IoT Attacks Skyrocket, Doubling in 6 Months
Threatpost
SEPTEMBER 6, 2021
The first half of 2021 saw 1.5 billion attacks on smart devices, with attackers looking to steal data, mine cryptocurrency or build botnets.

Threatpost
SEPTEMBER 6, 2021
The first half of 2021 saw 1.5 billion attacks on smart devices, with attackers looking to steal data, mine cryptocurrency or build botnets.

eSecurity Planet
SEPTEMBER 10, 2021
In a year where ransomware has raised the alert levels everywhere, the go-to answer from many is redundancy through offline, remote backups – but are they enough? Backups are a critical component of any enterprise cybersecurity posture, but they are not an airtight strategy. Like any other digital machine, backup systems are vulnerable to data loss and compromise.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Troy Hunt
SEPTEMBER 9, 2021
111 years ago almost to the day, a murder was committed which ultimately led to the first criminal trial to use fingerprints as evidence. We've all since watched enough crime shows to understand that fingerprints are unique personal biometric attributes and to date, no two people have ever been found to have a matching set. As technology has evolved, fingers (and palms and irises and faces) have increasingly been used as a means of biometric authentication.
Security Affairs
SEPTEMBER 9, 2021
The massive DDoS attack that has been targeting the internet giant Yandex was powered b a completely new botnet tracked as M?ris. The Russian Internet giant Yandex has been targeting by the largest DDoS attack in the history of Runet, the Russian Internet designed to be independent of the world wide web and ensure the resilience of the country to an internet shutdown.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Krebs on Security
SEPTEMBER 8, 2021
Microsoft Corp. warns that attackers are exploiting a previously unknown vulnerability in Windows 10 and many Windows Server versions to seize control over PCs when users open a malicious document or visit a booby-trapped website. There is currently no official patch for the flaw, but Microsoft has released recommendations for mitigating the threat.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

AIIM
SEPTEMBER 7, 2021
What is Information Governance, and Why is it Important? There are many benefits to constructing an Information Governance program plan. Generally, regulatory compliance or litigation activities are at the top of the list and often spur the creation of the IG program itself, but that's just the start of the list of IG benefits. In addition, a well-designed IG program can provide cost savings from better IT and information storage utilization, business agility, analytics, collaboration, and profi
Security Affairs
SEPTEMBER 5, 2021
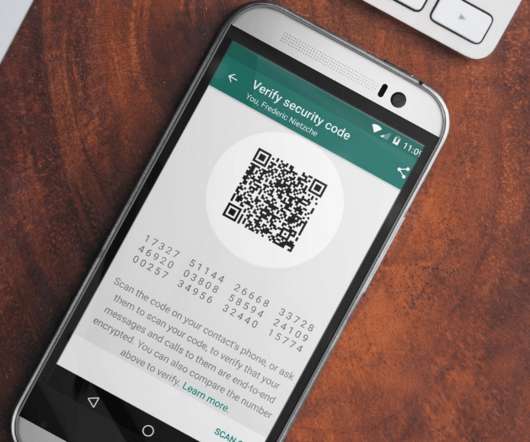
The Irish Data Protection Commission has fined WhatsApp €225 million over data sharing transparency for European Union users’ data with Facebook. The Irish Data Protection Commission has fined WhatsApp €225 million for the lack of transparency on how it shares European Union users’ data with Facebook companies. The instant messaging company violated the actual General Data Protection Regulation (GDPR). “The Data Protection Commission (DPC) has today announced a conclusion to a
Krebs on Security
SEPTEMBER 10, 2021
On Thursday evening, KrebsOnSecurity was the subject of a rather massive (and mercifully brief) distributed denial-of-service (DDoS) attack. The assault came from “ Meris ,” the same new “Internet of Things” (IoT) botnet behind record-shattering attacks against Russian search giant Yandex this week and internet infrastructure firm Cloudflare earlier this summer.
Data Breach Today
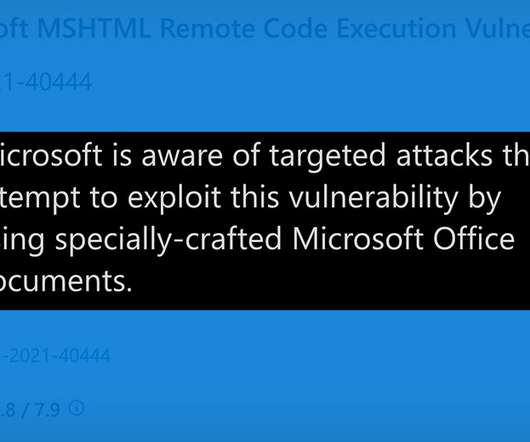
SEPTEMBER 8, 2021
Workarounds Detailed to Block Active Attack; Microsoft Has Yet to Release Patches Attackers are actively exploiting a flaw in Microsoft Windows for which no patch is yet available. Microsoft has issued workarounds and mitigations designed to block the zero-day attack for the flaw in the MSHTML browsing engine, which is being exploited via malicious Microsoft Office documents.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

WIRED Threat Level
SEPTEMBER 4, 2021
Plus: A spyware ban, a big WhatsApp fine, and more of the week's top security news.
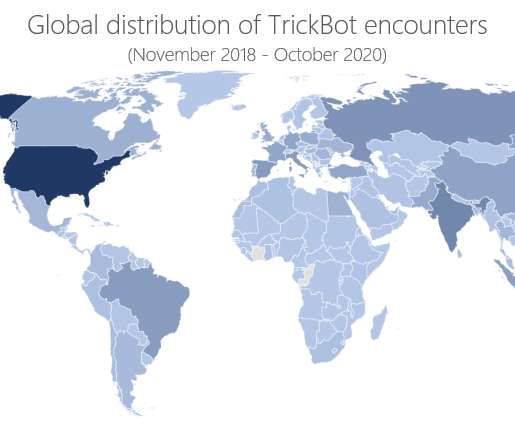
Security Affairs
SEPTEMBER 6, 2021
A Russian man accused of being a member of the infamous TrickBot gang was arrested while trying to leave South Korea. A Russian man accused of being a member of the TrickBot gang was arrested last week at the Seoul international airport. The man has remained stuck in the Asian country since February 2020 due to the COVID-19 lockdown imposed by the local government and the cancelation of international travel.
Krebs on Security
SEPTEMBER 6, 2021
In May 2015, KrebsOnSecurity briefly profiled “ The Manipulaters ,” the name chosen by a prolific cybercrime group based in Pakistan that was very publicly selling spam tools and a range of services for crafting, hosting and deploying malicious email. Six years later, a review of the social media postings from this group shows they are prospering, while rather poorly hiding their activities behind a software development firm in Lahore that has secretly enabled an entire generation of
Data Breach Today
SEPTEMBER 6, 2021
Revenue, Size, Geography and Level of Access Help Determine Sale Price for Access The most sought-after type of victim for ransomware-wielding attackers is a large, U.S.-based business with at least $100 million in revenue, not operating in the healthcare or education sector, with remote access available via remote desktop protocol or VPN credentials, threat intelligence firm Kela reports.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

WIRED Threat Level
SEPTEMBER 10, 2021
The ubiquitous messaging service will add end-to-end encryption to backups, keeping your chats safe no matter whose cloud they're stored in.

Security Affairs
SEPTEMBER 10, 2021
Microsoft has fixed the Azurescape issue, a flaw in Azure Container Instances that allows to take over containers of other platform users. Microsoft has addressed a vulnerability in Azure Container Instances (ACI) called Azurescape that could have allowed a malicious container to take over containers belonging to other users. An attacker could exploit the vulnerability to execute commands in the containers of other users and access to their data.

Troy Hunt
SEPTEMBER 6, 2021
For the last few years, I've been welcome national governments to Have I Been Pwned (HIBP) and granting them full and free access to domain-level searches via a dedicated API. Today, I'm very happy to welcome the Czech Republic's National Cyber and Information Security Agency who can now query their government domains along with the 26 other nations that have come before them.

Data Breach Today
SEPTEMBER 4, 2021
Flaws Fixed, Mitigations Issued for Discontinued Devices SEC Consult reportedly found multiple vulnerabilities in Moxa devices used in critical infrastructures including railways, manufacturing, cellular and heavy industries. Moxa has confirmed patching 60 vulnerabilities in its latest firmware update and issued mitigation advice for discontinued devices.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
SEPTEMBER 8, 2021
The email service says it was unable to appeal a Swiss court’s demand to log the IP address of a French climate advocate.
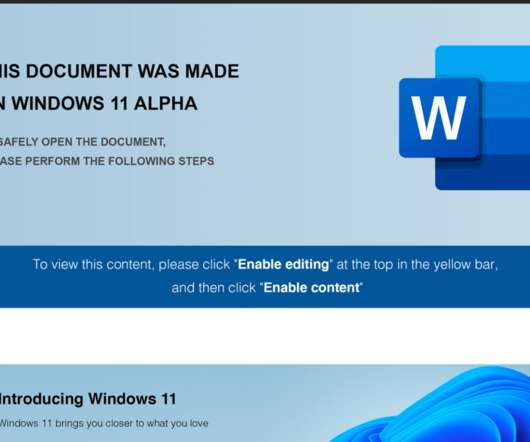
Security Affairs
SEPTEMBER 4, 2021
FIN7 cybercrime gang used weaponized Windows 11 Alpha-themed Word documents to drop malicious payloads, including a JavaScript backdoor. Anomali Threat Research experts have monitored recent spear-phishing attacks conducted by financially motivated threat actor FIN7. The messages used weaponized Windows 11 Alpha-themed Word documents with Visual Basic macros to drop malicious payloads, including a JavaScript backdoor, in an attack aimed at a US point-of-sale (PoS) service provider.

eSecurity Planet
SEPTEMBER 10, 2021
Palo Alto Networks (PANW) is bringing its enterprise-class security to small business and home markets with Okyo , a Wi-Fi 6 hardware device announced today. At $349 a year, the security and router system seems attractively priced for small businesses and companies looking to secure remote workers , who have surged in number since the start of the Covid pandemic 18 months ago.

Data Breach Today
SEPTEMBER 8, 2021
Experts Say Social Engineering Continues to Drive Illicit Activity The U.S. SEC in a new advisory warns against schemes targeting digital assets. Security experts say that with social engineering attempts on the rise, individuals and organizations must defend against related scams and other "get rich quick" schemes.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

WIRED Threat Level
SEPTEMBER 8, 2021
The fallout from the company's recent proposal has created a new opportunity to fix how it roots out abusive material across its devices.
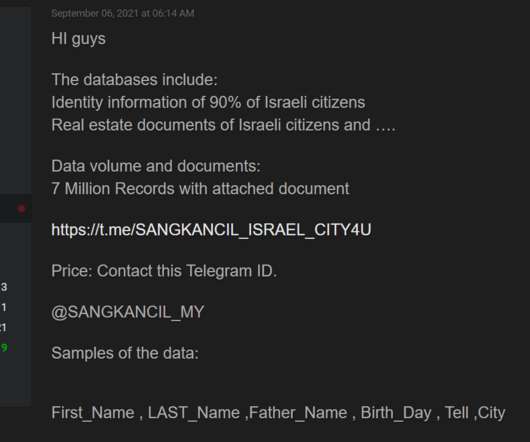
Security Affairs
SEPTEMBER 8, 2021
A threat actor that goes online with the moniker ‘Sangkancil’ claims to have stolen the personal information of 7 million Israelis. A threat actor that goes online with the moniker ‘Sangkancil’ claims to have stolen the personal information of 7 million Israelis from the CITY4U website. The hacker is offering the data for sale, but did not disclose the price for the complete archive.

eSecurity Planet
SEPTEMBER 7, 2021
Zero day threats can be the source of some of the most dangerous kinds of cyberattacks. Zero day attacks take advantage of vulnerabilities that haven’t been discovered or are not publicly known yet. One of the things that makes these threats so dangerous is that they often come without warning, posing a huge risk to the companies or individuals at stake.

Data Breach Today
SEPTEMBER 8, 2021
Classes Canceled as the University's IT Staff Repairs Damage Howard University canceled classes Tuesday in the wake of a ransomware attack it first detected on Friday, the university has announced. There is no evidence the attackers accessed or exfiltrated personal information, the school says.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Schneier on Security
SEPTEMBER 7, 2021
Normal-looking cables (USB-C, Lightning, and so on) that exfiltrate data over a wireless network. I blogged about a previous prototype here.

Security Affairs
SEPTEMBER 6, 2021
Security researcher ValdikSS found malware preinstalled in four low-budget push-button mobile phones available for sale on Russian e-stores. A Russian security researcher that goes online with the name of ValdikSS has found malware preinstalled in four low-budget push-button mobile phones available for sale on Russian e-stores. The expert noticed that several push-button telephones contain unwanted undocumented functions such as automatically sending SMS messages or going online to transmit purc

eSecurity Planet
SEPTEMBER 10, 2021
From the very beginning of the cloud computing era, security has been the biggest concern among enterprises considering the public cloud. For many organizations, the idea of storing data or running applications on infrastructure that they do not manage directly seems inherently insecure. CloudPassage’s 2021 AWS Cloud Security Report found that misconfiguration of cloud platforms (71 percent), exfiltration of sensitive data (59 percent), and insecure APIs (54 percent) are the top cloud secu
Let's personalize your content