How Ransomware Groups Weaponize Stolen Data
Data Breach Today
SEPTEMBER 2, 2024
DataBreachToday.com is a multimedia website providing news, insights and education on data breach detection, notification and prevention.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Data Breach Today
SEPTEMBER 2, 2024
DataBreachToday.com is a multimedia website providing news, insights and education on data breach detection, notification and prevention.

Data Breach Today
APRIL 26, 2023
A group's newly dubbed "Educated Manticore" is sending Iraq-themed bait to coax deployment of an implant known as PowerLess. Iranian Threat Actor Deploys Improved PowerLess Backdoor Iranian hackers are deploying an updated backdoor apparently targeting Israeli academic researchers with an interest in Iraq.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
APRIL 14, 2023
Pakistan-Linked APT Group Using Spear-Phishing to Plant Info Stealer Malware A suspected Pakistan espionage threat actor that relies on phishing emails is expanding to the education sector after years of focusing on the Indian military and government.
Security Affairs
DECEMBER 26, 2023
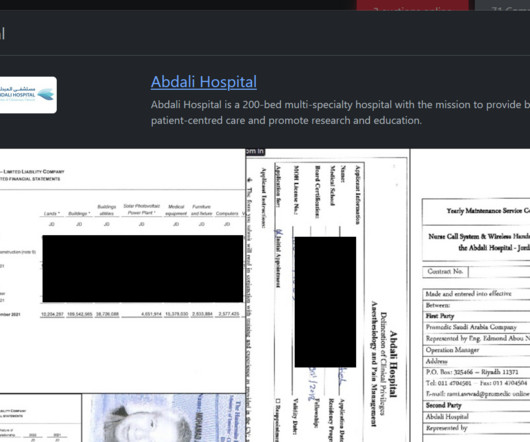
The Rhysida ransomware group claimed to have hacked Abdali Hospital, a multi-specialty hospital located in Jordan. The Rhysida ransomware group claimed to have breached the Abdali Hospital in Jordan and added it to the list of victims on its Tor leak site. The Rhysida ransomware group has been active since May 2023.

Data Breach Today
JUNE 26, 2023
Group Targeting Transportation, Construction, Government Agencies, CrowdStrike Says A Chinese state hacker is using novel tradecraft to gain initial access to victim systems, according to CrowdStrike.

Security Affairs
AUGUST 28, 2024
Iran-linked group APT33 used new Tickler malware in attacks against organizations in the government, defense, satellite, oil and gas sectors. The APT group conducted a cyber espionage campaign between April and July 2024 and used Microsoft’s Azure infrastructure for C2 infrastructure.

Data Breach Today
JUNE 12, 2022
Attacker Use DLL hijacking, DNS tunneling to Evade Post-Compromise Detection A recently identified Chinese hacking group dubbed "Aoqin Dragon" has been found to have targeted government, education and telecommunication organizations in Southeast Asia and Australia since 2013 as part of an ongoing cyberespionage campaign, according to research from (..)
Security Affairs
NOVEMBER 29, 2023
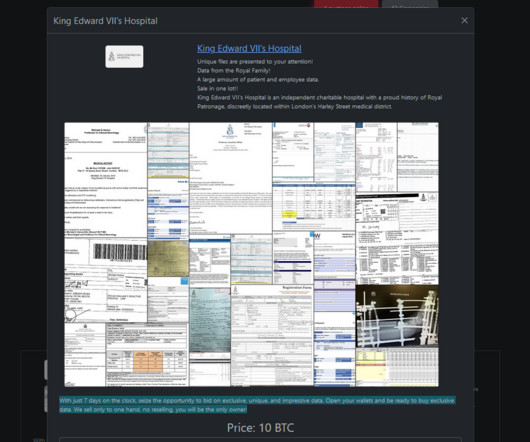
The Rhysida ransomware group claimed to have hacked King Edward VII’s Hospital in London. The Rhysida ransomware group claimed to have hacked King Edward VII’s Hospital in London and added it to the list of victims on its Tor leak site. The Rhysida ransomware group has been active since May 2023. Data from the Royal Family!
Krebs on Security
MAY 23, 2024
At least a dozen patriotic Russian hacking groups have been launching DDoS attacks since the start of the war at a variety of targets seen as opposed to Moscow. But by all accounts, few attacks from those gangs have come close to the amount of firepower wielded by a pro-Russia group calling itself “ NoName057(16).”
Security Affairs
NOVEMBER 21, 2023
Experts warn of a surge in NetSupport RAT attacks against education, government, and business services sectors. The most impacted sectors are education, government, and business services. In recent years, multiple threat actors, including the group TA569 , have been observed using the software as a Remote Access Trojan (RAT).
Security Affairs
AUGUST 7, 2024
The Rhysida Ransomware group claims to have breached Bayhealth Hospital in Delaware and offers alleged stolen data for 25 BTC. The Rhysida Ransomware group claims to have breached Bayhealth Hospital and added the hospital to the list of victims on its Tor leak site. The Rhysida ransomware group has been active since May 2023.

Krebs on Security
OCTOBER 14, 2021
Louis Post-Dispatch ran a story about how its staff discovered and reported a security vulnerability in a Missouri state education website that exposed the Social Security numbers of 100,000 elementary and secondary teachers. On Wednesday, the St. In a press conference this morning, Missouri Gov. ” Missouri Gov.
Security Affairs
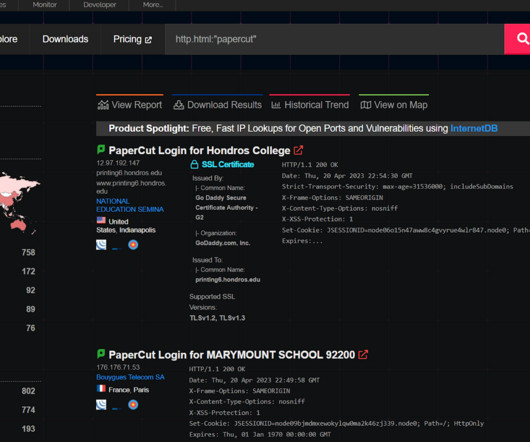
MAY 12, 2023
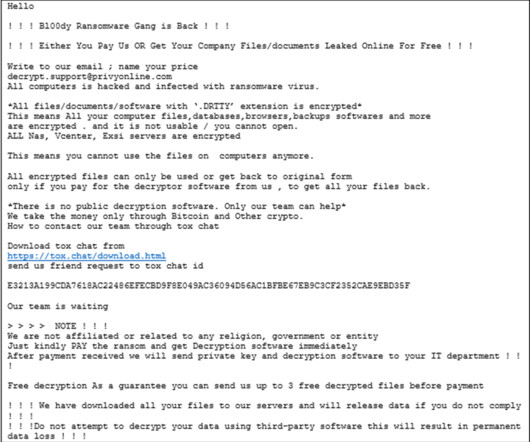
CISA and FBI warned of attacks conducted by the Bl00dy Ransomware Gang against the education sector in the country. The FBI and CISA issued a joint advisory warning that the Bl00dy Ransomware group is actively targeting the education sector by exploiting the PaperCut remote-code execution vulnerability CVE-2023-27350.

Security Affairs
AUGUST 6, 2023
The Colorado Department of Higher Education (CDHE) finally disclosed a data breach impacting students, past students, and teachers after the June attack. In June a ransomware attack hit the Colorado Department of Higher Education (CDHE), now the organization disclosed a data breach.

Krebs on Security
MAY 14, 2021
The crime gang announced it was closing up shop after its servers were seized and someone drained the cryptocurrency from an account the group uses to pay affiliates. “A number of the operators will most likely operate in their own closed-knit groups, resurfacing under new names and updated ransomware variants.

Krebs on Security
MARCH 2, 2021
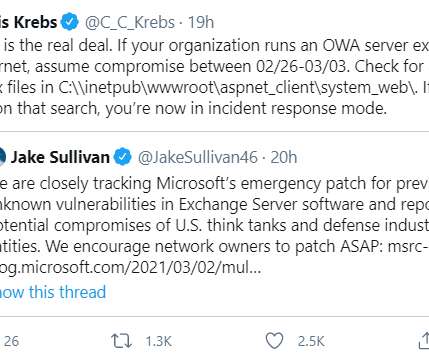
The company says all four flaws are being actively exploited as part of a complex attack chain deployed by a previously unidentified Chinese cyber espionage group. Microsoft Corp. Microsoft credited researchers at Reston, Va. based Volexity for reporting the attacks. “These flaws are very easy to exploit,” Adair said.
Krebs on Security
DECEMBER 8, 2022
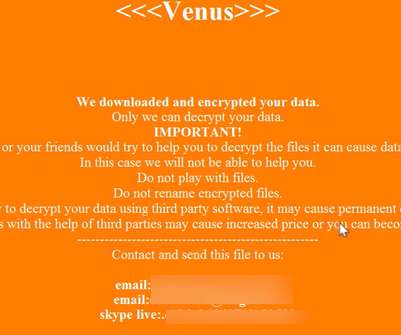
Ransomware groups are constantly devising new methods for infecting victims and convincing them to pay up, but a couple of strategies tested recently seem especially devious. Holden’s team gained visibility into discussions among members of two different ransom groups: CLOP (a.k.a. “ Cl0p ” a.k.a. Last month, the U.S.
Krebs on Security
MARCH 5, 2021
The espionage group is exploiting four newly-discovered flaws in Microsoft Exchange Server email software, and has seeded hundreds of thousands of victim organizations worldwide with tools that give the attackers total, remote control over affected systems. Microsoft’s initial advisory about the Exchange flaws credited Reston, Va.
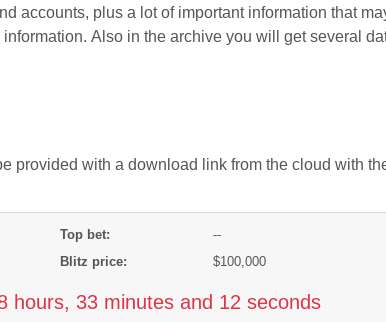
Krebs on Security
JUNE 2, 2020
The criminal group behind the REvil ransomware enterprise has begun auctioning off sensitive data stolen from companies hit by its malicious software. A partial screenshot from the REvil ransomware group’s Dark Web blog. “Others have gotten the message about the need for good backups, and probably don’t need to pay.

Krebs on Security
AUGUST 5, 2024
A ransomware group called Dark Angels made headlines this past week when it was revealed the crime group recently received a record $75 million data ransom payment from a Fortune 50 company. ThreatLabz found Dark Angels has conducted some of the largest ransomware attacks to date, and yet little is known about the group.

Security Affairs
FEBRUARY 3, 2022
Our old Twitter account, which was suspended, had pretty much many attacks on government agencies, corporations, educational institutions, ministries, and many, many other things around the world (which we still do, just on a smaller scale). We are a really mixed group. How were you born and approximately how many you are?

eSecurity Planet
SEPTEMBER 22, 2022
To accelerate the ransomware encryption process and make it harder to detect, cybercriminal groups have begun using a new technique: intermittent encryption. Sentinel Labs reported the new trend earlier this month, as ransomware groups have adopted the latest technology. Some are written on Go and can be customized.
Krebs on Security
FEBRUARY 26, 2023
Media coverage understandably focused on GoDaddy’s admission that it suffered three different cyberattacks over as many years at the hands of the same hacking group. But it’s worth revisiting how this group typically got in to targeted companies: By calling employees and tricking them into navigating to a phishing website.

Security Affairs
APRIL 20, 2023
Russia-linked threat actors launched large-volume phishing campaigns against hundreds of users in Ukraine to gather intelligence and aimed at spreading disinformation, states Google’s Threat Analysis Group (TAG). The group is also the author of the NotPetya ransomware that hit hundreds of companies worldwide in June 2017.

Krebs on Security
JUNE 30, 2021
One fraud-fighting group is intercepting hundreds to thousands of these per day. For the past year, BWare has maintained contact with an insider from the criminal group that’s been sending daily lists of would-be victims who are to receive counterfeit checks printed using the real bank account information of legitimate companies.
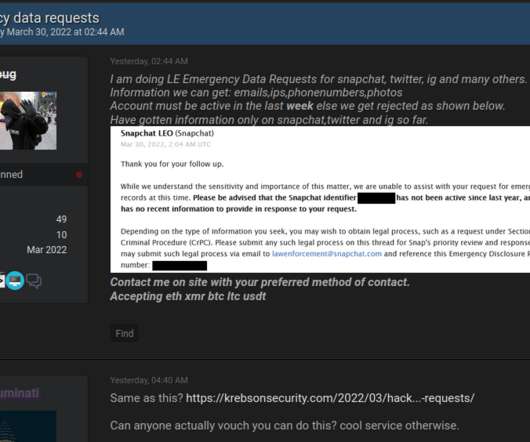
Krebs on Security
MARCH 31, 2022
” Tuesday’s story showed how fraudulently obtained EDRs were a tool used by members of LAPSUS$ , the data extortion group that recently hacked Microsoft , NVIDIA , Okta and Samsung. And it tracked the activities of a teenage hacker from the United Kingdom who was reportedly arrested multiple times for sending fake EDRs.

Security Affairs
APRIL 18, 2023
Citizen Lab reported that Israeli surveillance firm NSO Group used at least three iOS zero-click exploits in 2022. A new report from Citizen Lab states that the Israeli surveillance firm NSO Group used at least three zero-click zero-day exploits to deliver its Pegasus spyware. ” reads the report. ” reads the report.

Krebs on Security
NOVEMBER 22, 2021
George’s team confirmed that Medayedupin had around USD $2,000 to his name, which he’d recently stolen from a group of Nigerian fraudsters who were scamming people for gift cards. Ronnie Tokazowski is a threat researcher at Agari , a security firm that has closely tracked many of the groups behind BEC scams.
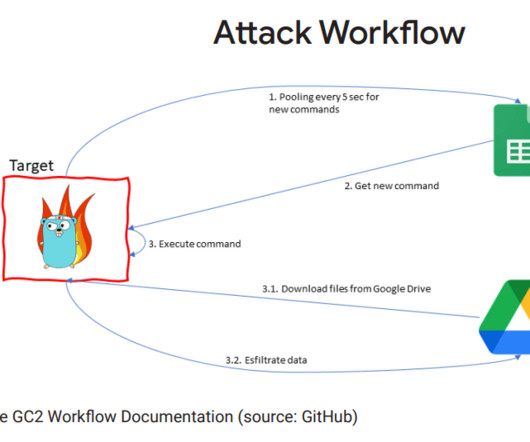
Security Affairs
APRIL 17, 2023
China-linked APT41 group used the open-source red teaming tool GC2 in an attack against a Taiwanese media organization. Google Threat Analysis Group (TAG) team reported that the China-linked APT41 group used the open-source red teaming tool Google Command and Control ( GC2 ) in an attack against an unnamed Taiwanese media organization.

Security Affairs
JUNE 26, 2023
China-linked APT group VANGUARD PANDA, aka Volt Typhoon, was spotted observing a novel tradecraft to gain initial access to target networks. CrowdStrike researchers observed the China-linked APT group VANGUARD PANDA, aka Volt Typhoon , using a novel tradecraft to gain initial access to target networks. ” concludes the report.
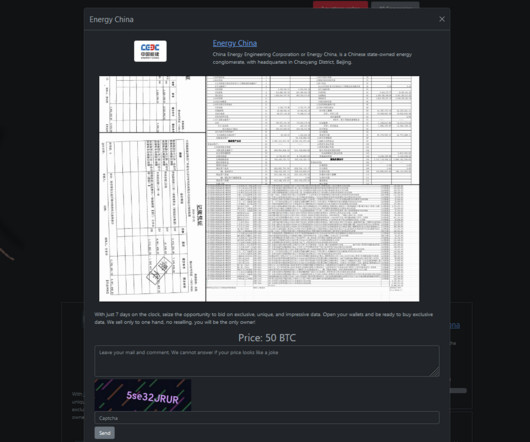
Security Affairs
NOVEMBER 25, 2023
The Rhysida ransomware group claimed to have hacked the Chinese state-owned energy conglomerate China Energy Engineering Corporation. China Energy Engineering Group ranks 3rd in ENR Top 150 Global Engineering Design Firms and 13th in ENR Top 250 Global Contractors. The Rhysida ransomware group has been active since May 2023.
Security Affairs
APRIL 24, 2023
Truebot has been active since 2017 and some researchers linked it to the Russian Silence Group , while a recent investigation linked it to threat actor TA505 (aka Evil Corp). It is interesting to note that the domain was also hosting malware a variant of the TrueBot malware.
Security Affairs
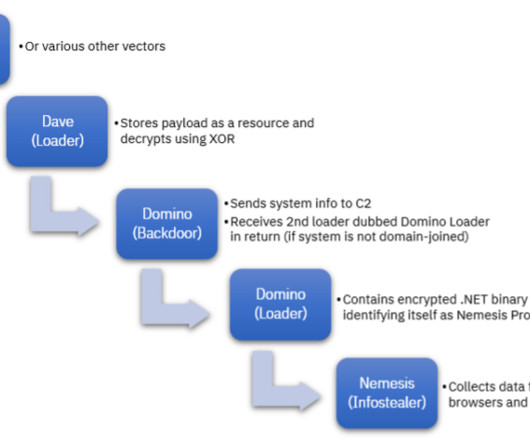
APRIL 18, 2023
A new malware, dubbed Domino, developed by the FIN7 cybercrime group has been used by the now-defunct Conti ransomware gang. IBM Security X-Force researchers recently discovered a new malware family, called Domino, which was created by developers associated with the FIN7 cybercriminal group (tracked by X-Force as ITG14).
Security Affairs
FEBRUARY 8, 2024
The Volt Typhoon group has been active since at least mid-2021 it carried out cyber operations against critical infrastructure. In the most recent campaign, the group targeted organizations in the communications, manufacturing, utility, transportation, construction, maritime, government, information technology, and education sectors.
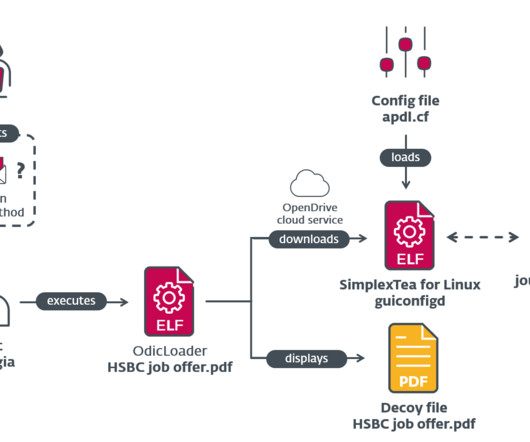
Security Affairs
APRIL 20, 2023
North Korea-linked APT group Lazarus employed new Linux malware in attacks that are part of Operation Dream Job. North Korea-linked APT group Lazarus is behind a new campaign tracked as Operation DreamJob (aka DeathNote or NukeSped ) that employed Linux malware.

Security Affairs
APRIL 22, 2024
Russia-linked APT28 group used a previously unknown tool, dubbed GooseEgg, to exploit Windows Print Spooler service flaw. Microsoft reported that the Russia-linked APT28 group (aka “ Forest Blizzard ”, “ Fancybear ” or “ Strontium ” used a previously unknown tool, dubbed GooseEgg, to exploit the Windows Print Spooler flaw CVE-2022-38028.
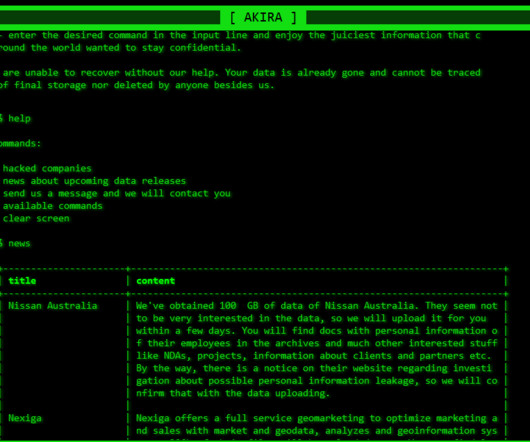
Security Affairs
FEBRUARY 17, 2024
The issue was listed by CISA as known to be used in ransomware campaigns, but the agency did not reveal which ransomware groups are actively exploiting the issue. In January, researchers from cybersecurity firm Truesec reported that the Akira ransomware group exploited the vulnerability in attacks targeting Cisco Cisco ASA and FTD appliances.

Krebs on Security
NOVEMBER 17, 2022
There are multiple examples of ransomware groups doing just that after security researchers crowed about finding vulnerabilities in their ransomware code. “The minute you announce you’ve got a decryptor for some ransomware, they change up the code,” James said.
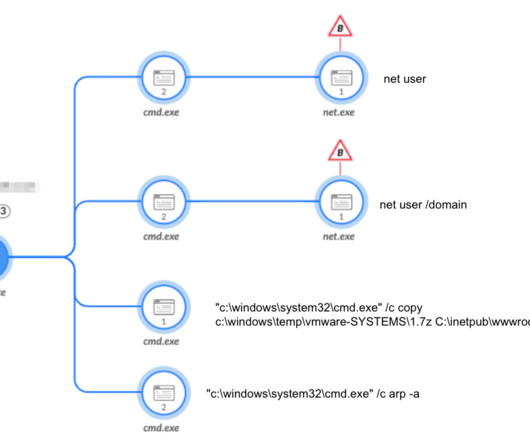
Security Affairs
NOVEMBER 7, 2023
Iran-linked Agonizing Serpens group has been targeting Israeli organizations with destructive cyber attacks since January. Based on our telemetry, the most targeted organizations belong to the education and technology sectors.” ” concludes the report that also includes indicators of compromise (IoCs).
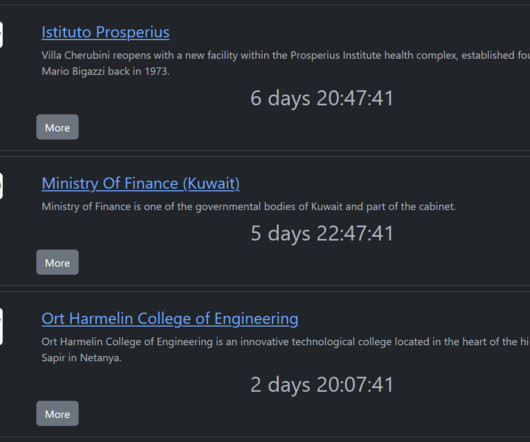
Security Affairs
NOVEMBER 15, 2023
The FBI and CISA warn of attacks carried out by the Rhysida ransomware group against organizations across multiple industry sectors. The report is part of the ongoing #StopRansomware effort that disseminates advisories about tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) associated with ransomware groups.

Security Affairs
APRIL 25, 2024
Cisa added the flaw to the KEV catalog after Microsoft reported that the Russia-linked APT28 group (aka “ Forest Blizzard ”, “ Fancybear ” or “ Strontium ” used a previously unknown tool, dubbed GooseEgg, to exploit the Windows Print Spooler flaw CVE-2022-38028.
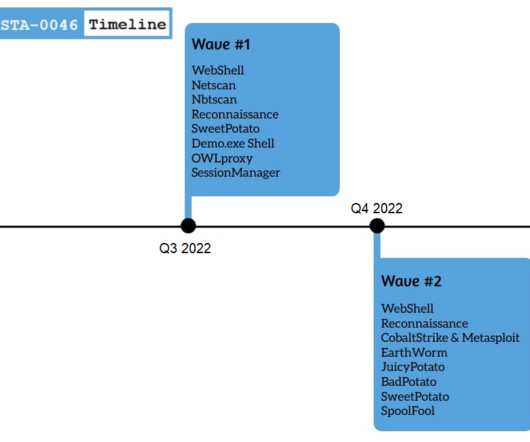
Security Affairs
SEPTEMBER 25, 2023
A stealthy APT group tracked as Gelsemium was observed targeting a Southeast Asian government between 2022 and 2023. Palo Alto Unit42 researchers an APT group tracked as Gelsemium targeting a Southeast Asian government. Gelsemium is a group focused on cyberespionage that has been active since at least 2014.
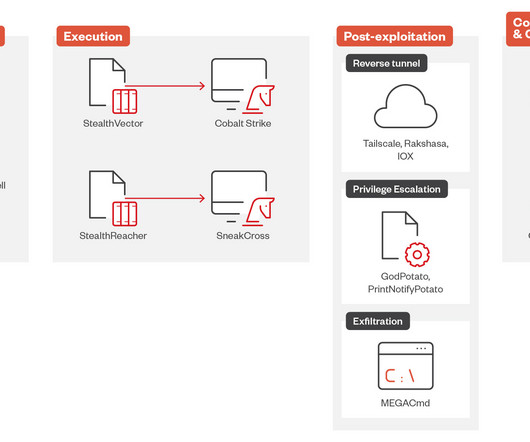
Security Affairs
AUGUST 14, 2024
China-linked APT group Earth Baku (a threat actor associated with APT41 ) has expanded its operations beyond the Indo-Pacific region to Europe, the Middle East, and Africa. The group targeted multiple industries, including media and communications, telecoms, technology, healthcare, and education and government entities.
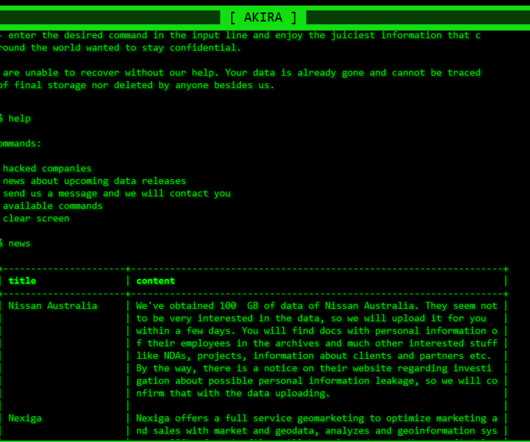
Security Affairs
DECEMBER 22, 2023
The Akira ransomware group announced it had breached the network of Nissan Australia, the Australian branch of the car maker giant. ” reads the message published by the group on its data leak site. Like other ransomware gangs, the group has developed a Linux encryptor to target VMware ESXi servers.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content