Military Exercises Trigger Russian DDoS Attacks on Japan
Data Breach Today
OCTOBER 18, 2024
Russian Actors Disrupt Websites of Political Party, Business and Government Groups Plans by Japan and U.S.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Data Breach Today
OCTOBER 18, 2024
Russian Actors Disrupt Websites of Political Party, Business and Government Groups Plans by Japan and U.S.

Security Affairs
AUGUST 20, 2023
-South Korea military exercise. The military drill, the Ulchi Freedom Guardian summer exercises , will start on Monday, August 21, 2023 , and will last 11 days. The military exercises aim at improving the ability of the two armies to respond to North Korea’s evolving nuclear and missile threats.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
AUGUST 16, 2020
The Australian government aims at giving itself the power to manage the response of private enterprises to cyber attacks on critical infrastructure. The Australian government wants to increase the security of critical infrastructure, for this reason, it plans to manage the response of private enterprises to cyber attacks targeting them.

Security Affairs
FEBRUARY 24, 2023
Defence Cyber Marvel 2 (DCM2) is the largest Western Europe-led cyber exercise that took place in Tallinn with 34 teams from 11 countries. This year, 750 cyber specialists have participated in the military cyberwarfare exercise. ” reads the press release published by the UK Ministry of Defence. .

Security Affairs
MAY 14, 2022
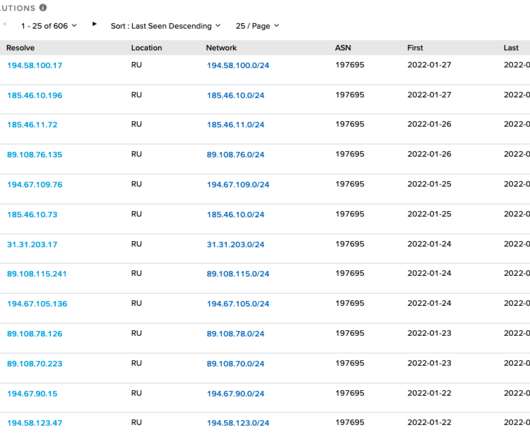
Our Legion conducts military cyber exercises in your countries in order to improve their skills. ” The list of the targeted websites was shared on the Telegram channel of the Pro-Russian hacker collective known as The Legion which focuses on attacks against Western organizations and governments, including NATO countries and the Ukraine.
Security Affairs
FEBRUARY 4, 2022
The Russia-linked Gamaredon APT group attempted to compromise an unnamed Western government entity in Ukraine. In Mid January the Ukrainian government was hit with destructive malware, tracked as WhisperGate , and several Ukrainian government websites were defaced by exploiting a separate vulnerability in OctoberCMS.

Security Affairs
AUGUST 4, 2020
China-linked hackers carried out cyber espionage campaigns targeting governments, corporations, and think tanks with TAIDOOR malware. China has been using #Taidoor malware to conduct #cyber espionage on governments, corporations, and think tanks. US government agencies published the Malware Analysis Report MAR-10292089-1.v1

Security Affairs
DECEMBER 13, 2023
A Joint Committee on the National Security Strategy (JCNSS) warns of the high risk of a catastrophic ransomware attack on the UK government. The British government is accused of failing to mitigate the risk of ransomware attacks. Beckett recommends the UK government consider defense from ransomware attacks a top political priority. “in

Security Affairs
JULY 22, 2021
Government experts reported that threat actors are targeting Pulse Secure devices since June 2020 by attempting to exploit multiple know vulnerabilities, including CVE-2019-11510 , CVE-2020-8260 , CVE-2020-8243 , CVE-2021-2289. Exercise caution when using removable media (e.g., ” Reads the CISA’s alert.

Security Affairs
FEBRUARY 14, 2020
The government experts released new and updated Malware Analysis Reports (MARs) related to new malware families involved in new attacks carried out by North Korea-linked HIDDEN COBRA group. . Exercise caution when opening e-mail attachments even if the attachment is expected and the sender appears to be known.

Security Affairs
OCTOBER 8, 2021
The Dutch government will not tolerate ransomware attacks that could threaten national security, it will use intelligence or military services to curb them. The Dutch government announced that it will not tolerate cyberattacks that pose a risk to its national security and will employ intelligence or military services to counter them.

Security Affairs
DECEMBER 24, 2019
Russia’s government announced that it has successfully concluded a series of tests for its RuNet intranet aimed at country disconnection from the Internet. The Russian Government has announced on Monday that it has successfully concluded the test on its RuNet intranet and the complete disconnection of the country from the Internet.

Security Affairs
AUGUST 21, 2021
Over the past several years, government agencies and its partners have responded to a significant number of ransomware attacks, including recent attacks against Colonial Pipeline and and U.S. The guidance aims at helping government and private sector organizations in preventing such kinds of incidents. softwa re company Kaseya.

Security Affairs
NOVEMBER 22, 2021
Remind employees not to click on suspicious links, and conduct exercises to raise awareness. . Government experts also warn of other malicious activities such as phishing scams , fraudulent sites spoofing reputable businesses , and unencrypted financial transactions.
Security Affairs
SEPTEMBER 6, 2021
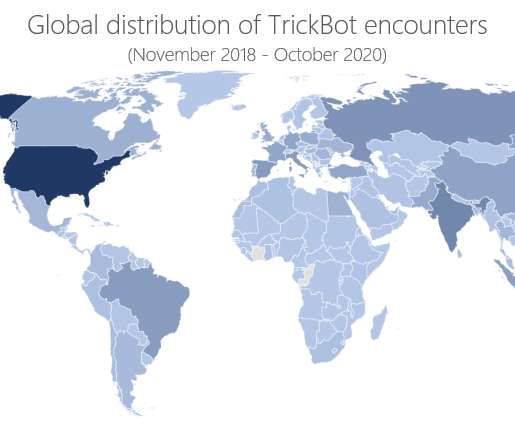
The man has remained stuck in the Asian country since February 2020 due to the COVID-19 lockdown imposed by the local government and the cancelation of international travel. A Russian man accused of being a member of the TrickBot gang was arrested last week at the Seoul international airport.

Security Affairs
DECEMBER 5, 2021
US Government experts also warn of other malicious activities such as phishing scams , fraudulent sites spoofing reputable businesses , and unencrypted financial transactions. Remind employees not to click on suspicious links, and conduct exercises to raise awareness.

Security Affairs
OCTOBER 2, 2019
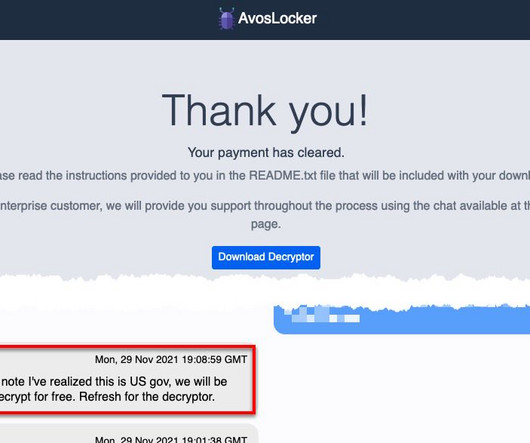
Once again US is warning its allies over Chinese 5G technology, but the Italian Government explained that its special powers over 5G supply deals would mitigate any risk. In September, Italy has exercised special powers in relation to the purchase of goods and services.
Security Affairs
OCTOBER 13, 2023
This joint CSA updates the advisory published by the US Government on March 17, 2022. The advisory also recommends organizations exercise, test, and validate their security program against the threat behaviors mapped to the MITRE ATT&CK for Enterprise framework in this advisory.

Security Affairs
SEPTEMBER 6, 2023
“The Control Environment Laboratory Resource (CELR) is an environment for government and private industry partners to experience the possible effects of kinetic cyber-physical attacks. HSSEDI and CISA collaborated on automated adversary emulation simulations conducted at the CISA’s Control Environment Laboratory Resource (CELR).

Security Affairs
FEBRUARY 12, 2023
Australia’s Defense Department announced that they will remove surveillance cameras made by Chinese firms linked to the government of Beijing. Australia’s Defense Department is going to replace surveillance cameras made by Chinese firms Hikvision and Dahua, who are linked to the government of Beijing. ” reported The Guardian. .”

The Last Watchdog
JANUARY 7, 2025
For example, in a recent attack on French corporates and government agencies, an AI-engineered malware exploited advanced techniques like COM hijacking and encrypted payloads, enabling attackers to remain undetected for extended periods, exfiltrate sensitive data, and establish long-term persistence within the network.

Security Affairs
MARCH 16, 2019
Government experts are warning of spam campaigns using messages containing links pointing to malware or using malicious attachments. “Users should exercise caution in handling emails related to the shooting, even if they appear to originate from trusted sources.” ” reads the security advisory published by the US-CERT.

Collibra
AUGUST 5, 2024
Data governance programs create policies, processes, and roles for handling large quantities of data in a way that makes it accurate, trustworthy, and available for decision-making. No matter the organization’s size, every company faces similar roadblocks to installing an effective, sustainable data governance program.

Hunton Privacy
JULY 5, 2022
On June 21, 2022, President Biden signed into law, the State and Local Government Cybersecurity Act of 2021 (S. 1097) (the “Cyber Workforce Program Act”), two bipartisan bills aimed at enhancing the cybersecurity postures of the federal, state and local governments.
Security Affairs
DECEMBER 30, 2019
Open Media pointed out that that Windows XP is the last operating system developed by Microsoft that was approved by the Kremlin for use on official Russian government computers. Microsoft Windows 10 is only allowed only for government systems that don’t manage secret information. ” reads the post published by The Guardian.

Security Affairs
JANUARY 13, 2024
Akira ransomware targets Finnish organizations GitLab fixed a critical zero-click account hijacking flaw Juniper Networks fixed a critical RCE bug in its firewalls and switches Vast Voter Data Leaks Cast Shadow Over Indonesia ’s 2024 Presidential Election Researchers created a PoC for Apache OFBiz flaw CVE-2023-51467 Team Liquid’s wiki leak exposes (..)
Security Affairs
APRIL 26, 2023
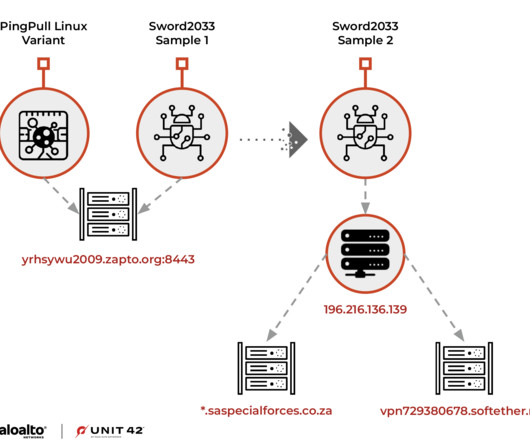
In recent years, the researchers observed the group expanding its operations to include financial institutions and government entities. This domain has been hosted on eight other IPs throughout its history, none of these IPs were directly affiliated with the South African government. saspecialforces.co[.]za za resolved to 196.216.136[.]139.
Security Affairs
AUGUST 21, 2023
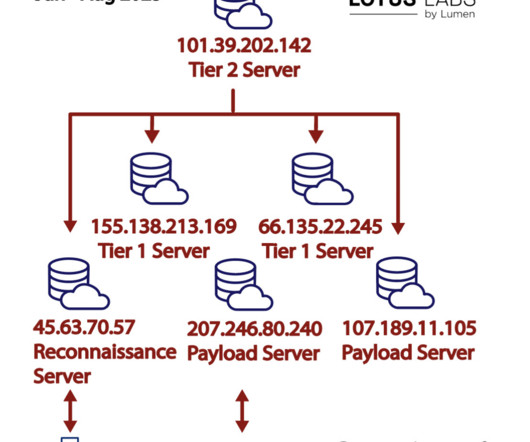
One of these virtual private servers was exclusively employed in attacks against entities across Taiwan, including commercial firms and at least one municipal government organization. “We recommend defense contractors exercise caution and monitor their networking devices for the presence of HiatusRAT. 57 155.138.213[.]169

Adam Levin
JANUARY 15, 2019
citizens are more vulnerable to the effects of identity theft and scams as a result of the ongoing government shutdown. The two primary websites created by the government as resources for victims of identity theft, IdentityTheft.gov and FTC.gov/complaint , are currently offline as part of the partial shutdown of the Federal Trade Commission.

Security Affairs
FEBRUARY 16, 2019
ISPs should be able to route traffic through nodes under the control of the Russian Government to allow the connections between Russians entities. Therefore, they came to the conclusion that market participants need to organize exercises or something similar in order to understand how this can all be implemented in practice” said Kaspersky.

AIIM
APRIL 13, 2021
He refers to the current attention on privacy matters as “privacy theater,” believing that apps are grabbing more of our data than they need to get the job done, and any assertion that these brands care about our personal data is largely a public relations exercise. and Jasen Hutchinson, Manager, Corporate Records Compliance, JEA.

Collibra
OCTOBER 4, 2023
The federal government is no exception. Today’s citizens, accustomed to the speed and personalization of digital experiences, expect no less from their government. For the federal government to modernize and meet the needs of the contemporary citizen, it must tap into the vast reservoirs of data at its disposal.

Security Affairs
APRIL 21, 2019
Locked Shields 2019 – Chapeau, France wins Cyber Defence Exercise. Hacker broke into super secure French Governments Messaging App Tchap hours after release. Gnosticplayers round 5 – 65 Million+ fresh accounts from 6 security breaches available for sale. Yellow Pencil WordPress Plugin flaw expose tens of thousands of sites.

Collibra
MAY 5, 2020
They need data governance. . They need data governance. What does data governance do? Governance delivers the context, relationships, lineage, and access data citizens need to make decisions around data. Data governance provides background on where data came from, how it’s used, and how trustworthy it is.

Security Affairs
APRIL 14, 2022
The US government agencies warned of threat actors that are targeting ICS and SCADA systems from various vendors. Have a cyber incident response plan, and exercise it regularly with stakeholders in IT, cybersecurity, and operations. Enforce multifactor authentication for all remote access to ICS networks and devices whenever possible.

Krebs on Security
APRIL 16, 2020
“It’s either that or the government gets involved. government may well soon get more involved. . “It’s really hard to do anything about this unless the registrars step up and do something on their own,” Daniel said. ” The U.S. Earlier this week, Senators Cory Booker (D-N.J.), Maggie Hassan (D-N.H.)

Security Affairs
FEBRUARY 12, 2022
Almost any sector was hit by sophisticated, high-impact ransomware attacks, including the Defense Industrial Base, Emergency Services, Food and Agriculture, Government Facilities, and Information Technology Sectors. Cybersecurity agencies from the U.K., ” reads the joint advisory.
Krebs on Security
JUNE 3, 2022
In most of these cases, the researcher isn’t worried that the government is going to come after them: It’s that they’re going to get sued by the company responsible for the security vulnerability or data leak. ” The new DOJ policy comes in response to a Supreme Court ruling last year in Van Buren v.
Krebs on Security
NOVEMBER 28, 2022
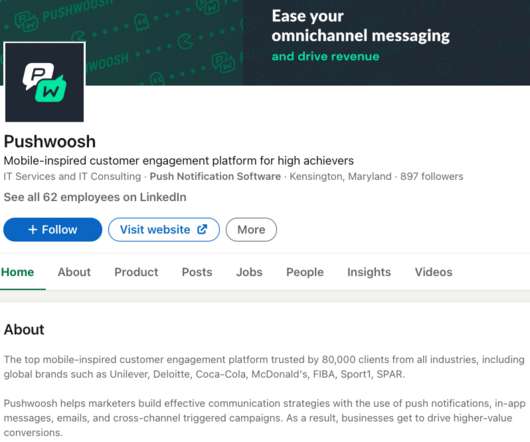
Pushwoosh’s software also was found in apps for “a wide array of international companies, influential nonprofits and government agencies from global consumer goods company Unilever and the Union of European Football Associations (UEFA) to the politically powerful U.S. regulatory filings present it as a U.S. ” GOV 311.

The Last Watchdog
APRIL 5, 2022
The Chinese government is well known for its censorship– and frequent harassment and intimidation of foreign journalists. In a recent statement , the Foreign Correspondents Club of China (FCCC) commented, “Covering China is increasingly becoming an exercise in remote reporting, as China cuts off new visas and expels journalists.”

John Battelle's Searchblog
JANUARY 25, 2019
My current work is split between two projects: One has to do with data governance, the other political media. And second… Governance. Government – well for sure, I’d wager that’s increased given who’s been running the country these past two years. But Governance? Data Governance. We’ll start with Governance.

The Last Watchdog
APRIL 11, 2022
While it’s nice to see law enforcement and governments go after the gangs, that won’t stop the monster that has grown out of control, that we, as an industry, continue to feed. They’re easier to attack and provide moderate consistent payouts with little retribution from law enforcement or governments. Bricks in the wall.

The Last Watchdog
FEBRUARY 14, 2022
Automating these processes with the help of Identity Governance and Administration ( IGA ) tools should be a top priority for your IT department. You should end this exercise with the definition of a roadmap that outlines a clear path for implementing the single measures in a reasonable order.

Security Affairs
AUGUST 10, 2020
Blocked websites have no means to identify and contact the organization responsible of the blocking and exercise their rights to object. Bifrost creates live-mirrors of WordPress sites, and pushes the content to large cloud storage services like Google or Amazon, which are too expensive for governments to block.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content