way things are. Devil’s advocates have long been paired with RT exercises. by] making critical and contrarian thinking part of the planning process.”.

OpenText Information Management
MARCH 28, 2024
Defending against Advanced Persistent Threats (APT) A leading financial investment management organization put their security posture to the test and OpenText stood out as the sole solution that detected an unannounced advanced red team exercise. Kevin has more than 10 years experience in cybersecurity engineering and consulting.

Schneier on Security
JUNE 3, 2024
Scott explored what happens when governments, or those with authority, attempt and fail to “improve the human condition.” It is this constructed reality that shapes the decisions businesses make every day, governs financial markets, influences geopolitical strategy, and increasingly controls more of how global society functions.

ForAllSecure
AUGUST 18, 2021
She is a daughter of a military father and so she went to West Point Academy, as one of the first female cadets. And, finally, CISA partners with local and state governments by sharing best practices from around the country. exercise these whole nation attack plans to prepare. Easterly began by presenting her bio.

KnowBe4
APRIL 4, 2023
Human Rights Groups Olga Lautman reported on a very sophisticated social engineering tactic that completely falsifies Non-Government Organizations (NGOs). The NGO Watchlist identifies suspicious NGOs and investigates their funders and links to government influence. or UK government authority."

IT Governance
DECEMBER 20, 2022
Tensions rose throughout February as the Russian military amassed across the Ukrainian border. Although Vladimir Putin and his sympathisers assured the world that they were simply conducting military exercises, the inevitable occurred on 24 February, when troops mobilised and war was declared.

Thales Cloud Protection & Licensing
APRIL 24, 2019
It was developed over the 20th century to enable the successful realization of more complex engineering projects; from telephony to military, space and automotive domains. However, developing complex software systems with large teams is still a fallible, expensive and inconsistent exercise.

eSecurity Planet
APRIL 26, 2024
Governance, risk, and compliance (GRC) management: Aligns security goals with business goals and regulatory requirements that apply to the data or the organization. Governance, risk, and compliance (GRC) tools help to prioritize the most valuable or the most damaging data and systems for additional layers of protection.

IT Governance
DECEMBER 13, 2018
Hello and welcome to the final IT Governance podcast of 2018. Even government and public bodies’ websites – including, ironically, the ICO – were found to be running cryptomining software after a third-party plug-in was compromised, but it transpired.

ForAllSecure
AUGUST 30, 2022
The governments of the world wanted the quick and agile minds of children who could think three dimensional -- and without all that moralizing about killing, you know, space aliens. And it could be somebody like a target, it could be a bank, it could be a municipality, like the city of New York, or it could be the US military.

KnowBe4
JULY 5, 2023
Government. Yes, we have started with training and recently conducted a phishing exercise, we are currently doing a POC test with a few users regarding the PAB functionality. Date/Time: Wednesday, July 12, @ 2:00 PM (ET) Save My Spot! Zimperium has the story: [link] What KnowBe4 Customers Say "Hi Stu, I trust that you are well.

ForAllSecure
SEPTEMBER 18, 2020
government -- hacking the U.S. Government - as part of a red or blue team experience. Vamosi: The term red team is military in origin. Part of Cold War wargaming exercises, the red teams are always viewed as offensive, or the attackers -- in this case it could be reference to the red Soviet Union. Or a blue team?

ForAllSecure
SEPTEMBER 17, 2020
government -- hacking the U.S. Government - as part of a red or blue team experience. Vamosi: The term red team is military in origin. Part of Cold War wargaming exercises, the red teams are always viewed as offensive, or the attackers -- in this case it could be reference to the red Soviet Union. Or a blue team?

ForAllSecure
SEPTEMBER 17, 2020
government -- hacking the U.S. Government - as part of a red or blue team experience. Vamosi: The term red team is military in origin. Part of Cold War wargaming exercises, the red teams are always viewed as offensive, or the attackers -- in this case it could be reference to the red Soviet Union. Or a blue team?

Data Matters
FEBRUARY 20, 2020
decrease from FY 2018, OCIE attributes the relatively small decrease to the month long suspension of examinations during the 2019 government shutdown. In FY 2019, OCIE examined approximately 15% of all RIAs, notwithstanding the government shutdown in early 2019. Information Security . OCIE completed 3,089 examinations in FY 2019.

Data Matters
JANUARY 24, 2020
OCIE also will focus on recommendations and advice provided to retail investors, with a particular emphasis on seniors, retirees, teachers and military personnel, as well as products that the SEC considers higher risk (e.g., In FY 2019, OCIE examined approximately 15% of all RIAs, notwithstanding the government shutdown in early 2019.

Archives Blogs
JULY 28, 2017
Most meeting minutes don’t read like this, and it seems likely that Sapis/Stone was exercising his writing muscles and ability for tongue-in-cheek prose with this first notebook entry. Ought any government to interfere in any religion?”. Have military heroes been beneficial to the world?”. Is deception justifiable in any case?”.

Security Affairs
DECEMBER 17, 2023
CISA and ENISA enhance their Cooperation CISA adds Qlik bugs to exploited vulnerabilities catalog Report: 2.6 CISA and ENISA enhance their Cooperation CISA adds Qlik bugs to exploited vulnerabilities catalog Report: 2.6

ForAllSecure
JANUARY 19, 2022
For example, here’s Jerry Lewis in a scene from a 1950s film, where he’s trying to break into a Nazi German military base. And I think it is an exercise, pretty fun to look at those credentials. Fact is, we’ve long had passwords as a credential. Lewis: Good. Other: Wait. I must have the password.

ForAllSecure
MAY 2, 2023
While I produced this episode, a 21 year old Massachusetts National Guard airman is alleged to have photographed and distributed copies of classified US Military material on Discord, a social media site. All those exercises, the honeypot or honeynet challenges I think that's what they were called in. Let's analyze stuff.

Hunton Privacy
OCTOBER 31, 2023
Notably, the Order requires private companies to share with the federal government the results of “red-team” safety tests for foundation models that pose certain risks, directs the development of new AI standards to guide government agencies’ acquisition and use of AI, creates a new National AI Research Resource to foster U.S.

Adam Shostack
JANUARY 2, 2025
Prudence, indeed, will dictate that Governments long established should not be changed for light and transient causes; and accordingly all experience hath shewn, that mankind are more disposed to suffer, while evils are sufferable, than to right themselves by abolishing the forms to which they are accustomed.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content