Apple Tracks You More Than You Think
WIRED Threat Level
NOVEMBER 26, 2022
Plus: WikiLeaks’ website is falling apart, tax websites are sending your data to Facebook, and cops take down a big phone-number-spoofing operation.

WIRED Threat Level
NOVEMBER 26, 2022
Plus: WikiLeaks’ website is falling apart, tax websites are sending your data to Facebook, and cops take down a big phone-number-spoofing operation.

IG Guru
NOVEMBER 30, 2022
Check out the article here.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

IT Governance
DECEMBER 1, 2022
Welcome to our November 2022 review of data breaches and cyber attacks. We identified 95 security incidents throughout the month, accounting for 32,051,144 breached records. Almost half of that figure comes from two incidents. The first was a data breach at Twitter, in the latest PR disaster for the social media giant. Reports emerged late last week that user records were stolen using an API vulnerability that has since been fixed.
Krebs on Security
NOVEMBER 28, 2022
A recent scoop by Reuters revealed that mobile apps for the U.S. Army and the Centers for Disease Control and Prevention (CDC) were integrating software that sends visitor data to a Russian company called Pushwoosh , which claims to be based in the United States. But that story omitted an important historical detail about Pushwoosh: In 2013, one of its developers admitted to authoring the Pincer Trojan , malware designed to surreptitiously intercept and forward text messages from Android mob

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Data Breach Today
NOVEMBER 29, 2022
Firms Fear that Involving Police in Response Will Have Regulatory Consequences U.K. businesses shy from involving police in cyber incident response for fear of regulatory consequences, lawmakers sitting on Parliament's Joint Committee on National Security Strategy heard. Allowing businesses to anonymously disclose incidents would result in more data, suggested a witness.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
NOVEMBER 28, 2022
But Information Compiled by Other Attackers May Involve Millions of Other Accounts Information amassed on 5.4 million Twitter users by an attacker who abused one of the social network's APIs has been dumped online for free. While Twitter confirmed that breach, a researcher suggests other attackers also abused the feature to amass information for millions of other users.
Krebs on Security
DECEMBER 1, 2022
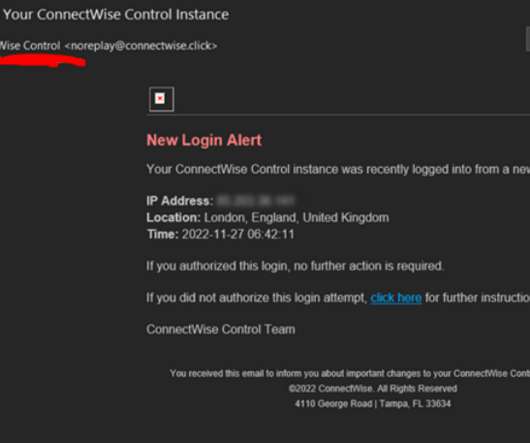
ConnectWise , which offers a self-hosted, remote desktop software application that is widely used by Managed Service Providers (MSPs), is warning about an unusually sophisticated phishing attack that can let attackers take remote control over user systems when recipients click the included link. The warning comes just weeks after the company quietly patched a vulnerability that makes it easier for phishers to launch these attacks.

Dark Reading
NOVEMBER 30, 2022
The simplicity and profitability of these attacks continue to appeal to threat actors a decade later.

Security Affairs
NOVEMBER 29, 2022
In today’s technological world, educating people about cybersecurity awareness is an absolute necessity. According to one report , 82% of data breaches involved the human element, from social attacks to misuse of technologies. These errors are not always entirely preventable, as some level of human error is inevitable, but proper training in cybersecurity awareness can greatly decrease the likelihood of human mistakes leading to data breaches.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

WIRED Threat Level
NOVEMBER 28, 2022
Google provided investigators with location data for more than 5,000 devices as part of the federal investigation into the attack on the US Capitol.

Data Breach Today
DECEMBER 2, 2022
Some Customers at Risk of Identity Theft, South Staffordshire Water Belatedly Warns Is a four-month delay between learning your systems were breached and notifying affected customers acceptable? After spotting an attack in August, private utility South Staffordshire Water in England is only beginning to alert customers that they're at risk of identity theft.

The Last Watchdog
NOVEMBER 27, 2022
Government assistance can be essential to individual wellbeing and economic stability. This was clear during the COVID-19 pandemic, when governments issued trillions of dollars in economic relief. Related: Fido champions passwordless authentication. Applying for benefits can be arduous, not least because agencies need to validate applicant identity and personal identifiable information (PII).

Security Affairs
DECEMBER 2, 2022
Qualys researchers demonstrated how to chain a new Linux flaw with two other two issues to gain full root privileges on an impacted system. Researchers at the Qualys’ Threat Research Unit demonstrated how to chain a new Linux vulnerability, tracked as CVE-2022-3328 , with two other flaws to gain full root privileges on an affected system. The vulnerability resides in the snap-confine function on Linux operating systems, a SUID-root program installed by default on Ubuntu.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

WIRED Threat Level
DECEMBER 2, 2022
Device manufacturers use “platform certificates” to verify an app’s authenticity, making them particularly dangerous in the wrong hands.

Data Breach Today
DECEMBER 1, 2022
Feds Warn Impermissible Disclosures of Patient Health Data is Prohibited Federal regulators issued a warning to healthcare entities and their tech vendors that the use of tracking code embedded in patient portals that transmits patient information to third-parties could be a violation of HIPAA, and punishable with monetary fines.

Schneier on Security
NOVEMBER 28, 2022
Laptop technicians routinely violate the privacy of the people whose computers they repair: Researchers at University of Guelph in Ontario, Canada, recovered logs from laptops after receiving overnight repairs from 12 commercial shops. The logs showed that technicians from six of the locations had accessed personal data and that two of those shops also copied data onto a personal device.
Security Affairs
DECEMBER 1, 2022
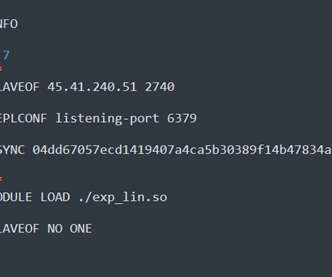
Redigo is a new Go-based malware employed in attacks against Redis servers affected by the CVE-2022-0543 vulnerability. Researchers from security firm AquaSec discovered a new Go-based malware that is used in a campaign targeting Redis servers. Threat actors are exploiting a critical vulnerability, tracked as CVE-2022-0543 , in Redis (Remote Dictionary Server) servers.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
NOVEMBER 30, 2022
Plus: Major patches dropped this month for Chrome, Firefox, VMware, Cisco, Citrix, and SAP.

Data Breach Today
DECEMBER 1, 2022
Australian Information Commissioner Will Investigate Insurer's Security Practices The Russia-based ransomware gang behind the hack of Australia's largest private health insurer says it posted a full set of stolen data. The Australian Information Commissioner said it will probe the insurer's personal information handling practices.

eSecurity Planet
DECEMBER 1, 2022
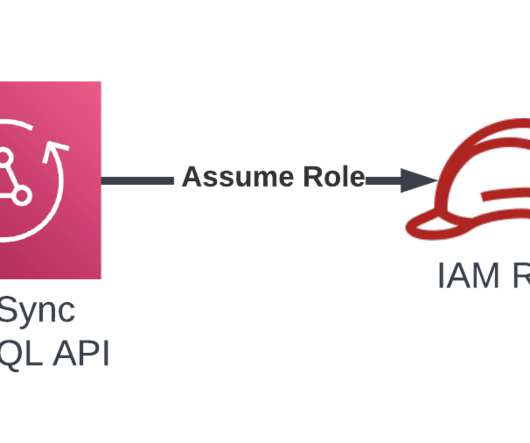
The Wiz Research Team recently discovered a supply chain vulnerability in IBM Cloud that they say is the first to impact a cloud provider’s infrastructure. In a dramatic flair, they named the flaw Hell’s Keychain. The security issues were reported to IBM Cloud in late August, and were patched in early September. Before it was patched, an attacker with knowledge of the vulnerability could run malicious code and modify data being stored by any IBM Cloud customer using PostgreSQL.
Security Affairs
NOVEMBER 28, 2022
Amazon Web Services (AWS) fixed a cross-tenant vulnerability that could have allowed attackers to gain unauthorized access to resources. Amazon Web Services (AWS) has addressed a cross-tenant confused deputy problem in its platform that could have allowed threat actors to gain unauthorized access to resources. The problem was reported to the company by researchers from Datadog on September 1, 2022, and the bug was solved on September 6.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

WIRED Threat Level
DECEMBER 1, 2022
As authorities hit citizens with more violence, the social network is proving key to documenting abuses. If it breaks, a human rights lifeline may disappear.

Data Breach Today
NOVEMBER 30, 2022
One Brooklyn Health Systems Three Hospitals Systems Affected by Nov. 19 Hack As three Brooklyn safety net hospitals grapple with the aftershocks of a Nov. 19 cyber incident, sources say other area hospitals are complaining about a lack of transparency. One Brooklyn Health System has been tight-lipped about the cause of the outage, which is suspected to involve ransomware.

Hunton Privacy
NOVEMBER 30, 2022
On November 15, 2022, the Italian Supreme Court held that an Italian court or competent data protection authority has jurisdiction to issue a global delisting order. A delisting order requires a search engine to remove certain search results about individuals if the data subject’s privacy interests prevail over the general right to expression and information, and the economic interest of the search engine.

Security Affairs
DECEMBER 2, 2022
Experts found multiple flaws in three Android Keyboard apps that can be exploited by remote attackers to compromise a mobile phone. Researchers at the Synopsys Cybersecurity Research Center (CyRC) warn of three Android keyboard apps with cumulatively two million installs that are affected by multiple flaws ( CVE-2022-45477, CVE-2022-45478, CVE-2022-45479, CVE-2022-45480, CVE-2022-45481, CVE-2022-45482, CVE-2022-45483 ) that can be exploited by attackers to compromise a mobile phone.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

WIRED Threat Level
NOVEMBER 29, 2022
With AlphaBay shuttered, Operation Bayonet enters its final phase: driving the site’s refugees into a giant trap. But one refugee hatched his own plan.

Data Breach Today
NOVEMBER 28, 2022
Fine Tied to Data Scrapping Incident Revealed in 2021 Facebook will pay a 265 million euro fine to the Irish data protection authority to resolve a 2021 incident when the scrapped data of 533 million users appeared online. The data contained names, phone numbers and birth dates. Facebook says it takes active measures against data scrapping.

KnowBe4
NOVEMBER 30, 2022
Every holiday season brings on an increase in gift card scams. Most people love to buy and use gift cards. They are convenient, easy to buy, easy to use, easy to gift, usually allow the receiver to pick just what they want, and are often received as a reward for doing something. The gift card market is estimated in the many hundreds of BILLIONS of dollars.
Let's personalize your content