15 Cybersecurity Pitfalls and Fixes for SMBs
Threatpost
APRIL 5, 2021
In this roundtable, security experts focus on smaller businesses offer real-world advice for actionable ways to shore up defenses using fewer resources.

Threatpost
APRIL 5, 2021
In this roundtable, security experts focus on smaller businesses offer real-world advice for actionable ways to shore up defenses using fewer resources.

DXC Technology
APRIL 8, 2021
Many companies are eager to use artificial intelligence (AI) in production, but struggle to achieve real value from the technology. What’s the key to success? Creating new services that learn from data and can scale across the enterprise involves three domains: software development, machine learning (ML) and, of course, data.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

AIIM
APRIL 6, 2021
In a truly all-digital world, there would be no need for printers – or scanners or document couriers. Documents would never need to be printed, and processes would run smoothly from all-electronic input to all-electronic output. This may already the reality for some leading companies, but for most organizations, forms, contracts, agreements, and signoffs are still rooted in wet ink on paper.
WIRED Threat Level
APRIL 6, 2021
The encrypted messaging app is integrating support for MobileCoin in a bid to keep up with the features offered by its more mainstream rivals.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.
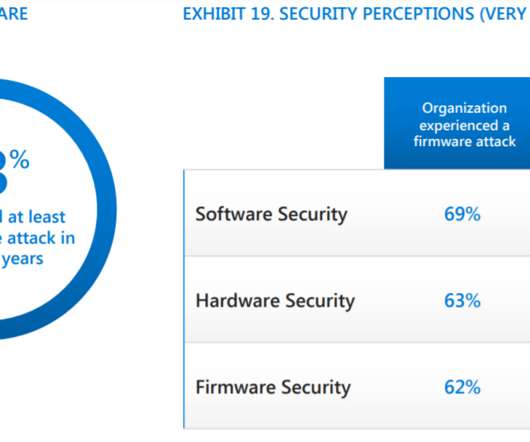
Security Affairs
APRIL 5, 2021
A new report published by Microsoft revealed that 80% of global enterprises were victims of a firmware-focused cyberattack. Microsoft recently published a report that states, titled “March 2021 Security Signals report,” that revealed that more than 80% of enterprises were victims of at least one firmware attack in the past two years. The study pointed out that only 29% of the targeted organizations have allocated budgets to protect firmware.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
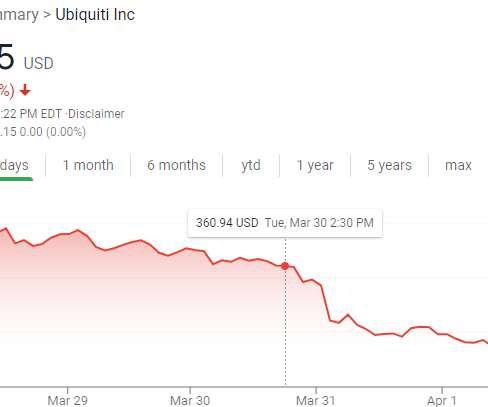
Krebs on Security
APRIL 4, 2021
For four days this past week, Internet-of-Things giant Ubiquiti did not respond to requests for comment on a whistleblower’s allegations the company had massively downplayed a “catastrophic” two-month breach ending in January to save its stock price, and that Ubiquiti’s insinuation that a third-party was to blame was a fabrication.

WIRED Threat Level
APRIL 9, 2021
The FBI arrested the suspect in Texas after he purchased explosives from an undercover agent.
Security Affairs
APRIL 8, 2021
Days after a massive Facebook data leak made the headlines, 500 million LinkedIn users are being sold online, seller leaked 2 million records as proof. Original Post at [link]. An archive containing data purportedly scraped from 500 million LinkedIn profiles has been put for sale on a popular hacker forum, with another 2 million records leaked as a proof-of-concept sample by the post author.

Data Breach Today
APRIL 6, 2021
Gemini Advisory Says Russian Cybercriminal Sold Gift Card, Payment Card Data A Russian-speaking cybercriminal recently sold on a darknet forum thousands of stolen payment and gift cards that researchers at Gemini Advisory believe were taken from the now defunct online gift card exchange Cardpool.com.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m
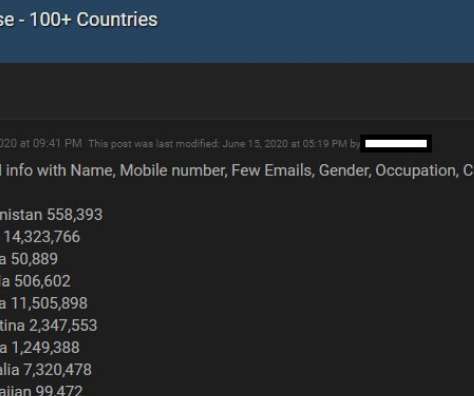
Krebs on Security
APRIL 6, 2021
Ne’er-do-wells leaked personal data — including phone numbers — for some 553 million Facebook users this week. Facebook says the data was collected before 2020 when it changed things to prevent such information from being scraped from profiles. To my mind, this just reinforces the need to remove mobile phone numbers from all of your online accounts wherever feasible.

WIRED Threat Level
APRIL 6, 2021
The company's explanations have been confusing and inconsistent, but there are finally some answers.

Security Affairs
APRIL 4, 2021
A malware attack against vehicle inspection services provider Applus Technologies paralyzed preventing vehicle inspections in eight US states. Applus Technologies is a worldwide leader in the testing, inspection and certification sector, the company was recently hit by a malware cyberattack that impacted vehicle inspections in eight states, including Connecticut, Georgia, Idaho, Illinois, Massachusetts, Utah, and Wisconsin.
Data Breach Today
APRIL 9, 2021
Cisco Talos: Reliance on These Tools Expands Attack Surface The increasing reliance on collaboration tools such as Slack and Discord to support those working remotely during the COVID-19 pandemic has opened up new ways for fraudsters and cybercriminals to bypass security tools and deliver malware, Cisco Talos reports.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.
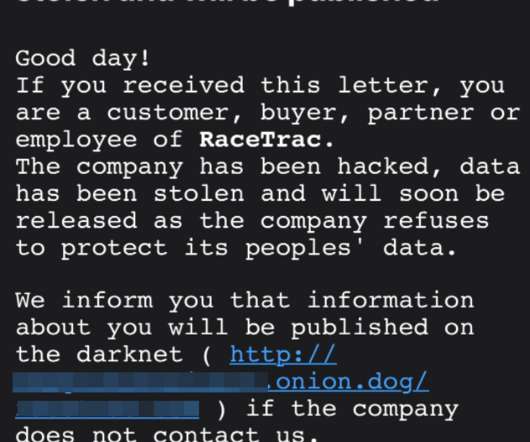
Krebs on Security
APRIL 5, 2021
Some of the top ransomware gangs are deploying a new pressure tactic to push more victim organizations into paying an extortion demand: Emailing the victim’s customers and partners directly, warning that their data will be leaked to the dark web unless they can convince the victim firm to pay up. This letter is from the Clop ransomware gang, putting pressure on a recent victim named on Clop’s dark web shaming site. “Good day!

AIIM
APRIL 8, 2021
Document Management is the use of a software application to track digital documents from creation through approval and publication. It serves in many ways to apply a formal governance framework to the document creation and collaborative editing processes. Today document management is generally incorporated as a set of capabilities in a broader enterprise content management (ECM) or information management solution.
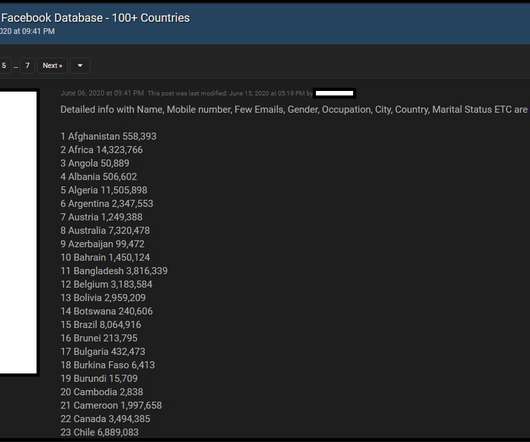
Security Affairs
APRIL 3, 2021
On April 3, a user has leaked the phone numbers and personal data of 533 million Facebook users in a hacking forum for free online. Bad news for Facebook, a user in a hacking forum has published the phone numbers and personal data of 533 million Facebook users. The availability of the data was first reported by Alon Gal, CTO of cyber intelligence firm Hudson Rock.

Data Breach Today
APRIL 7, 2021

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
APRIL 7, 2021
Beware of links from platforms that got big during quarantine.

The Last Watchdog
APRIL 5, 2021
We live in a time where technology is advancing rapidly, and digital acceleration is propelling development teams to create web applications at an increasingly faster rhythm. The DevOps workflow has been accompanying the market shift and becoming more efficient every day – but despite those efforts, there was still something being overlooked: application security.

Security Affairs
APRIL 3, 2021
The popular code repository hosting service GitHub is investigating a crypto-mining campaign abusing its infrastructure. Code repository hosting service GitHub launched an investigation in a series of attacks aimed at abusing its infrastructure to illicitly mine cryptocurrency. Such kind of attacks was reported at least since the end of 2020, when some software developers reported the malicious activity on their repositories. “I was attacked by a github user that crafted a malicious github

Data Breach Today
APRIL 9, 2021
ISMG Editors Discuss Hot Topics, Including Health Data Breaches Four editors at Information Security Media Group discuss important cybersecurity issues, including President Biden’s latest cybersecurity proposals and large vendor-related breaches in healthcare.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

WIRED Threat Level
APRIL 9, 2021
Software makers can’t catch every bug every time, but Facebook had ample warning about the privacy problems with its “contact import” feature.

The Last Watchdog
APRIL 7, 2021
Passwordless authentication as a default parameter can’t arrive too soon. Related: Top execs call for facial recognition to be regulated. The good news is that passwordless technologies are not only ready for prime time, they appear to be gaining traction in ways that suggest we’re on the cusp of a period of wide-scale adoption. That’s the upshot of a new report, The State of Passwordless Security 2021 , put out by HYPR , a New York City-based supplier of advanced authentication systems.

Security Affairs
APRIL 8, 2021
A threat actor has sold almost 900,000 gift cards and over 300,000 payment cards on a cybercrime forum on the dark web. A crook has sold 895,000 gift cards and over 300,000 payment cards, for a total of US$38 million, on a top-tier Russian-language hacking forum on the dark web. The criminal actor was spotted offering a huge amount of cards in February 2021.
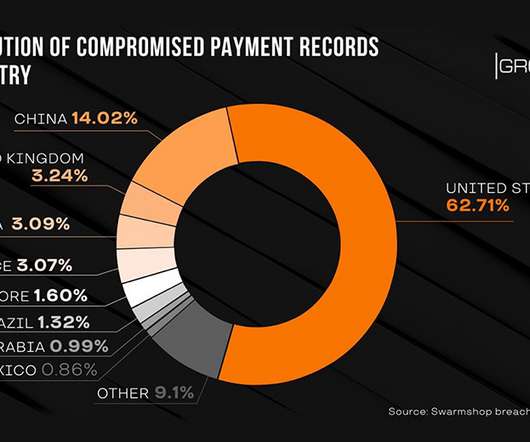
Data Breach Today
APRIL 8, 2021
Group-IB: Administrator, Seller and Buyer Data Also Stolen For the second time in two years, the contents of the darknet payment card marketplace Swarmshop have been removed and posted to a competing underground forum, Group-IB reports. The content includes data on more than 600,000 payment cards as well as administrator, seller and buyer information.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

WIRED Threat Level
APRIL 3, 2021
Plus: North Korean hackers, a rogue tweet, and more of the week's top security news.

Schneier on Security
APRIL 9, 2021
Unknown hackers attempted to add a backdoor to the PHP source code. It was two malicious commits , with the subject “fix typo” and the names of known PHP developers and maintainers. They were discovered and removed before being pushed out to any users. But since 79% of the Internet’s websites use PHP, it’s scary. Developers have moved PHP to GitHub, which has better authentication.

Security Affairs
APRIL 7, 2021
A new supply chain attack made the headlines, threat actors compromised at least one update server of smartphone maker Gigaset to deliver malware. The German device maker Gigaset was the victim of supply chain attack, threat actors compromised at least one server of the company to deliver malware. Gigaset AG , formerly known as Siemens Home and Office Communication Devices, is a multinational corporation based Germany.
Let's personalize your content