Securing AI Deployments: Striking the Balance
OpenText Information Management
MAY 10, 2024
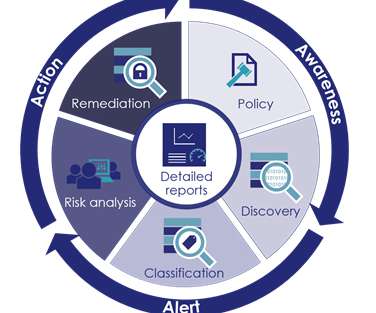
If it’s not accurate, accessible, and secure, organizations won’t get the desired results. Since AI relies on data to learn and improve, organizations must ensure their data is accurate, accessible, and secure. At the same time, we must also protect sensitive information and deliver accurate information to the user.





































Let's personalize your content