How to Avoid Phishing Emails and Scams
WIRED Threat Level
FEBRUARY 16, 2021
It's is a bigger threat than ever. Here are some ways you can defend yourself.

WIRED Threat Level
FEBRUARY 16, 2021
It's is a bigger threat than ever. Here are some ways you can defend yourself.
Data Breach Today
FEBRUARY 15, 2021
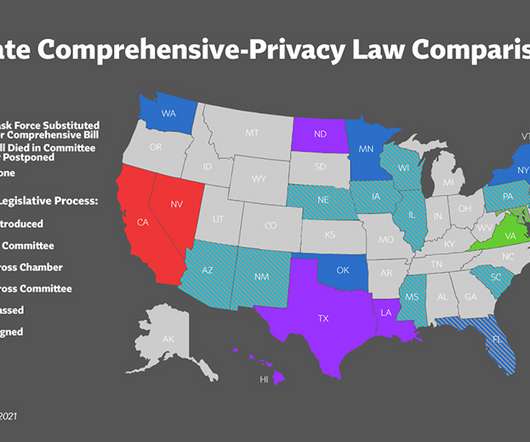
States Would Join 3 Others That Have Already Enacted Laws Five states are making progress this year toward passing privacy legislation along the lines of California's Consumer Privacy Act, according to the International Association of Privacy Professionals. Here's a status report.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

OpenText Information Management
FEBRUARY 17, 2021
Business and litigation go hand in hand in the 21st century. From litigation support personnel to the lawyers themselves, organizations face a common challenge: how to streamline processes and procedures to simplify and thoroughly respond to on-going litigation requests.
Security Affairs
FEBRUARY 18, 2021
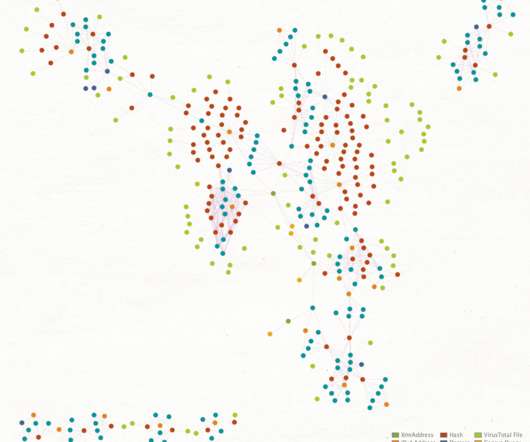
PaloAlto Network warns of the WatchDog botnet that uses exploits to take over Windows and Linux servers and mine cryptocurrency. Security researchers at Palo Alto Networks uncovered a cryptojacking botnet, tracked as WatchDog, that is targeting Windows and Linux systems. WatchDog is one of the largest and longest-lasting Monero cryptojacking operations uncovered by security experts, its name comes from the name of a Linux daemon called watchdogd.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Krebs on Security
FEBRUARY 15, 2021
As a total sucker for anything skimming-related, I was interested to hear from a reader working security for a retail chain in the United States who recently found Bluetooth-enabled skimming devices placed over top of payment card terminals at several stores. Interestingly, these skimmers interfered with the terminal’s ability to read chip-based cards, forcing customers to swipe the stripe instead.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

WIRED Threat Level
FEBRUARY 15, 2021
A French security agency warns that the destructively minded group has exploited an IT monitoring tool from Centreon.

Security Affairs
FEBRUARY 15, 2021
An international operation conducted in Ukraine and France lead to the arrest of criminals believed to be affiliated with the Egregor RaaS. Some affiliated with the Egregor RaaS , not the main ransomware gang, have been arrested as a result of a joint operation conducted by law enforcement in Ukraine and France. Authorities did not reveal the name of the suspects, according to France media the suspects are in contact with Egregor ransomware operators and provided logistical and financial support
Krebs on Security
FEBRUARY 19, 2021
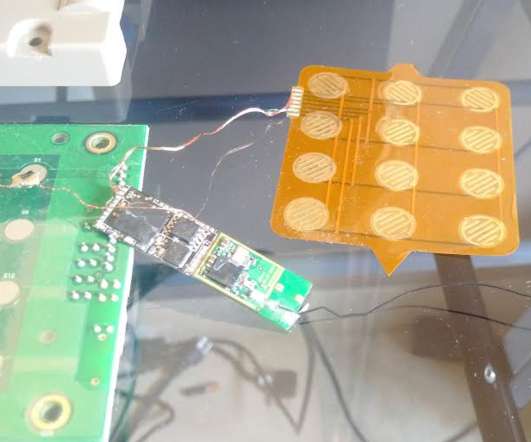
The leader of Mexico’s Green Party has been removed from office following allegations that he received money from a Romanian ATM skimmer gang that stole hundreds of millions of dollars from tourists visiting Mexico’s top tourist destinations over the past five years. The scandal is the latest fallout stemming from a three-part investigation into the organized crime group by KrebsOnSecurity in 2015.

Data Breach Today
FEBRUARY 16, 2021
Flaw Was Present in Microsoft Defender Since 2009, SentinelOne Finds Microsoft has patched a 12-year-old vulnerability in Microsoft Defender that, if exploited, could enable nonadministrative users to escalate privilege in the application. The patch was made after security firm SentinelOne recently notified Microsoft about the flaw.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

WIRED Threat Level
FEBRUARY 14, 2021
The lucrative business of dealing in code vulnerabilities is central to espionage and war planning, which is why brokers never spoke about it—until now.

Security Affairs
FEBRUARY 14, 2021
The FBI is warning companies about the use of out-of-date Windows 7 systems, desktop sharing software TeamViewer, and weak account passwords. The FBI issues this week a Private Industry Notification (PIN) alert to warn companies about the risks of using out-of-date Windows 7 systems, poor account passwords, and desktop sharing software TeamViewer. The alert comes after the recent attacks on the Oldsmar water treatment plant’s network where attackers tried to raise levels of sodium hydroxid

AIIM
FEBRUARY 18, 2021
What is the value of Records and Information Management? To help answer that, take a quick mental inventory of all the technologies your organization utilizes that interact in some way with organizational information. Think about technology like email, personal computers, the web, smart phones, social media, etc. Think about all of the information captured, stored, and created using those technologies.

Data Breach Today
FEBRUARY 15, 2021
Supply Chain Attack Likely Continues, He Tells '60 Minutes' More than 1,000 developers likely worked on rewriting code for the massive SolarWinds supply chain attack that affected many companies and U.S. government agencies, Microsoft President Brad Smith said in a Sunday interview, pointing out the attack is most likely continuing.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

WIRED Threat Level
FEBRUARY 17, 2021
Two distinct strains of malware have already adjusted to the new silicon just months after its debut.
Security Affairs
FEBRUARY 15, 2021
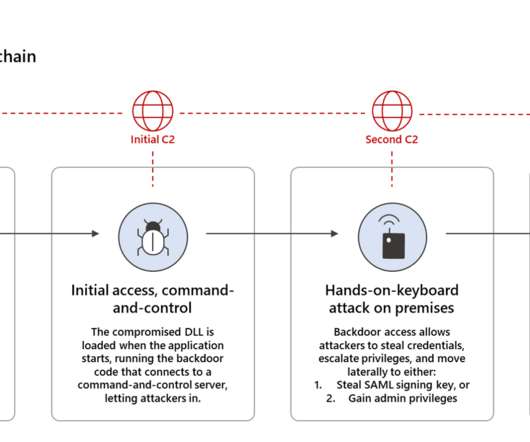
Microsoft says it found 1,000-plus developers’ fingerprints on the SolarWinds attack. Microsoft’s analysis of the SolarWinds supply chain attack revealed that the code used by the threat actors was the work of a thousand developers. Microsoft president Brad Smith provided further details about the investigation of the SolarWinds supply chain attack, the company’s analysis of the malicious code involved in the hack suggests it was the work of a thousand developers.

The Last Watchdog
FEBRUARY 15, 2021
Cybersecurity training has steadily gained traction in corporate settings over the past decade, and rightfully so. In response to continuing waves of data breaches and network disruptions, companies have made a concerted effort and poured substantial resources into promoting data security awareness among employees, suppliers and clients. Safeguarding data in workplace settings gets plenty of attention.

Data Breach Today
FEBRUARY 13, 2021
Breach Occurred After System Admin Granted Unauthorized Access Russian-Dutch multinational eCommerce company Yandex sustained a data breach in which 4,887 customer accounts were compromised after an unidentified employee with systems admin privileges gave unauthorized access to attackers.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
FEBRUARY 18, 2021
In its latest Platform Security Guide, Cupertino raised the curtain on the critical features that protect against hackers.
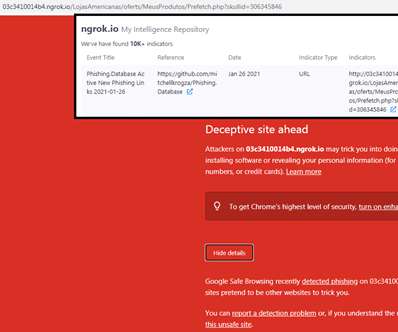
Security Affairs
FEBRUARY 16, 2021
Researchers from threat intelligence Cyble have discovered threat actors abusing the Ngrok platform in a fresh phishing campaign. Researchers at the threat intelligence firm Cyble discovered a new wave of phishing attacks targeting multiple organizations that are abusing the ngrok platform, a secure and introspectable tunnel to the localhost. ngrok is a cross-platform application used to expose a local development server to the Internet, the server appears to be hosted on a subdomain of ngrok (e

AIIM
FEBRUARY 16, 2021
The workplace in 2021 will demand a different set of skills. Now more than ever, organizations need to embrace disruption as a springboard for competitive advantage and adopt new ways of working that invigorate organizational performance. The needed capabilities include the ability to leverage remote work as an advantage, increase information agility, and drive business growth despite these challenging times.

Data Breach Today
FEBRUARY 17, 2021
Federal Prosecutors Say Hackers Work for Military Intelligence Unit Three North Koreans have been indicted for allegedly taking part in a criminal conspiracy to steal or extort $1.3 billion in cryptocurrency and cash from banks and other organizations around the world, the U.S. Justice Department announced Wednesday.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

WIRED Threat Level
FEBRUARY 17, 2021
The three men are allegedly part of a group that tried to steal $1.3 billion in an extended—and ongoing—cybercrime spree.

Security Affairs
FEBRUARY 19, 2021
A privacy bug in the Brave Browser caused the leak of the Tor onion URL addresses visited in the Tor mode by the users. A bug in the Private Window with Tor implemented in the Brave web browser could reveal the onion sites visited by the users. The Tor mode implemented in the Brave web browser allows users to access.onion sites inside Brave private browsing windows.

Schneier on Security
FEBRUARY 17, 2021
Interesting research on persistent web tracking using favicons. (For those who don’t know, favicons are those tiny icons that appear in browser tabs next to the page name.). Abstract: The privacy threats of online tracking have garnered considerable attention in recent years from researchers and practitioners alike. This has resulted in users becoming more privacy-cautious and browser vendors gradually adopting countermeasures to mitigate certain forms of cookie-based and cookie-less track

Data Breach Today
FEBRUARY 16, 2021
Reported Attempt at Stealing COVID-19 Data Comes in Wake of Global Warnings South Korean intelligence officials allege that North Korean hackers attempted to steal COVID-19 vaccine and treatment data by hacking the U.S. pharmaceutical firm Pfizer.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

WIRED Threat Level
FEBRUARY 13, 2021
The “big hack” redux, riot planning on Facebook, and more of the week's top security news.

Security Affairs
FEBRUARY 18, 2021
The OpenSSL Project addressed three vulnerabilities, including two denial-of-service (DoS) issues and a bug in the SSLv2 rollback protection. The OpenSSL Project released security patches to address three vulnerabilities, two denial-of-service (DoS) flaws, and an incorrect SSLv2 rollback protection issue. The fist vulnerability, tracked as CVE-2021-23841, is a NULL pointer dereference issue that can be exploited to cause a crash and trigger a DoS condition.

Schneier on Security
FEBRUARY 15, 2021
Vice is reporting on a new police hack: playing copyrighted music when being filmed by citizens, trying to provoke social media sites into taking the videos down and maybe even banning the filmers: In a separate part of the video, which Devermont says was filmed later that same afternoon, Devermont approaches [BHPD Sgt. Billy] Fair outside. The interaction plays out almost exactly like it did in the department — when Devermont starts asking questions, Fair turns on the music.
Let's personalize your content