The Iowa Caucus Tech Meltdown Is a Warning
WIRED Threat Level
FEBRUARY 4, 2020
The Iowa results will come in eventually, thanks to a paper trail. But it underscores just how much can go wrong when you lean on unnecessary, untested tech.

WIRED Threat Level
FEBRUARY 4, 2020
The Iowa results will come in eventually, thanks to a paper trail. But it underscores just how much can go wrong when you lean on unnecessary, untested tech.

Dark Reading
FEBRUARY 4, 2020
For cities, states and towns, paying up is short-sighted and only makes the problem worse.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Threatpost
FEBRUARY 7, 2020
Downloads of files like images may be banned if they use HTTP connections - even if they are available from an HTTPS website.
Security Affairs
FEBRUARY 7, 2020
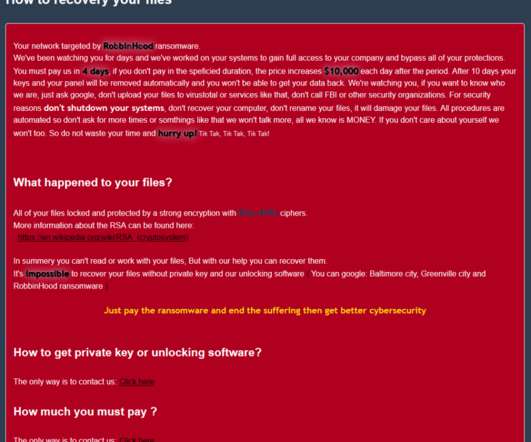
The operators behind the infamous RobbinHood ransomware are exploiting a vulnerable GIGABYTE driver to kill antivirus products. Cybercriminals behind the RobbinHood Ransomware are exploiting a vulnerable GIGABYTE driver to install a malicious and unsigned driver into Windows with the intent of disabling security products. Ransomware operators leverage a custom antivirus killing p ackage that is delivered to workstations to disable security solution before starting encryption.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.
Krebs on Security
FEBRUARY 5, 2020
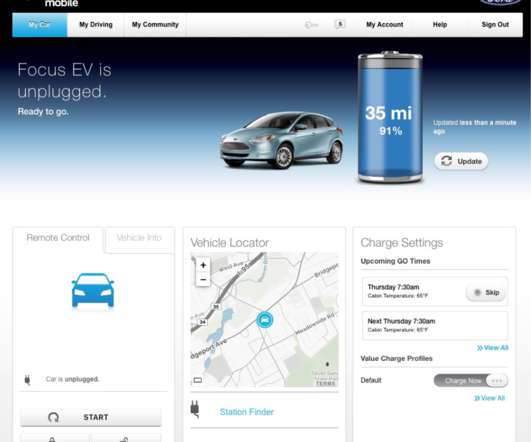
Many modern vehicles let owners use the Internet or a mobile device to control the car’s locks, track location and performance data, and start the engine. But who exactly owns that control is not always clear when these smart cars are sold or leased anew. Here’s the story of one former electric vehicle owner who discovered he could still gain remote, online access to his old automobile years after his lease ended.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
FEBRUARY 5, 2020
State Voter Registration Website Repeatedly Targeted The FBI reportedly warned this week that attackers repeatedly attempted to disrupt a state's voter registration and information website with a distributed denial-of-service attack.
Security Affairs
FEBRUARY 7, 2020
Japanese defense contractors Pasco and Kobe Steel have disclosed security breaches that they have suffered back in 2016 and 2018. Pasco is Japan’s largest geospatial provider and Kobe Steel is one of the major steel manufacturers. Just last week, Japan’s Ministry of Defense announced in addition to Mitsubishi Electric and the NEC defense business division other two unnamed contractors suffered a data breach.
Krebs on Security
FEBRUARY 4, 2020
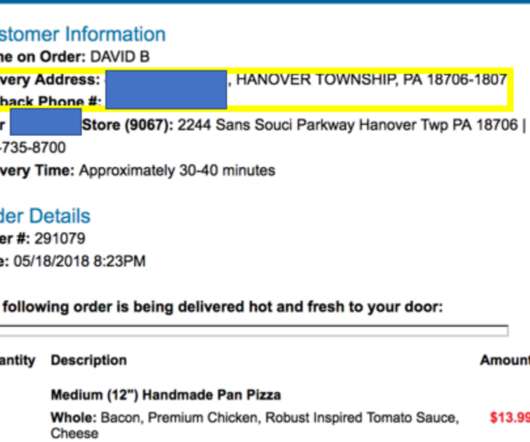
A Pennsylvania man who operated one of the Internet’s longest-running online attack-for-hire or “booter” services was sentenced to five years probation today. While the young man’s punishment was heavily tempered by his current poor health, the defendant’s dietary choices may have contributed to both his capture and the lenient sentencing: Investigators say the onetime booter boss’s identity became clear after he ordered a bacon and chicken pizza delivered to

WIRED Threat Level
FEBRUARY 3, 2020
With his "Google Maps Hack," artist Simon Weckert draws attention to the systems we take for granted—and how we let them shape us.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

Data Breach Today
FEBRUARY 6, 2020
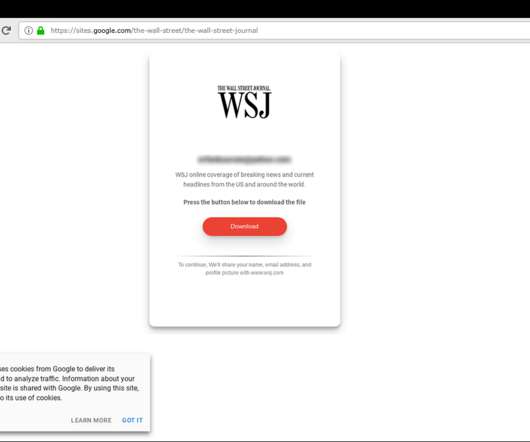
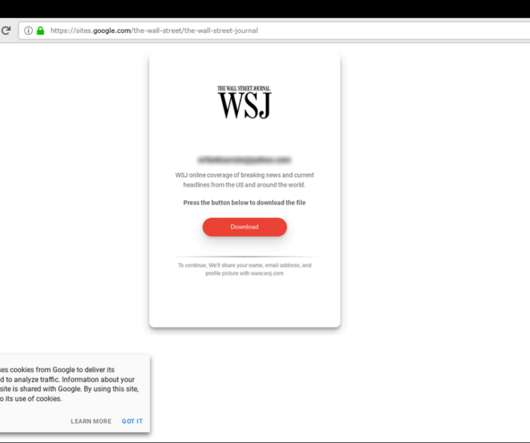
Inquiry Posing Interview Questions Designed to Steal Credentials In a recently discovered phishing campaign, hackers attempted to steal victims' passwords and credentials by posing as a former Wall Street Journal reporter and sending documents with potential interview questions, according to security firm Certfa.
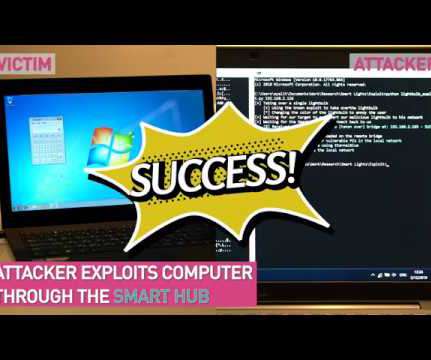
Security Affairs
FEBRUARY 6, 2020
Check Point experts discovered a high-severity flaw in Philips Hue Smart Light Bulbs that can be exploited to gain entry into a targeted WiFi network. Security experts from Check Point discovered a high-severity flaw ( CVE-2020-6007 ) in Philips Hue Smart Light Bulbs that can be exploited by hackers to gain entry into a targeted WiFi network. Lightbulbs could be remotely controlled through a mobile app or via a digital home assistant, owners could control the light in the environment and even

erwin
FEBRUARY 6, 2020
As organizations deal with managing ever more data, the need to automate data management becomes clear. Last week erwin issued its 2020 State of Data Governance and Automation (DGA) Report. The research from the survey suggests that companies are still grappling with the challenges of data governance — challenges that will only get worse as they collect more data.

WIRED Threat Level
FEBRUARY 3, 2020
EKANS appears to be the work of cybercriminals, rather than nation-state hackers—a worrying development, if so.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Data Breach Today
FEBRUARY 7, 2020
Privacy Rules Remain in Effect Pending Eventual Outcome of UK-EU Negotiations As former U.K. Prime Minister Theresa May famously declared: "Brexit means Brexit." But what Britain's exit from the EU means for the nation's data privacy rules and future EU-U.K. data flows remains to be seen, as the country navigates its post-Brexit transition period.

Security Affairs
FEBRUARY 7, 2020
Google addressed a critical vulnerability in its Android OS that affects the Bluetooth subsystem and could be exploited without user interaction. Google has addressed a critical flaw in Android OS that affects the Bluetooth subsystem and could be exploited without user interaction. The vulnerability tracked as CVE-2020-0022 is a remote code execution flaw that could allow attackers to execute code on the device with the elevated privileges of the Bluetooth daemon when the wireless module is acti

Thales Cloud Protection & Licensing
FEBRUARY 4, 2020
The traditional focus on security has been on breach prevention and threat detection but these can only go so far. For organisations going through digital transformation there needs to be a layered approach to security – complimenting these traditional strategies with data protection.In the evolving digital world of cloud, social and apps, data is now the perimeter.

WIRED Threat Level
FEBRUARY 5, 2020
Five vulnerabilities in Cisco Discovery Protocol make it possible for a hacker to take over desk phones, routers, and more. .

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Data Breach Today
FEBRUARY 6, 2020
Sites Fraudulently Offered Government Services for a Fee, Commission Says After winning court approval this week, the Federal Trade Commission shuttered over 200 websites that it says fraudulently claimed to offer government services, such as drivers' license renewals or verification of public benefits, for a fee.

Security Affairs
FEBRUARY 4, 2020
Google has accidentally shared private videos of some users that were stored on its servers with other, the tech giant notified impacted users. Google admitted a new privacy incident, it has accidentally shared private videos saved on its servers with other users. At the time it is not clear the number of impacted users, anyway, the company sent them a security notification.

AIIM
FEBRUARY 6, 2020
Reaching your Digital Transformation goals often requires the addition of new software solutions. But, shopping around for software can be a challenge. How are organizations expected to fully assess the precision of one software system/solution and compare it to another? Are we expected to become experts on each option? In our personal lives, when we shop for something like a new pair of shoes, we try on different brands and sizes to see what fits best for our needs.

WIRED Threat Level
FEBRUARY 4, 2020
Your digital self is fragmented and owned by third parties. Kaliya Young has a plan to change that—and make tech fairer for all.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

Data Breach Today
FEBRUARY 7, 2020
Attorney General Calls for Supporting Huawei's Competitors to Help Boost 5G Security U.S. Attorney General William Barr says the United States and its allies should take a "controlling stake" in Huawei's chief competitors, Findland's Nokia and Sweden's Ericsson, to help make them more viable and improve the security of emerging 5G networks.

Security Affairs
FEBRUARY 5, 2020
Microsoft published an interesting report that investigates web shell attacks, the IT giant says it detects 77,000 active web shells daily. According to a report published by Microsoft, the company detects an average of 77,000 active web shells, spreading across 46,000 infected servers, on a daily base. A web shell is a code, often written in typical web development programming languages (e.g., ASP, PHP, JSP), that attackers implant on web servers to gain remote access and code execution.

Adam Levin
FEBRUARY 7, 2020
Online scammers are using the 2020 Oscars to spread malware. A recent study released by Kaspersky Labs uncovered several hacking and phishing campaigns promising their targets free and early access to Best Picture nominees for this year’s Academy Awards. The study found over twenty phishing websites hosting at least 925 malicious files using the movies as bait, requiring would-be victims to either provide personal information (including credit card numbers), or to install adware applications to

WIRED Threat Level
FEBRUARY 6, 2020
The nation’s first primary is proudly low-tech, but it'll take more than paper ballots to defuse the disinformation threat.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Data Breach Today
FEBRUARY 3, 2020
Lessons Learned from WannaCry and Other Attacks The National Institute of Standards and Technology has unveiled a pair of draft practice guidelines that offer updated advice and best practices on how to protect the confidentiality, integrity and availability of data in light of increasing threats from ransomware and other large-scale cyber events.
Security Affairs
FEBRUARY 7, 2020
Iran-linked APT group Charming Kitten has been targeting journalists, political and human rights activists in a new campaign. Researchers from Certfa Lab reports have spotted a new cyber espionage campaign carried out by Iran-linked APT group Charming Kitten that has been targeting journalists, political and human rights activists. Iran-linked Charming Kitten group, (aka APT35 , Phosphorus , Newscaster , and Ajax Security Team) made the headlines in 2014 when experts at iSight issued a report de

Jamf
FEBRUARY 3, 2020
This year's global education technology show Bett has a lot of gadgets and flash. But do they actually impact education?
Let's personalize your content