Military Exercises Trigger Russian DDoS Attacks on Japan
Data Breach Today
OCTOBER 18, 2024
Russian Actors Disrupt Websites of Political Party, Business and Government Groups Plans by Japan and U.S.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Data Breach Today
OCTOBER 18, 2024
Russian Actors Disrupt Websites of Political Party, Business and Government Groups Plans by Japan and U.S.

Security Affairs
AUGUST 20, 2023
-South Korea military exercise. The military drill, the Ulchi Freedom Guardian summer exercises , will start on Monday, August 21, 2023 , and will last 11 days. The military exercises aim at improving the ability of the two armies to respond to North Korea’s evolving nuclear and missile threats.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
AUGUST 16, 2020
The Australian government aims at giving itself the power to manage the response of private enterprises to cyber attacks on critical infrastructure. The Australian government wants to increase the security of critical infrastructure, for this reason, it plans to manage the response of private enterprises to cyber attacks targeting them.

Security Affairs
MAY 14, 2022
Our Legion conducts military cyber exercises in your countries in order to improve their skills. ” The list of the targeted websites was shared on the Telegram channel of the Pro-Russian hacker collective known as The Legion which focuses on attacks against Western organizations and governments, including NATO countries and the Ukraine.

Security Affairs
FEBRUARY 24, 2023
Defence Cyber Marvel 2 (DCM2) is the largest Western Europe-led cyber exercise that took place in Tallinn with 34 teams from 11 countries. This year, 750 cyber specialists have participated in the military cyberwarfare exercise. ” reads the press release published by the UK Ministry of Defence. .

Collibra
AUGUST 5, 2024
Data governance programs create policies, processes, and roles for handling large quantities of data in a way that makes it accurate, trustworthy, and available for decision-making. No matter the organization’s size, every company faces similar roadblocks to installing an effective, sustainable data governance program.

Hunton Privacy
JULY 5, 2022
On June 21, 2022, President Biden signed into law, the State and Local Government Cybersecurity Act of 2021 (S. 1097) (the “Cyber Workforce Program Act”), two bipartisan bills aimed at enhancing the cybersecurity postures of the federal, state and local governments.

Security Affairs
JANUARY 16, 2022
The simulation took place on Friday and is part of a six-week exercise aimed at testing also the cooperation among member states and their joint response. The start of the cyber exercise was concurrent with the attacks against tens of Ukraine’s government websites. ” reads the post published by Bloomberg.

Adam Levin
JANUARY 15, 2019
citizens are more vulnerable to the effects of identity theft and scams as a result of the ongoing government shutdown. The two primary websites created by the government as resources for victims of identity theft, IdentityTheft.gov and FTC.gov/complaint , are currently offline as part of the partial shutdown of the Federal Trade Commission.

Data Protection Report
JUNE 22, 2022
UK GDPR Reform: government publishes response to consultation – likely to form basis of forthcoming UK Data Reform Bill. The Department for Culture, Media and Sport (DCMS) has finally published the UK government’s long-awaited response to the consultation on the future of the UK data protection regime. Reform of Article 22.

Data Matters
SEPTEMBER 30, 2020
government released a “White Paper” addressing how U.S. law and practice relating to government access to data for national security purposes,” especially as that information bears on “issues that appear to have concerned the ECJ in Schrems II ” and as it “may bear on many companies’ analyses” of how their reliance on SCCs conforms to EU law.

The Last Watchdog
AUGUST 23, 2021
For instance, if you have employees in China and the EU, you’ll have to obtain Chinese government approval to provide data from China to EU authorities enforcing the GDPR. Government Monitoring. Similarly, different nations exercise varying amounts of authority over internet traffic.
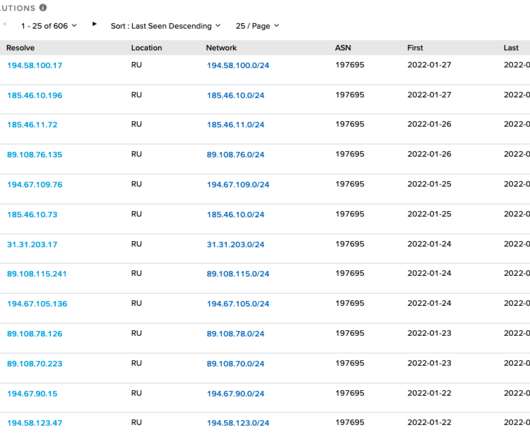
Security Affairs
FEBRUARY 4, 2022
The Russia-linked Gamaredon APT group attempted to compromise an unnamed Western government entity in Ukraine. In Mid January the Ukrainian government was hit with destructive malware, tracked as WhisperGate , and several Ukrainian government websites were defaced by exploiting a separate vulnerability in OctoberCMS.

Collibra
OCTOBER 4, 2023
The federal government is no exception. Today’s citizens, accustomed to the speed and personalization of digital experiences, expect no less from their government. For the federal government to modernize and meet the needs of the contemporary citizen, it must tap into the vast reservoirs of data at its disposal.

Collibra
MAY 5, 2020
They need data governance. . They need data governance. What does data governance do? Governance delivers the context, relationships, lineage, and access data citizens need to make decisions around data. Data governance provides background on where data came from, how it’s used, and how trustworthy it is.

Security Affairs
AUGUST 4, 2020
China-linked hackers carried out cyber espionage campaigns targeting governments, corporations, and think tanks with TAIDOOR malware. China has been using #Taidoor malware to conduct #cyber espionage on governments, corporations, and think tanks. US government agencies published the Malware Analysis Report MAR-10292089-1.v1

The Last Watchdog
APRIL 5, 2022
The Chinese government is well known for its censorship– and frequent harassment and intimidation of foreign journalists. In a recent statement , the Foreign Correspondents Club of China (FCCC) commented, “Covering China is increasingly becoming an exercise in remote reporting, as China cuts off new visas and expels journalists.”

AIIM
APRIL 13, 2021
He refers to the current attention on privacy matters as “privacy theater,” believing that apps are grabbing more of our data than they need to get the job done, and any assertion that these brands care about our personal data is largely a public relations exercise. and Jasen Hutchinson, Manager, Corporate Records Compliance, JEA.

John Battelle's Searchblog
JANUARY 25, 2019
My current work is split between two projects: One has to do with data governance, the other political media. And second… Governance. Government – well for sure, I’d wager that’s increased given who’s been running the country these past two years. But Governance? Data Governance. We’ll start with Governance.

The Last Watchdog
APRIL 11, 2022
While it’s nice to see law enforcement and governments go after the gangs, that won’t stop the monster that has grown out of control, that we, as an industry, continue to feed. They’re easier to attack and provide moderate consistent payouts with little retribution from law enforcement or governments. Bricks in the wall.

Security Affairs
DECEMBER 13, 2023
A Joint Committee on the National Security Strategy (JCNSS) warns of the high risk of a catastrophic ransomware attack on the UK government. The British government is accused of failing to mitigate the risk of ransomware attacks. Beckett recommends the UK government consider defense from ransomware attacks a top political priority. “in

Krebs on Security
MARCH 8, 2024
government. government. government levied financial sanctions against Channel One that bar US companies or citizens from doing business with the company. government. Formed in 2009, Radaris is a vast people-search network for finding data on individuals, properties, phone numbers, businesses and addresses.
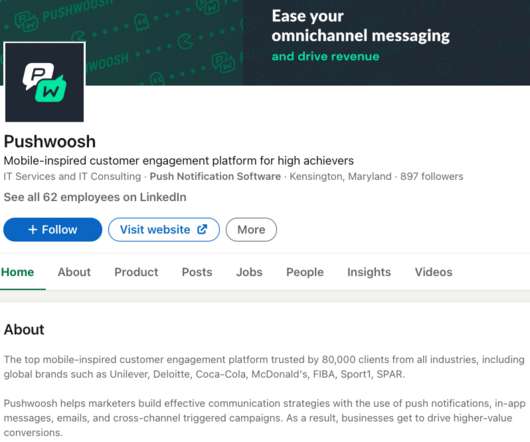
Krebs on Security
NOVEMBER 28, 2022
Pushwoosh’s software also was found in apps for “a wide array of international companies, influential nonprofits and government agencies from global consumer goods company Unilever and the Union of European Football Associations (UEFA) to the politically powerful U.S. regulatory filings present it as a U.S. ” GOV 311.
Krebs on Security
JUNE 3, 2022
In most of these cases, the researcher isn’t worried that the government is going to come after them: It’s that they’re going to get sued by the company responsible for the security vulnerability or data leak. ” The new DOJ policy comes in response to a Supreme Court ruling last year in Van Buren v.

Krebs on Security
APRIL 16, 2020
“It’s either that or the government gets involved. government may well soon get more involved. . “It’s really hard to do anything about this unless the registrars step up and do something on their own,” Daniel said. ” The U.S. Earlier this week, Senators Cory Booker (D-N.J.), Maggie Hassan (D-N.H.)

The Last Watchdog
FEBRUARY 14, 2022
Automating these processes with the help of Identity Governance and Administration ( IGA ) tools should be a top priority for your IT department. You should end this exercise with the definition of a roadmap that outlines a clear path for implementing the single measures in a reasonable order.

Data Protector
AUGUST 17, 2020
One of the Government's core objectives throughout the Brexit negotiations has been to respect data protection rights, slash Brussels' red tape and allow the United Kingdom to be a competitive safe haven for businesses all over the world. No longer might UK privacy pros feel obliged to wait for the publication of weirdly worded EDPB opinions.

Security Affairs
JULY 22, 2021
Government experts reported that threat actors are targeting Pulse Secure devices since June 2020 by attempting to exploit multiple know vulnerabilities, including CVE-2019-11510 , CVE-2020-8260 , CVE-2020-8243 , CVE-2021-2289. Exercise caution when using removable media (e.g., ” Reads the CISA’s alert.

Security Affairs
APRIL 1, 2024
The US government announced establishing the Office of the Assistant Secretary of Defense for Cyber Policy. Exercising authority, direction, and control over the official designated as Deputy PCA concerning their Deputy PCA duties. Spearheading the DoD’s implementation of national-level cyberspace policies.

The Last Watchdog
JANUARY 31, 2019
A report co-sponsored by Lloyd’s of London paints a chilling scenario for how a worldwide cyberattack could trigger economic losses of some $200 billion for companies and government agencies ill-equipped to deflect a very plausible ransomware attack designed to sweep across the globe. cyber foes exploit government shutdown.

IT Governance
MARCH 30, 2023
These rights can be exercised by first submitting a DSAR (data subject access request). If the individual is unhappy with any of the details provided in this access request, they can exercise one of their data subject rights, including the right to erasure. This is where IT Governance can help. Can you charge a fee?

Hunton Privacy
DECEMBER 2, 2020
On November 25, 2020, the European Commission published its Proposal for a Regulation on European Data Governance (the “Data Governance Act”). The Data Governance Act is part of a set of measures announced in the 2020 European Strategy for Data , which is aimed at putting the EU at the forefront of the data empowered society.

DLA Piper Privacy Matters
MAY 19, 2020
In 2017, the DPC’s Special Investigation Unit (SIU) investigated the governance of Tusla, examining the processing of personal data in child protection cases. It found that there had been insufficient governance planning when Tusla was established, taking into account the volume of cases which it subsumed in 2014.

Data Protection Report
DECEMBER 17, 2020
On 25 November 2020, the European Commission ( EC ) published its proposed Data Governance Regulation (the DGR ), which will create a new legal framework to encourage the development of a European single market for data. What are the objectives of the Data Governance Regulation? This is part one of a series of three blog posts.

Security Affairs
OCTOBER 8, 2021
The Dutch government will not tolerate ransomware attacks that could threaten national security, it will use intelligence or military services to curb them. The Dutch government announced that it will not tolerate cyberattacks that pose a risk to its national security and will employ intelligence or military services to counter them.

Security Affairs
FEBRUARY 14, 2020
The government experts released new and updated Malware Analysis Reports (MARs) related to new malware families involved in new attacks carried out by North Korea-linked HIDDEN COBRA group. . Exercise caution when opening e-mail attachments even if the attachment is expected and the sender appears to be known.

Data Protector
AUGUST 17, 2020
If the UK receives an EU adequacy assessment, presumably the UK Government will simply anglicise the new EU SCCs and ask UK organisations to use the new versions for the Non-EU, UK - Rest of the World data flows. To expect them to commission a similar exercise so soon is cruel (and costly). It could take years to complete.

Data Matters
JANUARY 28, 2022
The advisory was promptly endorsed by the National Cyber Security Centre, a division of Government Communications Headquarters (“GCHQ”), a UK intelligence agency. government, especially in light of ongoing tensions between the U.S. Create, Maintain, and Exercise a Cyber Incident Response, Resilience, and Continuity of Operations Plan.

Security Affairs
AUGUST 21, 2021
Over the past several years, government agencies and its partners have responded to a significant number of ransomware attacks, including recent attacks against Colonial Pipeline and and U.S. The guidance aims at helping government and private sector organizations in preventing such kinds of incidents. softwa re company Kaseya.

Security Affairs
DECEMBER 24, 2019
Russia’s government announced that it has successfully concluded a series of tests for its RuNet intranet aimed at country disconnection from the Internet. The Russian Government has announced on Monday that it has successfully concluded the test on its RuNet intranet and the complete disconnection of the country from the Internet.

Data Protector
AUGUST 17, 2020
I see the IPA as an outstanding example that Governments of all countries should adopt to ensure that public authorities act transparently and put effective mechanisms in place to ensure that human rights are appropriately respected. Where opinion formers had concerns, these issues should be addressed.

Schneier on Security
JUNE 8, 2021
During that same period, we’ve seen increasingly brazen cyberattacks by everyone from criminals to governments. In 2018, a 29-country NATO exercise, Trident Juncture , that included cyberweapons was disrupted by Russian GPS jamming. NATO does try to test cyberweapons outside such exercises, but has limited scope in doing so.

Security Affairs
NOVEMBER 22, 2021
Remind employees not to click on suspicious links, and conduct exercises to raise awareness. . Government experts also warn of other malicious activities such as phishing scams , fraudulent sites spoofing reputable businesses , and unencrypted financial transactions.

The Last Watchdog
NOVEMBER 26, 2018
It can host training, such as capture the flag exercises, demonstrate how known hacks play out, test defensive responses and be utilized for software security testing. Participants competed in exercises to detect improvised explosive devises targeting semi-trucks and military vehicles.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content