Stay Safe Online in 10 Easy Steps
Elie
AUGUST 1, 2021
Here are the ten most important steps you can take to stay safe online. Blog post

Elie
AUGUST 1, 2021
Here are the ten most important steps you can take to stay safe online. Blog post
Security Affairs
AUGUST 2, 2021
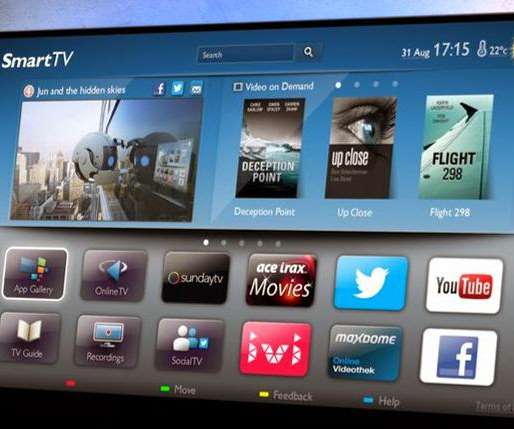
Did you ever stop to think that the office smart TV used for company presentations, Zoom meetings, and other work-related activities may not be so trustworthy? In our latest video, we demonstrate an attack scenario that can occur within any organization – hacking a smart TV. The video shows an insider plugging a USB Rubber Ducky into a smart TV in a company meeting room.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Threatpost
AUGUST 5, 2021
IBM X-Force detailed the custom-made "LittleLooter" data stealer and 4+ hours of ITG18 operator training videos revealed by an opsec goof.

Data Breach Today
AUGUST 5, 2021
Ivanti, Sophos, Deloitte, Cerberus Sentinel and Feedzai Announce Deals Cybersecurity acquisitions continue at an intense pace, with Ivanti, Sophos, Deloitte Risk & Financial Advisory, Cerberus Sentinel and Feedzai all making moves to bolster their security portfolios.

Speaker: Frank Taliano
Document-heavy workflows slow down productivity, bury institutional knowledge, and drain resources. But with the right AI implementation, these inefficiencies become opportunities for transformation. So how do you identify where to start and how to succeed? Learn how to develop a clear, practical roadmap for leveraging AI to streamline processes, automate knowledge work, and unlock real operational gains.

WIRED Threat Level
AUGUST 2, 2021
The tech may seem antiquated, but it poses very modern cybersecurity problems.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

The Last Watchdog
AUGUST 4, 2021
A cornucopia of cybersecurity solutions went on public display today as Black Hat USA 2021 convened once more as a live event in Las Vegas. Related: Kaseya hack raises more supply chain worries. For small- and mid-sized businesses (SMBs) cutting through the marketing hype can be daunting. That said, there is one venerable technology – web application firewalls ( WAFs) – that is emerging as a perfect fit for SMBs in today’s environment, as all companies shift to a deeper reliance on cloud service

Data Breach Today
AUGUST 4, 2021
vpnMentor: Server Belonging to OneMoreLead Is Now Secured Researchers at vpnMentor say that B2B marketing company OneMoreLead exposed the data of up to 126 million Americans on a misconfigured Elasticsearch server.

WIRED Threat Level
AUGUST 4, 2021
It’s not a ghost. It’s a half-dozen vulnerabilities in a digital automation system.

Security Affairs
AUGUST 4, 2021
The American venture capital firm Advanced Technology Ventures (ATV) disclosed a ransomware attack, crooks also stole data of some private investors. Advanced Technology Ventures (ATV) is an American venture capital firm with more than $1.8 billion in capital under management. The venture capital firm this week disclosed a ransomware attack, threat actors have also stolen the personal information of some of its private investors.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

The Last Watchdog
AUGUST 4, 2021
Human beings remain the prime target in the vast majority of malicious attempts to breach company networks. Related: Stealth tactics leveraged to weaponize email. Cybersecurity awareness training is valuable and has its place. Yet as Black Hat USA 2021 returns today as a live event in Las Vegas, it remains so true that we can always be fooled — and that the prime vehicle for hornswoggling us remains phishing messages sent via business email.
Data Breach Today
AUGUST 3, 2021
Malwarebytes Describes Unusual Tactics The Malwarebytes threat intelligence team has discovered a remote access Trojan apparently designed to target Russian speakers that may have combined a social engineering technique with a known exploit to maximize chances of infecting targets.

WIRED Threat Level
AUGUST 5, 2021
Vulnerabilities in Signal, Facebook Messenger, Google Duo, and more all point to a pervasive privacy issue.

Security Affairs
AUGUST 6, 2021
VMware has addressed a critical vulnerability that affects multiple products that could be exploited to gain access to confidential information. VMware has released security updates to address multiple flaws in its products, including a critical issue that could allow an attacker to access confidential information. A couple of vulnerabilities tracked as CVE-2021-22002 and CVE-2021-22003, impact Workspace One Access (Access), Identity Manager (vIDM), vRealize Automation (vRA), Cloud Foundation, a

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

The Last Watchdog
AUGUST 3, 2021
Software developers have become the masters of the digital universe. Related: GraphQL APIs pose new risks. Companies in the throes of digital transformation are in hot pursuit of agile software and this has elevated developers to the top of the food chain in computing. There is an argument to be made that agility-minded developers, in fact, are in a terrific position to champion the rearchitecting of Enterprise security that’s sure to play out over the next few years — much more so than me

Data Breach Today
AUGUST 6, 2021
OIG Outlines Shortcomings, Recommends Fixes The FDIC has failed to properly update its policies for mobile device usage, conduct regular control assessments of its mobile device management solution or adequately log and monitor mobile cybersecurity practices, according to a new report from the Office of the Inspector General.

WIRED Threat Level
JULY 31, 2021
Plus: A sneaky iOS app, a wiper attack in Iran, and more of the week's top security news.
Security Affairs
AUGUST 5, 2021
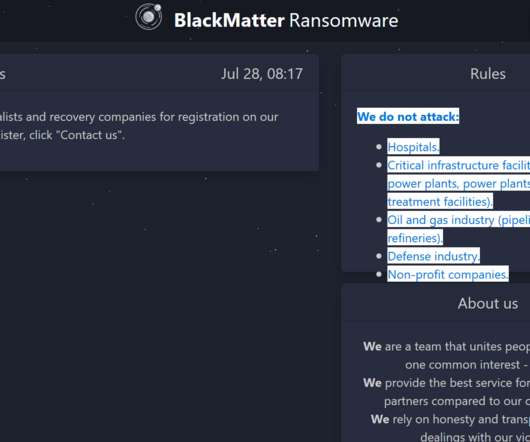
BlackMatter gang rapidly evolves, the group has developed a Linux version that allows operators to targets VMware’s ESXi VM platform. The BlackMatter ransomware gang has implemented a Linux encryptor to targets VMware ESXi virtual machine platform. This is the last ransomware in order of time that is able to target VM platforms, some of the other ransomware operations that do the same are REvil , RansomExx/Defray , Mespinoza , HelloKitty , and Babuk.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

The Last Watchdog
AUGUST 2, 2021
In less than a decade, SOAR — security orchestration, automation and response — has rapidly matured into an engrained component of the security technology stack in many enterprises. Related: Equipping SOCs for the long haul. SOAR has done much since it entered the cybersecurity lexicon to relieve the cybersecurity skills shortage. SOAR leverages automation and machine learning to correlate telemetry flooding in from multiple security systems.

Data Breach Today
AUGUST 6, 2021
One Measure Calls for Sanctions Against Nations Tolerating Ransomware Gangs Two bipartisan bills introduced in Congress this week seek to address cyberthreats. One calls for imposing sanctions against countries that allow ransomware gangs to operate within their borders. Another would require law enforcement agencies to better track cybercrime statistics to identify trends.

WIRED Threat Level
AUGUST 3, 2021
The crime-tracking app is charging $20 per month to give subscribers access to their own virtual security service.
Security Affairs
AUGUST 5, 2021
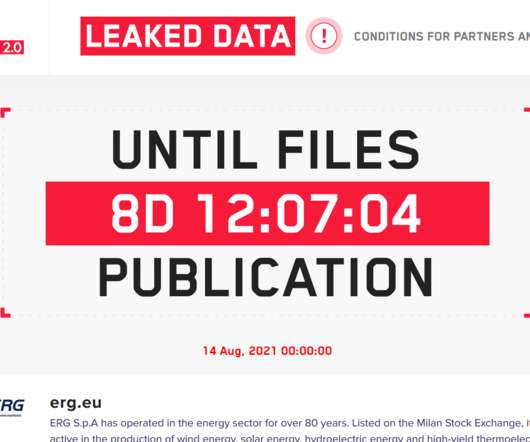
ERG SPA, an Italian energy company, reports a minor impact on its operations after the recent ransomware attack conducted by LockBit 2.0 gang. Recently the Italian energy company ERG was hit by the LockBit 2.0 ransomware gang, now the company reported “only a few minor disruptions” for its ICT infrastructure. The company is active in the production of wind energy, solar energy, hydroelectric energy and high-yield thermoelectric cogeneration energy with low environmental impact. ̶

Speaker: Yohan Lobo and Dennis Street
In the accounting world, staying ahead means embracing the tools that allow you to work smarter, not harder. Outdated processes and disconnected systems can hold your organization back, but the right technologies can help you streamline operations, boost productivity, and improve client delivery. Dive into the strategies and innovations transforming accounting practices.

Schneier on Security
AUGUST 6, 2021
Fascinating research: “ Generating Master Faces for Dictionary Attacks with a Network-Assisted Latent Space Evolution.” Abstract: A master face is a face image that passes face-based identity-authentication for a large portion of the population. These faces can be used to impersonate, with a high probability of success, any user, without having access to any user-information.

Data Breach Today
AUGUST 4, 2021
Incident Bears Similarities to Recent Attack at Scripps Health In the wake of a recent cyberattack on UF Health Central Florida that disrupted access to patients' electronic health records for about a month during recovery, the entity is now reporting the incident also exposed patient information.

WIRED Threat Level
AUGUST 1, 2021
Google is pushing the new standard for Android devices, which promises better security and cooler features than plain old SMS.
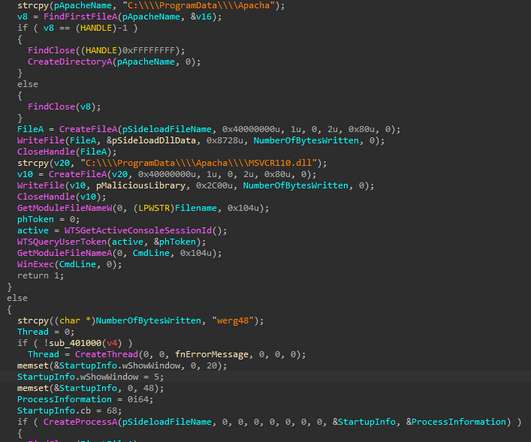
Security Affairs
AUGUST 4, 2021
China-linked APT31 group employed a new strain of malware in attacks aimed at entities in Mongolia, Belarus, Canada, the US, and Russia. Researchers from Positive Technologies reported that China-linked APT31 group has been using a new piece of malware in a recent wave of attacks targeting Mongolia, Belarus, Canada, the United States, and Russia. Experts found many similarities between the malware and the DropboxAES RAT that was first spotted by researchers at Secureworks and that was previously

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

Schneier on Security
AUGUST 5, 2021
The facts aren’t news, but Zoom will pay $85M — to the class-action attorneys, and to users — for lying to users about end-to-end encryption, and for giving user data to Facebook and Google without consent. The proposed settlement would generally give Zoom users $15 or $25 each and was filed Saturday at US District Court for the Northern District of California.

Data Breach Today
AUGUST 2, 2021
Agency Emphasizes Value of VPNs, Other Security Steps Teleworking U.S. national security employees are putting sensitive data at risk if they use public Wi-Fi networks without using a virtual private network to encrypt the traffic, the National Security Agency notes in a new advisory.

WIRED Threat Level
AUGUST 5, 2021
With a new capability to search for illegal material not just in the cloud but on user devices, the company may have opened up a new front in the encryption wars.
Let's personalize your content