2020 Cyber Threats, Trends and Attacks
Data Breach Today
MAY 5, 2020
What You Don't See Now, Can Hurt You Later

Data Breach Today
MAY 5, 2020
What You Don't See Now, Can Hurt You Later

Data Breach Today
MAY 4, 2020
Trump Bans Use of Foreign Equipment That Poses 'National Security Threat' Declaring that threats to the United States' power grid are a national emergency, President Donald Trump is taking steps designed to help defend the grid from foreign interference by focusing on the supply chain.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
MAY 7, 2020
This is a good explanation of an iOS bug that allowed someone to break out of the application sandbox. A summary: What a crazy bug, and Siguza's explanation is very cogent. Basically, it comes down to this: XML is terrible. iOS uses XML for Plists , and Plists are used everywhere in iOS (and MacOS). iOS's sandboxing system depends upon three different XML parsers, which interpret slightly invalid XML input in slightly different ways.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Dark Reading
MAY 4, 2020
Researchers warn the installers are legitimate but don't come from official sources of the Zoom app, including the Apple App Store and Google Play.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
MAY 6, 2020
Researchers: Malware Is Capable of Launching DDoS Attacks Kaiji, a newly discovered botnet, is compromising Linux servers and IoT devices using brute-force methods that target the SSH protocol, according to the security firm Intezer. The botnet has the capability to launch DDoS attacks.

Data Breach Today
MAY 4, 2020
Nintendo Was Likely Anticipating the Dump After 2018 Intrusion Gamers are poring over a massive leak of Nintendo data, including source code for older gaming systems, prototypes of games and extensive software and hardware documentation. The data likely dates from a 2018 network intrusion at Nintendo.

Data Breach Today
MAY 8, 2020
The latest edition of the ISMG Security Report analyzes the many challenges involved in developing and implementing contact-tracing apps to help in the battle against COVID-19. Also featured: A discussion of emerging privacy issues and a report on why account takeover fraud losses are growing.

Threatpost
MAY 5, 2020
The vulnerability is one of 39 affecting various aspects of the mobile OS that the company fixed in a security update this week.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

WIRED Threat Level
MAY 4, 2020
As contact tracing plans firm up, the tech giants are sharing new details for their framework—and a potential app interface.

Dark Reading
MAY 6, 2020
Hackers are hitting the sports industry hard on social media and luring quarantined consumers with offers of free streaming services, a new report shows.

Security Affairs
MAY 5, 2020
A proof-of-concept (PoC) exploit for the recently fixed CVE-2020-1967 denial-of-service (DoS) issue in OpenSSL has been made public. Recently, the OpenSSL Project released a security update for OpenSSL that patches a high-severity vulnerability, tracked as CVE-2020-1967 , that can be exploited by attackers to launch denial-of-service (DoS) attacks. The CVE-2020-1967 vulnerability has been described as a “segmentation fault” in the SSL_check_chain function, it is the first issue addressed in Op

WIRED Threat Level
MAY 3, 2020
A recent infection, which managed to plunder a company's network within hours, demonstrates why the malware has become so prevalent.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Data Breach Today
MAY 5, 2020
Campaign Designed to Harvest Credentials of Financial Industry Regulatory Authority Members The Financial Industry Regulatory Authority, a private organization that helps self-regulate brokerage firms and exchange markets in the U.S., warns that a "widespread, ongoing" phishing campaign is targeting its members.

Krebs on Security
MAY 6, 2020
Fresenius , Europe’s largest private hospital operator and a major provider of dialysis products and services that are in such high demand thanks to the COVID-19 pandemic, has been hit in a ransomware cyber attack on its technology systems. The company said the incident has limited some of its operations, but that patient care continues. Based in Germany, the Fresenius Group includes four independent businesses: Fresenius Medical Care , a leading provider of care to those suffering from ki
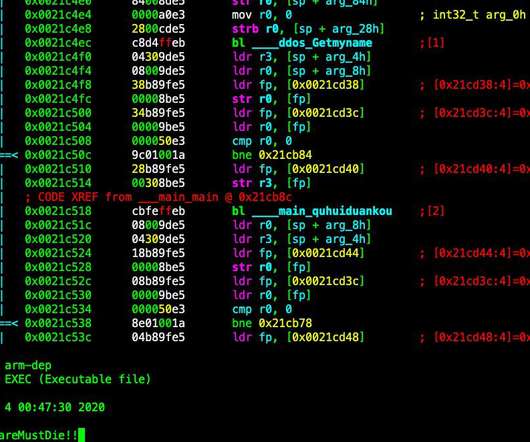
Security Affairs
MAY 5, 2020
Security researchers spotted a new piece of DDoS bot dubbed Kaiji that is targeting IoT devices via SSH brute-force attacks. Last week, the popular security researcher MalwareMustDie and the experts at Intezer Labs spotted a new piece of malware dubbed Kaiji, that is targeting IoT devices via SSH brute-force attacks. The malicious code was designed to target Linux-based servers and Internet of Things (IoT) devices and use them as part of a DDoS botnet.

WIRED Threat Level
MAY 6, 2020
The system's use of GPS data could let hackers pinpoint who reports a positive diagnosis.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Data Breach Today
MAY 7, 2020
'Unauthorized Individual' Accessed SSH File, Company Says Web hosting giant GoDaddy confirms that a data breach has affected about 28,000 of its customers' web hosting accounts, according to a news report. The company has reset passwords and usernames for some customers as a precaution, although it says no data appears to have been altered.
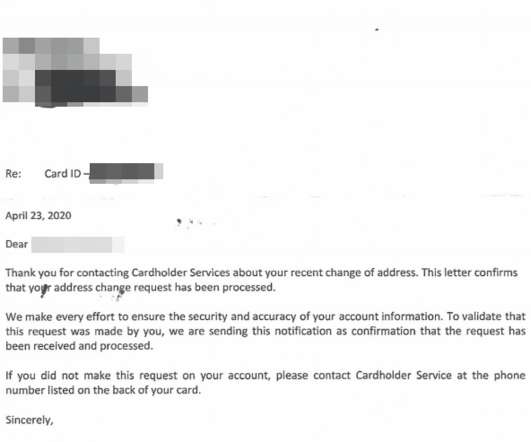
Krebs on Security
MAY 8, 2020
Millions of Americans now filing for unemployment will receive benefits via a prepaid card issued by U.S. Bank , a Minnesota-based financial institution that handles unemployment payments for more than a dozen U.S. states. Some of these unemployment applications will trigger an automatic letter from U.S. Bank to the applicant. The letters are intended to prevent identity theft, but many people are mistaking these vague missives for a notification that someone has hijacked their identity.

Security Affairs
MAY 5, 2020
GoDaddy has been notifying its customers of a data breach, threat actors might have compromised their web hosting account credentials. GoDaddy has been notifying its customers of a data breach, attackers might have compromised users’ web hosting account credentials. Headquartered in Scottsdale, Arizona, the Internet domain registrar and web hosting company claims to have over 19 million customers worldwide.

WIRED Threat Level
MAY 5, 2020
CAM4 has taken the server offline, but not before it leaked 7TB of user data.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

Data Breach Today
MAY 5, 2020
'Password-Spraying' Campaigns Aimed at Stealing Research Data, US and UK Authorities Warn Authorities in the U.S. and U.K. are warning medical institutions, pharmaceutical companies, universities and others about "password-spraying campaigns" by advance persistent threat groups seeking to steal COVID-19 research data. Security experts outline defensive steps that organizations can take.

AIIM
MAY 5, 2020
The large-scale and lasting impacts of a digital transformation will influence your company for decades to come. Going digital is not merely about adopting present practices - it is a step into the future, aligning your business model and company's methods with the format that is solidifying itself as the new standard. As with any new integration, digitalization presents its fair share of challenges.
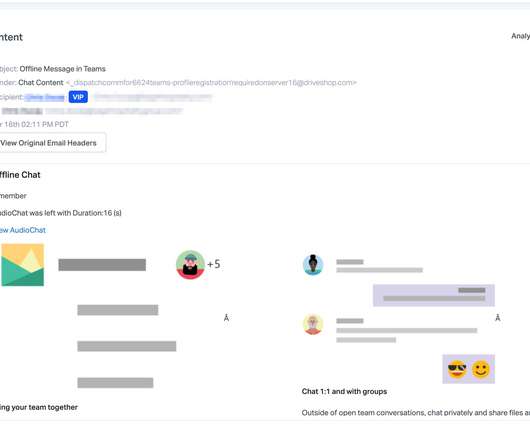
Security Affairs
MAY 2, 2020
Phishing attacks impersonating notifications from Microsoft Teams targeted as many as 50,000 Teams users to steal Office365 logins. Abnormal Security experts observed two separate phishing attacks impersonating notifications from Microsoft Teams that targeted as many as 50,000 Teams users to steal Office365 logins. The popularity of Microsoft Teams has spiked as a result of the smart working adopted by many organizations due to the COVID-19 pandemic.

WIRED Threat Level
MAY 8, 2020
For real this time. Its sister conference, Black Hat, has also been called off.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.
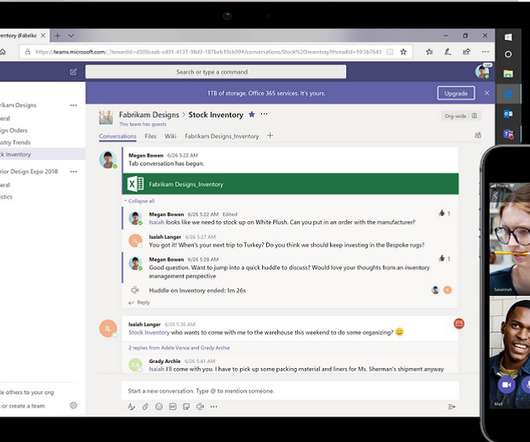
Data Breach Today
MAY 2, 2020
Fraudsters Look to Harvest Office 365 Credentials From At-Home Employees A recently uncovered phishing campaign is spoofing notifications from Microsoft's Teams collaboration platform in order to harvest Office 365 credentials from employees working from home offices because of the COVID-19 pandemic, according to research from Abnormal Security.

AIIM
MAY 6, 2020
The concept of a digital mailroom has been around a while. The idea is pretty simple - all incoming mail is scanned on entry and delivered electronically to the appropriate department or process. In reality, only mail with business value is likely to be processed. This will predominantly be documents with a structure such as forms, orders, invoices, delivery dockets, and vouchers.
Security Affairs
MAY 3, 2020
A hacker has leaked the details of 15 million users registered on Tokopedia , an Indonesian technology company specializing in e-commerce. Tokopedia is an Indonesian technology company specializing in e-commerce, it currently operates Indonesia’s largest online store. The company has over 4200 employees and accounts for over 90 million active users every month.
Let's personalize your content