3 Ways to Deal With the Trojan Source Attack
Dark Reading
NOVEMBER 8, 2021
These scripts and commands provide short-term fixes for blocking the Trojan Source attack that abuses Unicode to inject malicious backdoors in source code.
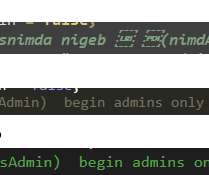
Dark Reading
NOVEMBER 8, 2021
These scripts and commands provide short-term fixes for blocking the Trojan Source attack that abuses Unicode to inject malicious backdoors in source code.

The Last Watchdog
NOVEMBER 8, 2021
There’s no doubt, the increasing use of telemedicine, the explosion of health-based cloud apps, and innovative medical IoT devices are improving the patient care experience. Related: Hackers relentlessly target healthcare providers. However, healthcare data ranks at the top of the list for needing improvements in security and privacy protections. This data is managed by different entities, such as primary care facilities, acute care facilities and within associated applications that collect, sto
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dark Reading
NOVEMBER 9, 2021
One of the biggest mistakes an organization can make is blindly throwing technology at the problem instead of properly investing in building a security team.
Security Affairs
NOVEMBER 10, 2021
South Korean users have been targeted with a new sophisticated Android spyware, tracked as PhoneSpy, as part of an ongoing campaign. Researchers from Zimperium zLabs uncovered an ongoing campaign aimed at infecting the mobile phones of South Korean users with new sophisticated android spyware dubbed PhoneSpy. The malware already hit more than a thousand South Korean victims.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.
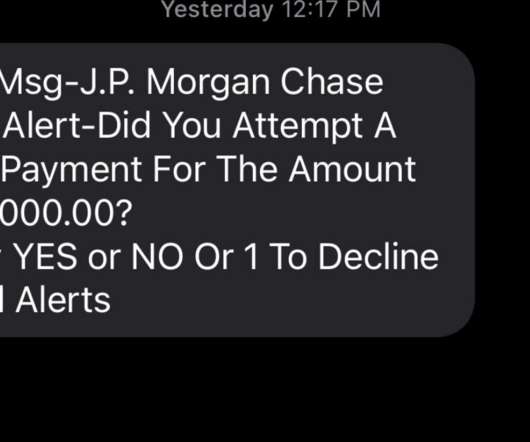
Krebs on Security
NOVEMBER 10, 2021
Most of us have probably heard the term “smishing” — which is a portmanteau for traditional ph ishing scams sent through SMS text messages. Smishing messages usually include a link to a site that spoofs a popular bank and tries to siphon personal information. But increasingly, phishers are turning to a hybrid form of smishing — blasting out linkless text messages about suspicious bank transfers as a pretext for immediately calling and scamming anyone who responds via text
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Preservica
NOVEMBER 9, 2021
Welcome to the "How we do it" Video Series. If you are a Clerk, Records Manager or Archivist for City or County Government, our practical “How we do it” videos are for you! We have compiled a series of videos, from users in City and County Government to share how they quickly and easily perform common electronic records preservation and access tasks with Preservica’ s solutions.

Security Affairs
NOVEMBER 12, 2021
Google revealed that threat actors recently exploited a zero-day vulnerability in macOS to deliver malware to users in Hong Kong. Google TAG researchers discovered that threat actors leveraged a zero-day vulnerability in macOS in a watering hole campaign aimed at delivering malware to users in Hong Kong. The attackers exploited a XNU privilege escalation vulnerability ( CVE-2021-30869 ) unpatched in macOS Catalina.

Krebs on Security
NOVEMBER 8, 2021
The U.S. Department of Justice today announced the arrest of Ukrainian man accused of deploying ransomware on behalf of the REvil ransomware gang, a Russian-speaking cybercriminal collective that has extorted hundreds of millions from victim organizations. The DOJ also said it had seized $6.1 million in cryptocurrency sent to another REvil affiliate, and that the U.S.

WIRED Threat Level
NOVEMBER 8, 2021
By arresting one alleged hacker associated with REVil and seizing millions from another, the US has made it clear that ransomware comes with a cost.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

eSecurity Planet
NOVEMBER 12, 2021
Remote work and home offices were an afterthought until the COVID-19 pandemic. They were then vaulted to the forefront of security concerns so quickly that security and IT teams were caught off guard. Now, remote work is likely here to stay even after the pandemic is gone. That means that the temporary solutions put in place over the last 18 months will need to give way to more permanent solutions.

Security Affairs
NOVEMBER 8, 2021
The US DoJ has charged a REvil ransomware affiliate that is suspected to have orchestrated the attack on Kaseya MSP platform in July. The US Department of Justice has charged a REvil ransomware affiliate for orchestrating the ransomware attacks on Kaseya MSP platform that took place in July 4. The suspect is 22-year old Ukrainian national Yaroslav Vasinskyi (aka Profcomserv, Rabotnik, Rabotnik_New, Yarik45, Yaraslav2468, and Affiliate 22), who was arrested for cybercriminal activity on October 8

Krebs on Security
NOVEMBER 9, 2021
Microsoft Corp. today released updates to quash at least 55 security bugs in its Windows operating systems and other software. Two of the patches address vulnerabilities that are already being used in active attacks online, and four of the flaws were disclosed publicly before today — potentially giving adversaries a head start in figuring out how to exploit them.

WIRED Threat Level
NOVEMBER 7, 2021
Plus: A ‘Trojan Source’ bug, Russian hackers exposed, and more of the week's top security news.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Troy Hunt
NOVEMBER 8, 2021
When someone passed me hundreds of thousands of records on kids taken from CloudPets a few years ago , I had a nightmare of a time getting in touch with the company. They'd left a MongoDB instance exposed to the public without a password and someone had snagged all their data. Within the data were references that granted access to voice recordings made by children, stored in an S3 bucket that also had no auth.

Security Affairs
NOVEMBER 9, 2021
The Clop ransomware gang is exploiting CVE-2021-35211 vulnerability in SolarWinds Serv-U to compromise corporate networks. Threat actors always look for new ways to compromise target networks, Clop ransomware gang (aka TA505, FIN11) is exploiting CVE-2021-35211 SolarWinds Serv-U vulnerability to breach businesses’ infrastructures and deploy its ransomware.

Schneier on Security
NOVEMBER 11, 2021
ArsTechnica’s Sean Gallagher has a two – part article on “securing your digital life.” It’s pretty good.

WIRED Threat Level
NOVEMBER 12, 2021
The social network got huge by ignoring who you know. That's increasingly no longer the case.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Threatpost
NOVEMBER 10, 2021
The distributed computing vendor patched the flaw, affecting Citrix ADC and Gateway, along with another flaw impacting availability for SD-WAN appliances.

Security Affairs
NOVEMBER 12, 2021
Wiz Research Team disclosed technical details about the discovery of the ChaosDB vulnerability in Azure Cosmos DB database solution. In August, 2021 the Wiz Research Team disclosed ChaosDB – a severe vulnerability in the popular Azure Cosmos DB database solution that allowed for complete, unrestricted access to the accounts and databases of several thousand Microsoft Azure customers, including many Fortune 500 companies.

Schneier on Security
NOVEMBER 10, 2021
I just don’t think it’s possible to create a hack-proof computer system, especially when the system is physically in the hands of the hackers. The Sony Playstation 5 is the latest example: Hackers may have just made some big strides towards possibly jailbreaking the PlayStation 5 over the weekend, with the hacking group Fail0verflow claiming to have managed to obtain PS5 root keys allowing them to decrypt the console’s firmware. […].

Dark Reading
NOVEMBER 10, 2021
AWS fixed the security flaws that left the API service at risk of so-called HTTP header-smuggling attacks, says the researcher who discovered them.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

Threatpost
NOVEMBER 11, 2021
Cyberattackers stole PS5 root keys and exploited the kernel, revealing rampant insecurity in gaming devices.

Security Affairs
NOVEMBER 6, 2021
The FBI issued a private industry notification (PIN) to warn of ransomware attacks that hit several tribal-owned casinos last year. A private industry notification issued by the FBI’s Cyber Division revealed that ransomware attacks hit several tribal-owned casinos causing millions of dollar losses. The attacks paralyzed the activities of the casinos shutting down their gaming floors, as well as restaurants, hotels, and gas stations.

Schneier on Security
NOVEMBER 12, 2021
Google researchers discovered a MacOS zero-day exploit being used against Hong Kong activists. It was a “watering hole” attack, which means the malware was hidden in a legitimate website. Users visiting that website would get infected. From an article : Google’s researchers were able to trigger the exploits and study them by visiting the websites compromised by the hackers.
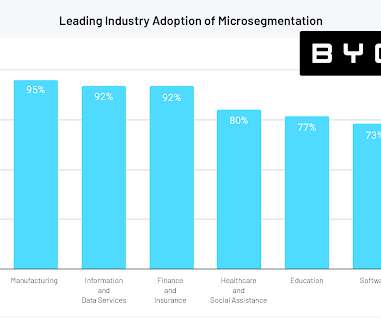
eSecurity Planet
NOVEMBER 10, 2021
For a security technology that’s only a few years old, microsegmentation is catching on quickly. According to a new report from edge security vendor Byos, 88 percent of cybersecurity leaders believe microsegmentation is essential to achieving zero trust security, and 83 percent are currently leveraging microsegmentation in some form. Despite such strong uptake, the market still has plenty of room to grow, the report found: only 17 percent have fully invested in microsegmentation to the poi

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Threatpost
NOVEMBER 12, 2021
BotenaGo, written in Google’s Golang programming language, can exploit more than 30 different vulnerabilities.

Security Affairs
NOVEMBER 8, 2021
Operation Cyclone – Six alleged affiliates with the Clop ransomware operation were arrested in an international joint law enforcement operation led by Interpol. Interpol announced the arrest of six alleged affiliates with the Clop ransomware operation as part of an international joint law enforcement operation codenamed Operation Cyclone. Law enforcement authorities from South Korea, Ukraine, and the United States, joint their efforts in a 30-month investigation that was coordinated by Int

Schneier on Security
NOVEMBER 8, 2021
We’ve now had an (unsuccessful) assassination attempt by explosive-laden drones.
Let's personalize your content