Coronavirus-themed campaign targets energy sector with PoetRAT
Security Affairs
APRIL 18, 2020
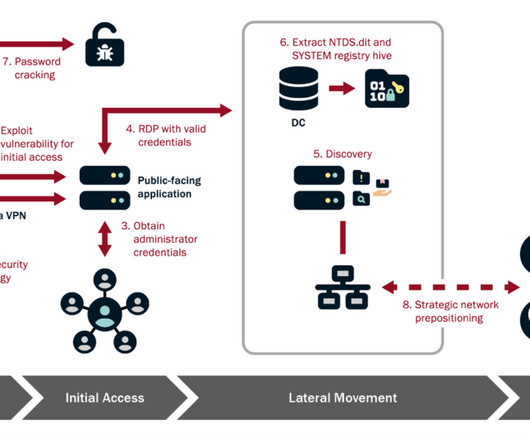
Threat actors employed the previously-undetected PoetRAT Trojan in a Coronavirus-themed campaign aimed at government and energy sectors. . The malware infected ICS and SCADA systems used to control the wind turbines within the renewable energy sector. ” reads the analysis published by Cisco Talos.











































Let's personalize your content