LastPass Data Breach: It's Time to Ditch This Password Manager
WIRED Threat Level
DECEMBER 28, 2022
The password manager's most recent data breach is so concerning, users need to take immediate steps to protect themselves.
WIRED Threat Level
DECEMBER 28, 2022
The password manager's most recent data breach is so concerning, users need to take immediate steps to protect themselves.

Data Breach Today
DECEMBER 26, 2022
APT Groups Use 500 Decoy Domains of Popular NFT, DeFi Platforms North Korean attackers are using phishing websites to impersonate popular NFT platforms and DeFi marketplaces to steal digital assets worth hundreds of thousands of dollars. They set up nearly 500 decoy sites, including that of a project associated with the World Cup and NFT marketplace OpenSea.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dark Reading
DECEMBER 29, 2022
How CISOs handle the ethical issues around data breaches can make or break their careers. Don't wait until a breach happens to plot the course forward.

Security Affairs
DECEMBER 25, 2022
Threat actors are actively exploiting a critical flaw in the YITH WooCommerce Gift Cards Premium WordPress plugin installed by over 50,000 websites. Hackers are actively exploiting a critical vulnerability, tracked as CVE-2022-45359 (CVSS v3: 9.8), affecting the WordPress plugin YITH WooCommerce Gift Cards Premium. The YITH WooCommerce Gift Cards Premium plugin allows websites of online stores to sell gift cards, a WordPress plugin used on over 50,000 websites.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.
WIRED Threat Level
DECEMBER 29, 2022
The year was marked by sinister new twists on cybersecurity classics, including phishing, breaches, and ransomware attacks.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
DECEMBER 28, 2022
Russia Continued Its Cyber Offensive With an Average of 10 Cyberattacks a Day Ukraine's domestic intelligence agency revealed this week that it successfully blocked more than 4,500 cyberattacks in 2022. The number of cyberattacks has tripled since last year and has grown fivefold since 2020, the domestic intelligence agency's cyber division chief says.

Security Affairs
DECEMBER 30, 2022
The website for the Port of Lisbon is still down days after it was the target of a ransomware attack claimed by Lockbit group. The Port of Lisbon is the third-largest port in Portugal and one of the main European ports due to its strategic location. The website of the port was hit by a cyber attack on December 25, in response to the security breach the administrators shut down it.

WIRED Threat Level
DECEMBER 30, 2022
Any multifactor authentication adds protection, but a physical token is the best bet when it really counts.

Schneier on Security
DECEMBER 30, 2022
Yet another smartphone side-channel attack: “ EarSpy: Spying Caller Speech and Identity through Tiny Vibrations of Smartphone Ear Speakers “: Abstract: Eavesdropping from the user’s smartphone is a well-known threat to the user’s safety and privacy. Existing studies show that loudspeaker reverberation can inject speech into motion sensor readings, leading to speech eavesdropping.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

Data Breach Today
DECEMBER 30, 2022
Website Remains Down Following Christmas Day Attack One of Europe's busiest ports is added to the list of LockBit ransomware victims. The hacking group targeted Portugal's Port of Lisbon on Christmas day, giving the facility a deadline of Jan.18 to pay a ransom of $1.5 million in exchange for their data deletion.

Security Affairs
DECEMBER 30, 2022
Netgear addressed a high-severity bug affecting multiple WiFi router models, including Wireless AC Nighthawk , Wireless AX Nighthawk (WiFi 6) , and Wireless AC. Netgear fixed a bug affecting multiple WiFi router models, including Wireless AC Nighthawk , Wireless AX Nighthawk (WiFi 6) , and Wireless AC router models. The vendor only said that the flaw is a pre-authentication buffer overflow vulnerability and urged customers to address the firmware of their devices as soon as possible.

WIRED Threat Level
DECEMBER 25, 2022
Ever-expanding cloud storage presents more risks than you might think.

Schneier on Security
DECEMBER 27, 2022
This is one way of ensuring that IT keeps up with patches : Albanian prosecutors on Wednesday asked for the house arrest of five public employees they blame for not protecting the country from a cyberattack by alleged Iranian hackers. Prosecutors said the five IT officials of the public administration department had failed to check the security of the system and update it with the most recent antivirus software.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Data Breach Today
DECEMBER 30, 2022
Agency Says It Has Temporary 'Exclusive Control' of Assets for Safe Custody The Bahamas Securities Commission seized digital assets worth $3.5 billion from local firm FTX Digital Markets. The regulator says the funds were at risk of "imminent dissipation" due to hack attacks, and will temporarily remain under its exclusive control, stored in secure digital wallets.

Security Affairs
DECEMBER 30, 2022
US CISA added TIBCO Software’s JasperReports vulnerabilities to its Known Exploited Vulnerabilities Catalog. US CISA added TIBCO Software’s JasperReports vulnerabilities, tracked as CVE-2018-5430 (CVSS score: 7.7) and CVE-2018-18809 (CVSS score: 9.9), to its Known Exploited Vulnerabilities ( KEV ) catalog, TIBCO JasperReports is an open-source Java reporting tool for creating and managing reports and dashboards.

WIRED Threat Level
DECEMBER 26, 2022
From SBF to the GRU, these were the most disruptive forces of online chaos this year.

KnowBe4
DECEMBER 27, 2022
Impersonating Facebook using its own platform against them, a new phishing attack takes advantage of victim’s inability to distinguish legitimate from illegitimate.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Data Breach Today
DECEMBER 29, 2022
Global Cyber Alliance CEO Philip Reitinger Shares Updates, Challenges Global Cyber Alliance CEO Philip Reitinger shares updates on the alliance's Internet Integrity and Capacity & Resilience programs, which tackle key challenges of internet infrastructure, privacy and safety. Success is measured by the number of partners and "who is using the platform," he says.
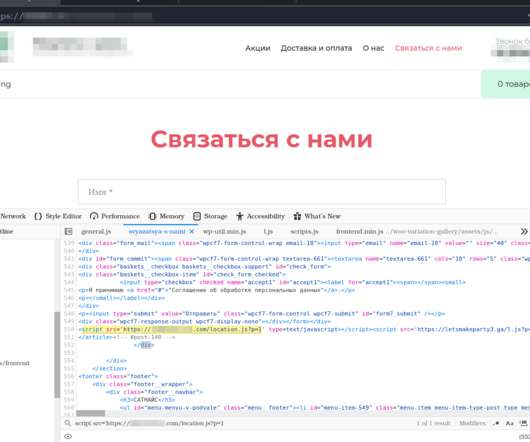
Security Affairs
DECEMBER 30, 2022
A new Linux malware has been exploiting 30 vulnerabilities in outdated WordPress plugins and themes to deploy malicious JavaScripts. Doctor Web researchers discovered a Linux malware, tracked as Linux.BackDoor.WordPressExploit.1, that compromises WordPress websites by exploiting 30 vulnerabilities in multiple outdated plugins and themes. The malware injects into targeted webpages malicious JavaScripts, then when users click on the compromised page, they are redirected to other sites under the c

WIRED Threat Level
DECEMBER 28, 2022
The Kremlin’s aggression in Ukraine is following a dangerous playbook that began to unfold years ago.

Dark Reading
DECEMBER 29, 2022
Attackers are harvesting credentials from compromised systems. Here's how some commonly used tools can enable this.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

Data Breach Today
DECEMBER 26, 2022
Effective testing of incident response plans continues to be a major weakness for many healthcare sector entities, especially those facing ransomware and other disruptive incidents, says Van Steel, a partner at consultancy LBMC Information Security.
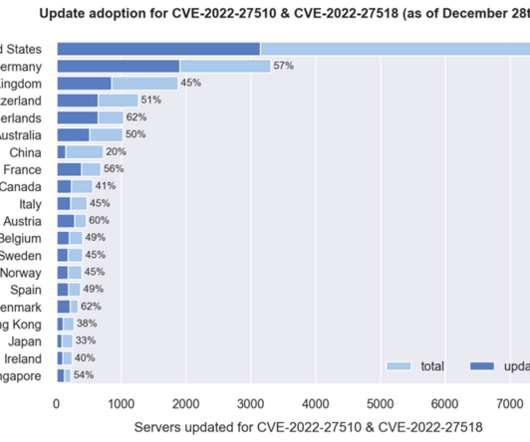
Security Affairs
DECEMBER 29, 2022
Researchers warn of thousands of Citrix Application Delivery Controller (ADC) and Gateway endpoints are still unpatched. NCC Group’s Fox-IT research team warns of thousands of Citrix ADC and Gateway endpoints remain vulnerable to two critical vulnerabilities, tracked as CVE-2022-27510 and CVE-2022-27518 (CVSS scores: 9.8), that the company addressed in recent months.

WIRED Threat Level
DECEMBER 24, 2022
Plus: An offensive US hacking operation, swatters hacking Ring cameras, a Netflix password-sharing crackdown, and more.

KnowBe4
DECEMBER 28, 2022
By Roger A. Grimes. KnowBe4 recommends that everyone use a password manager to create and use strong passwords as a part of their password policy [link].

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Data Breach Today
DECEMBER 25, 2022
Regulatory Pressure over Security, Privacy Mounts on Beleaguered Social Media Firm A member of a criminal data breach forum says he's selling email addresses and phone numbers of 400 million Twitter users. If verified, the data breach would be a further blow to Twitter and its beleaguered chief executive as regulators increase pressure over the firm's security practices.

Security Affairs
DECEMBER 29, 2022
The Lake Charles Memorial Health System (LCMHS) suffered a ransomware attack that impacted 270,000 patients. The Lake Charles Memorial Health System (LCMHS) disclosed a data breach that affected almost 270,000 patients at its medical centers. The Lake Charles Memorial Health System is the largest not-for-profit community healthcare system in Southwest Louisiana.

WIRED Threat Level
DECEMBER 27, 2022
Throughout 2022, geopolitics has given rise to a new wave of politically motivated attacks with an undercurrent of state-sponsored meddling.
Let's personalize your content