How China Hacked US Phone Networks
WIRED Threat Level
JUNE 11, 2022
Plus: Russia rattles its cyber sword, a huge Facebook phishing operation is uncovered, feds take down the SSNDOB marketplace, and more.

WIRED Threat Level
JUNE 11, 2022
Plus: Russia rattles its cyber sword, a huge Facebook phishing operation is uncovered, feds take down the SSNDOB marketplace, and more.

The Last Watchdog
JUNE 13, 2022
At the start of this year, analysts identified a number of trends driving the growth of cybersecurity. Among them: an expanding digital footprint, growing attack surfaces, and increasing government regulation. Related: Taking API proliferation seriously. Last year saw an unprecedented $21.8 billion in venture capital poured into cybersecurity companies globally.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
JUNE 13, 2022
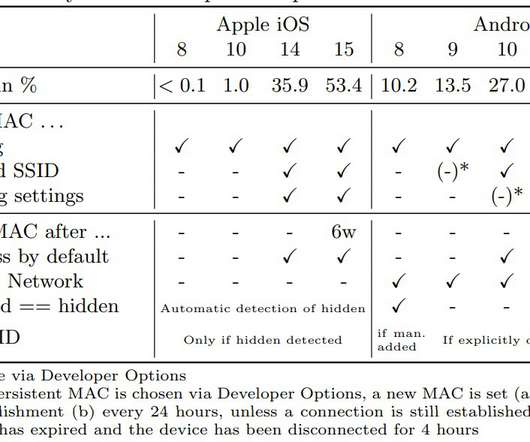
Researchers at the University of Hamburg demonstrated that WiFi connection probe requests expose users to track. A group of academics at the University of Hamburg (Germany) demonstrated that it is possible to use WiFi connection probe requests to identify and track devices and thereby their users. Mobile devices transmit probe requests to receive information about nearby Wi-Fi networks and establish a Wi-Fi connection.

Data Breach Today
JUNE 17, 2022
DXC Technology's Michael Baker on Top Threats, Recruitment Tips, Career Advice Threat watch: The ongoing Russia-Ukraine war continues to pose both direct and indirect risks to enterprise networks, says Michael Baker, vice president and IT CISO of IT services and consulting firm DXC Technology. He also discusses recruiting and retaining new talent.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

WIRED Threat Level
JUNE 16, 2022
New details connect police in India to a plot to plant evidence on victims' computers that led to their arrest.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Security Affairs
JUNE 12, 2022
Ransomware gangs are actively exploiting CVE-2022-26134 remote code execution (RCE) flaw in Atlassian Confluence Server and Data Center. Multiple ransomware groups are actively exploiting the recently disclosed remote code execution (RCE) vulnerability, tracked as CVE-2022-26134 , affecting Atlassian Confluence Server and Data Center. Proof-of-concept exploits for the CVE-2022-26134 vulnerability have been released online, Bleeping Computer reported that starting from Friday afternoon, a proo

Data Breach Today
JUNE 16, 2022
The latest edition of the ISMG Security Report includes highlights and observations from RSA Conference 2022, including a key message from RSA CEO Rohit Ghai. It also discusses the value of automation and the Cybersecurity and Infrastructure Security Agency's mission to grow cyber talent.

WIRED Threat Level
JUNE 17, 2022
Contactless fingerprinting uses a smartphone camera to capture your prints—and opens up a whole new set of privacy concerns.

Krebs on Security
JUNE 15, 2022
Microsoft on Tuesday released software updates to fix 60 security vulnerabilities in its Windows operating systems and other software, including a zero-day flaw in all supported Microsoft Office versions on all flavors of Windows that’s seen active exploitation for at least two months now. On a lighter note, Microsoft is officially retiring its Internet Explorer (IE) web browser, which turns 27 years old this year.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m
Security Affairs
JUNE 11, 2022
Iran-linked Lyceum APT group uses a new.NET-based DNS backdoor to target organizations in the energy and telecommunication sectors. The Iran-linked Lyceum APT group, aka Hexane or Spilrin, used a new.NET-based DNS backdoor in a campaign aimed at companies in the energy and telecommunication sectors, ZScaler researchers warn. The activity of the Lyceum APT group was first documented earlier in August 2019 by researchers at ICS security firm Dragos which tracked it as Hexane.

Data Breach Today
JUNE 17, 2022
The State of Passwordless in 2022, New Identity Technologies In the latest weekly update, Jeremy Grant, coordinator of the Better Identity Coalition, joins three editors at ISMG to discuss important cybersecurity issues, including where we are with passwordless, if we are getting closer to a U.S. federal privacy law, and next-gen authentication technologies.

The Last Watchdog
JUNE 16, 2022
The identity management market has grown to $13 billion and counting. While intuition would tell you enterprises have identity under control, that is far from reality. Related: Taking a zero-trust approach to access management. Current events, such as the global pandemic and ‘ The Great Resignation, ’ which have accelerated cloud adoption, remote working environments, and the number of business applications and systems in use has complicated matters.

WIRED Threat Level
JUNE 15, 2022
In occupied Ukraine, people’s internet is being routed to Russia—and subjected to its powerful censorship and surveillance machine.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.
Security Affairs
JUNE 17, 2022
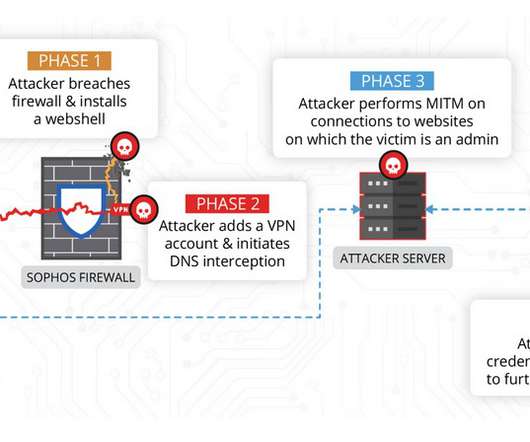
China-linked threat actors exploited the zero-day flaw CVE-2022-1040 in Sophos Firewall weeks before it was fixed by the security vendor. Volexity researchers discovered that the zero-day vulnerability, tracked as CVE-2022-1040 , in Sophos Firewall was exploited by Chinese threat actors to compromise a company and cloud-hosted web servers it was operating.

Data Breach Today
JUNE 15, 2022
CISO of Maricopa County, Arizona on Strengthening Election Security "Social media is probably the newest and most impactful thing that we've seen from a cybersecurity perspective at Maricopa County," says its CISO, Lester Godsey. The only response to misinformation and disinformation campaigns, he says, is to use the same platform and respond with the facts.

Krebs on Security
JUNE 14, 2022
A 33-year-old Illinois man was sentenced to two years in prison today following his conviction last year for operating services that allowed paying customers to launch powerful distributed denial-of-service (DDoS) attacks against hundreds of thousands of Internet users and websites. The user interface for Downthem[.]org. Matthew Gatrel of St. Charles, Ill. was found guilty for violations of the Computer Fraud and Abuse Act (CFAA) related to his operation of downthem[.]org and ampnode[.]com , two

WIRED Threat Level
JUNE 12, 2022
A pair of ransomware attacks crippled parts of the country—and rewrote the rules of cybercrime.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Security Affairs
JUNE 12, 2022
A new round of the weekly Security Affairs newsletter arrived! Every week the best security articles from Security Affairs for free in your email box. If you want to also receive for free the newsletter with the international press subscribe here. Ransomware gangs are exploiting CVE-2022-26134 RCE in Atlassian Confluence servers HID Mercury Access Controller flaws could allow to unlock Doors Iran-linked Lyceum APT adds a new.NET DNS Backdoor to its arsenal PACMAN, a new attack technique against

Data Breach Today
JUNE 17, 2022
KnowBe4's Roger Grimes on Why MFA Alone Isn't a Successful Hack Prevention Strategy Phishing is no longer restricted to just emails. As attackers broaden their arsenal, businesses today also need to be on the lookout for impersonation attempts via SMS text messages or voice calls, says Roger Grimes, a data-driven defense evangelist at KnowBe4.

eSecurity Planet
JUNE 16, 2022
A cyberattack is any action taken by a cyber criminal in an attempt to illegally gain control of a computer, device, network, or system with malicious intent. Cyber criminals may damage, destroy, steal, encrypt, expose, or leak data as well as cause harm to a system. Cyberattacks are on the rise, with cyber criminal trends and techniques becoming increasingly sophisticated and creative.

WIRED Threat Level
JUNE 17, 2022
Despite major progress fighting spam and scams, the roots of the problem go far deeper than your phone company’s defenses.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!
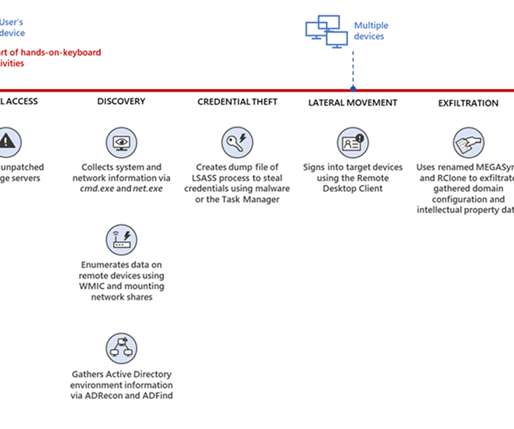
Security Affairs
JUNE 16, 2022
The BlackCat ransomware gang is targeting unpatched Exchange servers to compromise target networks, Microsoft warns. Microsoft researchers have observed BlackCat ransomware gang targeting unpatched Exchange servers to compromise organizations worldwide. The compromise of Exchange servers allows threat actors to access the target networks, perform internal reconnaissance and lateral movement activities, and steal sensitive documents before encrypting them. “For example, while the common ent

Data Breach Today
JUNE 15, 2022
Incident Is Latest on Growing List of Recent Major Healthcare Data Hacks An Arizona medical center that suffered a ransomware attack in April has begun notifying 700,000 individuals of a data breach compromising sensitive medical and personal information. The incident is among the latest major health data breaches involving ransomware.
IT Governance
JUNE 15, 2022
In an increasingly digital world, there are an escalating number of cyber security risks for business to address. Criminal hackers are adept at spotting weaknesses, while organisations do themselves no favours when they fail to adequately protect their systems. IT Governance identified more than 1,200 publicly disclosed data breaches in 2021 , while another report found that security incidents cost almost £3 million on average.

WIRED Threat Level
JUNE 13, 2022
Many people reportedly died after struggling to access medical care during a brutal lockdown. The families want to make sure these deaths are counted.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.
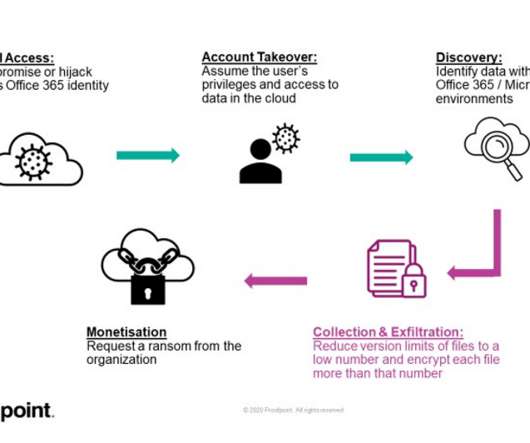
Security Affairs
JUNE 17, 2022
Experts discovered a feature in Microsoft 365 suite that could be abused to encrypt files stored on SharePoint and OneDrive and target cloud infrastructure. Researchers from Proofpoint reported that a feature in the in Microsoft 365 suite could be abused to encrypt files stored on SharePoint and OneDrive. “Proofpoint has discovered a potentially dangerous piece of functionality in Office 365 or Microsoft 365 that allows ransomware to encrypt files stored on SharePoint and OneDrive in a way

Data Breach Today
JUNE 17, 2022
Backdoored Apps Allow Normal Functioning of Wallet While Exfiltrating Master Key A "technically sophisticated" threat campaign is cloning cryptocurrency apps to steal funds from web3 wallet users, security researchers at Confiant say. The campaign, dubbed SeaFlower, uses cloned wallet apps offered by MetaMask, Coinbase, imToken and TokenPocket to carry out the theft.

Dark Reading
JUNE 17, 2022
Most of the attacks involve the use of automated exploits, security vendor says.
Let's personalize your content