Military Exercises Trigger Russian DDoS Attacks on Japan
Data Breach Today
OCTOBER 18, 2024
Russian Actors Disrupt Websites of Political Party, Business and Government Groups Plans by Japan and U.S.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Data Breach Today
OCTOBER 18, 2024
Russian Actors Disrupt Websites of Political Party, Business and Government Groups Plans by Japan and U.S.

Security Affairs
AUGUST 20, 2023
North Korea-linked APT group Kimsuky carried out a spear-phishing campaign against US contractors involved in a joint U.S.-South South Korea military exercise. The military drill, the Ulchi Freedom Guardian summer exercises , will start on Monday, August 21, 2023 , and will last 11 days. ” reported Reuters agency.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
MAY 14, 2022
Pro-Russian hacker group Killnet targeted the websites of several Italian institutions, including the senate and the National Institute of Health. Our Legion conducts military cyber exercises in your countries in order to improve their skills. The impact was limited, the websites were unreachable for a short period of time.
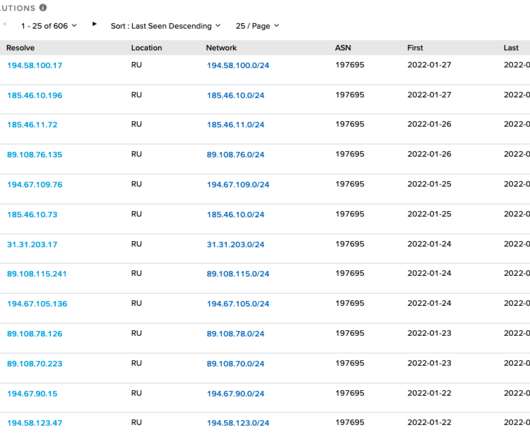
Security Affairs
FEBRUARY 4, 2022
The Russia-linked Gamaredon APT group attempted to compromise an unnamed Western government entity in Ukraine. In Mid January the Ukrainian government was hit with destructive malware, tracked as WhisperGate , and several Ukrainian government websites were defaced by exploiting a separate vulnerability in OctoberCMS.

Collibra
NOVEMBER 20, 2020
So your team has identified implementing data governance as a priority for the year. But what happens once you purchase a data governance platform? This article is meant to outline the vital steps for implementing data governance. Why a data governance roadmap is vital. 10 steps to successful data governance.

Hunton Privacy
DECEMBER 1, 2020
million on Carrefour France and a fine of €800,000 on Carrefour Banque for various violations of the EU General Data Protection Regulation (“GDPR”) and Article 82 of the French Data Protection Act governing the use of cookies. Carrefour France and Carrefour Banque are both affiliates of the French retail group, the Carrefour Group.

Krebs on Security
OCTOBER 5, 2022
The fabricated LinkedIn identities — which pair AI-generated profile photos with text lifted from legitimate accounts — are creating major headaches for corporate HR departments and for those managing invite-only LinkedIn groups. ” The opening slide for a plea by Taylor’s group to LinkedIn.

Hunton Privacy
DECEMBER 2, 2020
On November 25, 2020, the European Commission published its Proposal for a Regulation on European Data Governance (the “Data Governance Act”). The Data Governance Act is part of a set of measures announced in the 2020 European Strategy for Data , which is aimed at putting the EU at the forefront of the data empowered society.
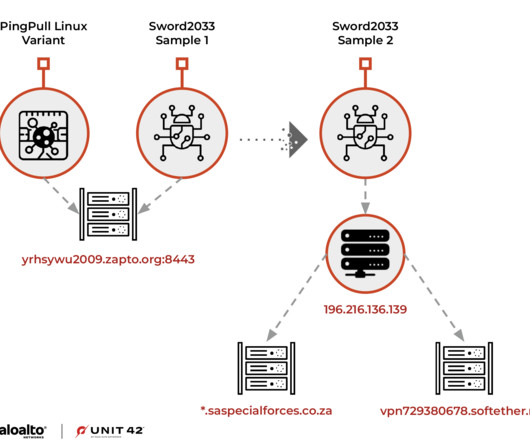
Security Affairs
APRIL 26, 2023
Researchers from Palo Alto Networks Unit 42 recently observed the China-linked Alloy Taurus group (aka GALLIUM , Softcell ) targeting Linux systems with a new variant of PingPull backdoor. In recent years, the researchers observed the group expanding its operations to include financial institutions and government entities.

Gimmal
JUNE 10, 2022
Craig Carpenter and Dean Gonsowski , Gimmal’s CEO and CRO respectively, spoke with Ari about information discovery, migration, governance, and compliance, and how Gimmal helps organization address their biggest information governance challenges. It started as a GRC — governance risk and compliance — consulting firm.
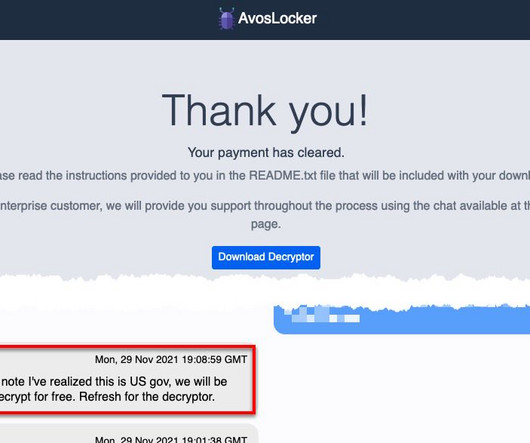
Security Affairs
OCTOBER 13, 2023
The AvosLocker ransomware-as-a-service emerged in the threat landscape in September 2021, since January the group expanded its targets by implementing support for encrypting Linux systems, specifically VMware ESXi servers. This joint CSA updates the advisory published by the US Government on March 17, 2022.

IT Governance
JUNE 22, 2023
The cyber intelligence firm Group-IB discovered the compromised data within the logs of info-stealing malware traded on various underground websites. Indeed, over a quarter of all the stolen information found by Group-IB came last month, with threat actors posting 26,800 new pieces of data in May 2023. How was this possible?

Security Affairs
AUGUST 4, 2020
China-linked hackers carried out cyber espionage campaigns targeting governments, corporations, and think tanks with TAIDOOR malware. China has been using #Taidoor malware to conduct #cyber espionage on governments, corporations, and think tanks. US government agencies published the Malware Analysis Report MAR-10292089-1.v1

Security Affairs
JULY 22, 2021
Government experts reported that threat actors are targeting Pulse Secure devices since June 2020 by attempting to exploit multiple know vulnerabilities, including CVE-2019-11510 , CVE-2020-8260 , CVE-2020-8243 , CVE-2021-2289. Do not add users to the local administrators group unless required. ” Reads the CISA’s alert.

Data Protector
AUGUST 17, 2020
One of the Government's core objectives throughout the Brexit negotiations has been to respect data protection rights, slash Brussels' red tape and allow the United Kingdom to be a competitive safe haven for businesses all over the world. No longer might UK privacy pros feel obliged to wait for the publication of weirdly worded EDPB opinions.
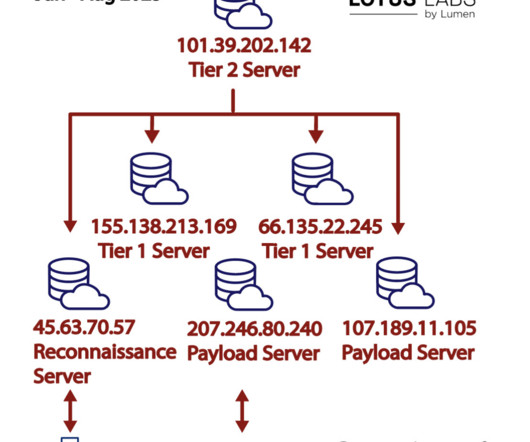
Security Affairs
AUGUST 21, 2023
In June the group started a reconnaissance and targeting activity aimed at a U.S. One of these virtual private servers was exclusively employed in attacks against entities across Taiwan, including commercial firms and at least one municipal government organization. Another VPS node was used to target a U.S. 57 155.138.213[.]169

Security Affairs
JANUARY 13, 2024
Akira ransomware targets Finnish organizations GitLab fixed a critical zero-click account hijacking flaw Juniper Networks fixed a critical RCE bug in its firewalls and switches Vast Voter Data Leaks Cast Shadow Over Indonesia ’s 2024 Presidential Election Researchers created a PoC for Apache OFBiz flaw CVE-2023-51467 Team Liquid’s wiki leak exposes (..)

Security Affairs
FEBRUARY 14, 2020
The government experts released new and updated Malware Analysis Reports (MARs) related to new malware families involved in new attacks carried out by North Korea-linked HIDDEN COBRA group. Do not add users to the local administrators group unless required. Exercise caution when using removable media (e.g.,

The Last Watchdog
JANUARY 31, 2019
A report co-sponsored by Lloyd’s of London paints a chilling scenario for how a worldwide cyberattack could trigger economic losses of some $200 billion for companies and government agencies ill-equipped to deflect a very plausible ransomware attack designed to sweep across the globe. cyber foes exploit government shutdown.

CGI
FEBRUARY 14, 2017
10 measures for good IT security governance. Adequate security and governance of information assets no longer can be achieved on an ad hoc basis, nor addressed by technology alone. I invite you to read more on this topic in our white paper on IT Security Governance. harini.kottees…. Wed, 02/15/2017 - 01:58. Add new comment.

Security Affairs
DECEMBER 17, 2023
CISA and ENISA enhance their Cooperation CISA adds Qlik bugs to exploited vulnerabilities catalog Report: 2.6 CISA and ENISA enhance their Cooperation CISA adds Qlik bugs to exploited vulnerabilities catalog Report: 2.6

Data Protection Report
NOVEMBER 2, 2023
Risk management framework for outsourced data: Where a firm outsources the processing of data, including to an intra-group company, there must be in place an appropriate risk management framework that allows the firm to identify and mitigate the risks inherent in that outsourcing.

eSecurity Planet
JANUARY 27, 2023
.” CISA noted that while the motive appeared to be financial, the hackers could resell access to cyber criminals or APT groups, who are “known to use legitimate RMM software as a backdoor for persistence and/or command and control (C2).” Implement a user training program and phishing exercises to raise awareness among users.

The Last Watchdog
NOVEMBER 26, 2018
I was recently privileged to be part of a group of journalists covering the 2018 North American International Cyber Summit at Detroit’s Cobo Convention Center. It can host training, such as capture the flag exercises, demonstrate how known hacks play out, test defensive responses and be utilized for software security testing.
The Texas Record
MARCH 31, 2021
Agencies or local governments that are tight on storage space might look forward to speedily carrying out disposition on records that have met their full retention periods, but there are cases when reaching a destruction eligibility date may not put the records manager in the clear to destroy or transfer those records.

CILIP
MAY 13, 2024
Ben Lee, Co-Director of Shared Intelligence, explains that his own professional background began in central government, but he has “had a varied career, getting involved in community empowerment, arts and culture, impact evaluation, and futures literacy”. and ‘will local government have more or less freedom?’)

AIIM
NOVEMBER 7, 2019
The class started with some icebreaker exercises, including asking the students to define, in their own words, “ What is information management? That is to say, where should the information management/records management/information governance job function be located within an organizational structure? Information Governance “Island”.

Brandeis Records Manager
JULY 13, 2017
Devil’s advocates have long been paired with RT exercises. Capture your responses, state each problem, brainstorm alternative possibilities, and thoroughly review them with your group. While whole standing teams are ideal, I’d suggest that “RT lite” or “lean RT” may be more realistically employed with scant resources.

Security Affairs
FEBRUARY 16, 2019
ISPs should be able to route traffic through nodes under the control of the Russian Government to allow the connections between Russians entities. ” The experiment has been agreed in a session of the Information Security Working Group at the end of January. . ” reported ZDNet. and Yandex.ru

Security Affairs
APRIL 14, 2022
The US government agencies warned of threat actors that are targeting ICS and SCADA systems from various vendors. The CHERNOVITE Activity Group (AG) developed PIPEDREAM. Have a cyber incident response plan, and exercise it regularly with stakeholders in IT, cybersecurity, and operations.

The Security Ledger
SEPTEMBER 25, 2018
But an exercise in Boston last week showed how hackers can compromise the vote without ever touching an election system. But an exercise in Boston last week showed how hackers can compromise the vote without ever touching an election system. That’s the scenario of an exercise that took place high above Boston last week.

InfoGovNuggets
JANUARY 22, 2019
After problems with the spread of fake news and rumors that may have led to violence in India, WhatsApp will now reduce the number of individuals (including groups) you can forward a message to, from 20 to 5. Is that Governance or Information or both? So, one way to fight fake news is to restrict how many people you can send it to.

DLA Piper Privacy Matters
SEPTEMBER 6, 2021
Article 60 decisions govern the process of cooperation between lead supervisory authorities, and concerned supervisory authorities. The final decision was made pursuant to Section 111 of the Data Protection Act and in accordance with Articles 60 and 65 of the GDPR.

Thales Cloud Protection & Licensing
NOVEMBER 10, 2022
But that gave us a priority group to focus on. This is exciting for us, and we’re exercising a lot of new muscles in doing this work. We want to build strong governance, joint marketing and demand generation with these partners. Which of these companies stand to win the most from having a more integrated partnership with us?

Unwritten Record
FEBRUARY 6, 2024
To do this, the United States Government employed several strategies to garner the support of the American people. One such tactic the government relied on heavily was the production of public relations materials including propaganda. Other parts of their training are also depicted, such as flight simulation and exercise.

OpenText Information Management
APRIL 2, 2024
Mark will be joined by OpenText customer Vincent Champain, SVP of Digital Performance & IT with Framatome Group , who will discuss how the energy company uses OpenText Content solutions to manage its core business operations. Wondering what’s new in our products?

The Last Watchdog
SEPTEMBER 13, 2018
military carry out training exercises for real life cyber warfare. That led to a transition into what it is today: a leading supplier of immersive “gamification” training modules designed to keep cyber protection teams in government, military, and corporate entities on their toes. It adapted its gaming systems to help the U.S.

OpenText Information Management
APRIL 1, 2024
He will dive into the OpenText cloud roadmap to showcase how security, trust, and governance are at the center of serving our customers with our deeply integrated solutions. Next up is OpenText CPO Muhi Majzoub , whose keynote will address how information management in the cloud has become a prerequisite of AI.

Data Matters
JULY 8, 2019
Ensuring that a company is properly prepared for and responds to privacy and cyber security threats is a key corporate governance responsibility for directors and senior officers. This action by the ICO demonstrates that they are prepared to enforce the GDPR and levy significant fines.

Hunton Privacy
NOVEMBER 5, 2020
Section 189 requires the UK government to review the operation of the representative action provisions of the DPA and provide a report to Parliament by November 25, 2020. Representative actions do not necessarily allow for the measurement of true loss suffered by an individual, especially where data subjects are not even consulted.

IBM Big Data Hub
JANUARY 22, 2024
The General Data Protection Regulation (GDPR) is a European Union (EU) law that governs how organizations collect and use personal data. Schools, hospitals and government agencies all fall under GDPR authority. A data controller is any organization, group or person that obtains personal data and determines how it is used.

Managing Your Information
SEPTEMBER 10, 2022
Compliance professionals including those working in Information Governance and Information Assurance . This course will be delivered by Liz Taylor and Frank Rankin , who each possess over 25 years’ experience working as professionals within the information governance arena. . The course is suitable for: . Human Resource managers

Unwritten Record
FEBRUARY 13, 2024
The photographs span multiple record groups and show Valentine’s Day greetings and dances. Record Group 111: Records of the Office of the Chief Signal Officer Original Caption: WAC Valentine, Pfc. February 15, 1945 Local photo ID number: 80-G-48124 Record Group 127: Records of the U.S. Brisbane, Q’land, Australia.

Hunton Privacy
OCTOBER 2, 2018
In addition, the CNIL examined solutions to enable data subjects to exercise their data protection rights. If it is appropriate to use blockchain technology, data controllers should use a consortium blockchain that ensures better control of the governance of personal data, in particular with respect to data transfers outside of the EU.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content