The Time Is Now for IoT Security Standards
Dark Reading
AUGUST 11, 2022
Industry standards would provide predictable and understandable IoT security frameworks.

Dark Reading
AUGUST 11, 2022
Industry standards would provide predictable and understandable IoT security frameworks.
Krebs on Security
AUGUST 10, 2022
One way to tame your email inbox is to get in the habit of using unique email aliases when signing up for new accounts online. Adding a “+” character after the username portion of your email address — followed by a notation specific to the site you’re signing up at — lets you create an infinite number of unique email addresses tied to the same account.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
AUGUST 6, 2022
Vulnerability Allowed Threat Actors to Gain Access to Personal Information Twitter confirms that a zero-day vulnerability allowed threat actors to gain access to the personal information of 5.4 million user account profiles. The company was notified about this specific vulnerability in Twitter's systems through their bug bounty program in January.
Security Affairs
AUGUST 9, 2022
Cybersecurity researchers from Kaspersky linked the Maui ransomware to the North Korea-backed Andariel APT group. Kaspersky linked with medium confidence the Maui ransomware operation to the North Korea-backed APT group Andariel , which is considered a division of the Lazarus APT Group, . North Korean nation-state actors used Maui ransomware to encrypt servers providing healthcare services, including electronic health records services, diagnostics services, imaging services, and intranet servic

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

WIRED Threat Level
AUGUST 10, 2022
It cost a researcher only $25 worth of parts to create a tool that allows custom code to run on the satellite dishes.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Data Breach Today
AUGUST 10, 2022
Monthly Dump Includes Patches for 141 Flaws, Including 17 'Critical' Fixes More than two years after being notified of it, Microsoft issued a fix for a Microsoft Windows Support Diagnostic Tool vulnerability known as DogWalk. The fix is part of the operating system giant's newest Patch Tuesday dump, which includes patches for 141 flaws.

Security Affairs
AUGUST 7, 2022
A massive cyberattack hit the website of the German Chambers of Industry and Commerce (DIHK) this week. A massive attack hit the website of the German Chambers of Industry and Commerce (DIHK) forcing the organization to shut down its IT systems as a precautionary measure for security reasons. Aktuell wird intensiv an Lösung und Abwehr gearbeitet. Wir informieren Sie hier, welche Anwendungen wieder funktionsfähig sind: [link] #IHK #DIHK pic.twitter.com/5OHMOLH7Mz — DIHK (@DIHK_News) August

The Last Watchdog
AUGUST 10, 2022
Technology provides opportunities to positively impact the world and improve lives. Related: Why facial recognition ought to be regulated. It also delivers new ways to commit crimes and fraud. The U.S. Federal Bureau of Investigation (FBI) issued a public warning in June 2022 about a new kind of fraud involving remote work and deepfakes. The making of Deepfakes.

Krebs on Security
AUGUST 11, 2022
Image: Shutterstock. A cybersecurity firm says it has intercepted a large, unique stolen data set containing the names, addresses, email addresses, phone numbers, Social Security Numbers and dates of birth on nearly 23 million Americans. The firm’s analysis of the data suggests it corresponds to current and former customers of AT&T. The telecommunications giant stopped short of saying the data wasn’t theirs, but it maintains the records do not appear to have come from its systems

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

Data Breach Today
AUGUST 9, 2022
Victims Often Attacked Simultaneously by Multiple Ransomware Groups Cybercriminals monitor leak sites for newly listed ransomware victims in a bid to try their own hand at dropping encryption malware, says Sophos. The cybersecurity firm says it's seen an uptick in incidents involving multiple criminal gangs demanding a ransom for unencrypted victims' files.

Security Affairs
AUGUST 7, 2022
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive for free the newsletter with the international press subscribe here. Greek intelligence service used surveillance malware to spy on a journalist, Reuters reports Slack resets passwords for about 0.5% of its users due to the exposure of salted password hashes Twitter confirms zero-day used to access data of 5.4 millio

WIRED Threat Level
AUGUST 8, 2022
The new Pretty Good Phone Privacy service for Android hides the data linking you to your mobile device.

Krebs on Security
AUGUST 12, 2022
The Department of Homeland Security (DHS) is urging states and localities to beef up security around proprietary devices that connect to the Emergency Alert System — a national public warning system used to deliver important emergency information, such as severe weather and AMBER alerts. The DHS warning came in advance of a workshop to be held this weekend at the DEFCON security conference in Las Vegas, where a security researcher is slated to demonstrate multiple weaknesses in the nationw

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Data Breach Today
AUGUST 10, 2022
An ISMG Overview of the Technology Buzz Leading Up to Black Hat Conference 2022 ISMG caught up with 11 security executives in Las Vegas on Tuesday to discuss everything from open-source intelligence and Web3 security to training new security analysts and responding to directory attacks. Here's a look at some of the most interesting things we heard from industry leaders.
Security Affairs
AUGUST 10, 2022
A former Twitter employee was found guilty of spying on certain Twitter users for Saudi Arabia. A former Twitter employee, Ahmad Abouammo (44), was found guilty of gathering private information of certain Twitter users and passing them to Saudi Arabia. “Ahmad Abouammo, a US resident born in Egypt, was found guilty by a jury Tuesday of charges including acting as an agent for Saudi Arabia, money laundering, conspiracy to commit wire fraud and falsifying records, following a two-week trial i

WIRED Threat Level
AUGUST 12, 2022
An injection flaw allowed a researcher to access all files on a Mac. Apple issued a fix, but some machines may still be vulnerable.

The Last Watchdog
AUGUST 8, 2022
Our technological world is advancing at dizzying speeds. Related: The coming of a ‘bio digital twin” Over the last decade, we have seen the introduction of 4G and 5G telecommunication service, the iPad, Instagram, and the introduction, acceptance, and adoption of cloud services from Microsoft, Google, and Amazon, as well as cloud computing.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Data Breach Today
AUGUST 8, 2022
Penalties for Anyone in US Jurisdiction Who Uses the Cryptocurrency Mixer The federal government today sanctioned Tornado Cash. The Department of Treasury ordered assets of the Ethereum blockchain cryptocurrency mixer to be frozen and says civil and potentially criminal penalties await anyone under U.S. jurisdiction who uses the service.
Security Affairs
AUGUST 10, 2022
Cisco discloses a security breach, the Yanluowang ransomware group breached its corporate network in late May and stole internal data. Cisco disclosed a security breach, the Yanluowang ransomware group breached its corporate network in late May and stole internal data. The investigation conducted by Cisco Security Incident Response (CSIRT) and Cisco Talos revealed that threat actors compromised a Cisco employee’s credentials after they gained control of a personal Google account where credential

WIRED Threat Level
AUGUST 11, 2022
The Raspberry Pi-powered device can scan for phones around you. If it keeps spotting the same one, it’ll send you an alert.

eSecurity Planet
AUGUST 9, 2022
Regulatory compliance and data privacy issues have long been an IT security nightmare. And since the EU’s General Data Protection Regulation (GDPR) took effect May 25, 2018, IT compliance issues have been at the forefront of corporate concerns. GDPR, the EU’s flagship data privacy and “right to be forgotten” regulation, has made the stakes of a data breach higher than ever.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!
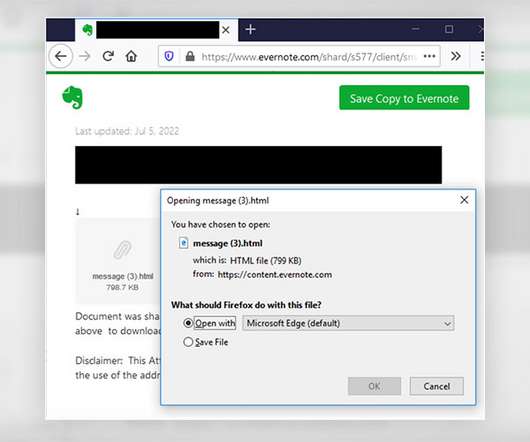
Data Breach Today
AUGUST 12, 2022
Scam Uses 'Secure Message' Theme and Trojan to Harvest Credentials A "secure message-themed" phishing campaign targeting healthcare providers aims to lure recipients to an Evernote notepad website in an attempt by hackers to harvest security credentials, federal authorities warn, saying the scheme puts entities at risk for potential data security compromises.

Security Affairs
AUGUST 9, 2022
Microsoft Patch Tuesday security updates for August 2022 addressed a zero-day attack remote code execution vulnerability in Windows. Microsoft Patch Tuesday security updates for August 2022 addressed 118 CVEs in multiple products, including.NET Core, Active Directory Domain Services, Azure Batch Node Agent, Azure Real Time Operating System, Azure Site Recovery, Azure Sphere, Microsoft ATA Port Driver, Microsoft Bluetooth Driver, Microsoft Edge (Chromium-based), Microsoft Exchange Server, Microso

WIRED Threat Level
AUGUST 10, 2022
Ten years after it was first unveiled, the powerful firmware analysis platform Ofrak is now available to anyone.

Schneier on Security
AUGUST 8, 2022
Quantum computing is a completely new paradigm for computers. A quantum computer uses quantum properties such as superposition, which allows a qubit (a quantum bit) to be neither 0 nor 1, but something much more complicated. In theory, such a computer can solve problems too complex for conventional computers. Current quantum computers are still toy prototypes, and the engineering advances required to build a functionally useful quantum computer are somewhere between a few years away and impossib

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Data Breach Today
AUGUST 8, 2022
Watters Can't Wait to Combine Google Analytics With Mandiant Intelligence Engine Combining the data analytics of Google Chronicle with Mandiant's ability to identify signals of abnormal behavior is an unbeatable combination, says Mandiant President and COO John Watters. Google agreed in March to purchase threat intelligence and incident response titan Mandiant for $5.4 billion.

Security Affairs
AUGUST 10, 2022
Cisco addressed a high severity flaw, tracked as CVE-2022-20866, affecting Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) software. Cisco addressed a high severity vulnerability in its Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) software. The flaw, tracked as CVE-2022-20866 , impacts the handling of RSA keys on devices running Cisco ASA Software and FTD Software, an unauthenticated, remote attacker can trigger it to retrieve an RSA private key.

WIRED Threat Level
AUGUST 9, 2022
New research found troubling vulnerabilities in the 5G platforms carriers offer to wrangle embedded device data.
Let's personalize your content