10 Mistakes Companies Make in Their Ransomware Responses
Dark Reading
JULY 14, 2021
Hit by ransomware? These missteps can take a bad scenario and make it even worse

Dark Reading
JULY 14, 2021
Hit by ransomware? These missteps can take a bad scenario and make it even worse

Dark Reading
JULY 12, 2021
Microsoft Active Directory, ubiquitous across enterprises, has long been a primary target for attackers seeking network access and sensitive data.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

OpenText Information Management
JULY 12, 2021
According to EFT, 55 percent of supply chain executives considered web service APIs as an alternative to EDI. But we should know better by now than try to write off electronic data interchange (EDI) again. This isn’t about replacement. It is, as always, about integration.

Data Breach Today
JULY 16, 2021
Palo Alto Networks Report Describes Tactics of Group Leveraging Open-Source Tools The gang behind the ransomware strain known as Mespinoza, aka PYSA, is targeting manufacturers, schools and others, mainly in the U.S. and U.K., demanding ransom payments as high as $1.6 million, according to Palo Alto Networks' Unit 42, which says the group leverages open-source tools.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Security Affairs
JULY 15, 2021
HelloKitty ransomware gang is using a Linux variant of their malware to target VMware ESXi virtual machine platform. A Linux variant of the HelloKitty ransomware was employed in attacks against VMware ESXi systems. The move of the ransomware gang aims at expanding the operations targeting enterprises that are largely adopting virtualizing platforms.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

WIRED Threat Level
JULY 15, 2021
The hackers posed as recruiters, journalists, and hospitality workers to lure its victims.

Data Breach Today
JULY 15, 2021
'Tortoiseshell' Group Used the Social Network to Contact Targets Facebook's threat intelligence team says it has disrupted an Iranian advanced persistent threat group that was using the social network as part of an effort to spread malware and conduct cyberespionage operations, primarily in the U.S.
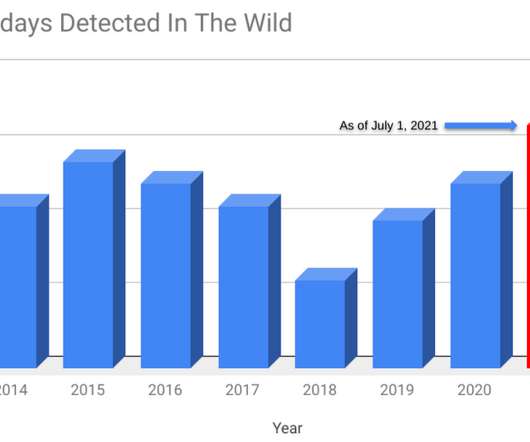
Security Affairs
JULY 14, 2021
Google security experts revealed that Russia-linked APT group targeted LinkedIn users with Safari zero-day. Security researchers from Google Threat Analysis Group (TAG) and Google Project Zero revealed that four zero-day vulnerabilities have been exploited in the wild earlier this year. The four security flaws were discovered earlier this year and affect Google Chrome, Internet Explorer, and WebKit browser engine.

AIIM
JULY 13, 2021
The shift to remote work has significantly impacted how organizations manage information. We sat down recently with Adam Storch, Vice President of Business Solutions, Micro Strategies, to discuss the effect advancing technology and the move to hybrid workplaces have had on information management. How are businesses using artificial intelligence (AI) to automate the processing and categorization of incoming information?

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

WIRED Threat Level
JULY 15, 2021
Security researchers say the group exploited a zero-day in Apple’s operating system to target European government officials over LinkedIn.

Data Breach Today
JULY 13, 2021
Flaw in Serv-U File-Transfer Software Unconnected to Orion Supply-Chain Attack Attackers have been actively exploiting a zero-day flaw in SolarWinds' Serv-U Managed File Transfer Server and Serv-U Secured FTP software, the security software vendor warns. SolarWinds has released patched versions that mitigate the flaw, discovered by Microsoft, and is urging users to update.
Security Affairs
JULY 16, 2021
The Joker malware is back, experts spotted multiple malicious apps on the official Google Play store that were able to evade scanners. Experts reported an uptick in malicious Android apps on the official Google Play store laced with the Joker mobile trojan. The Joker malware is a malicious code camouflaged as a system app and allows attackers to perform a broad range of malicious operations, including disable the Google Play Protect service , install malicious apps, generate fake reviews, and sh

AIIM
JULY 15, 2021
With SharePoint now included in Enterprise Microsoft 365 subscriptions, it is now more accessible than ever before. It is tempting for organizations to just jump right in and start setting it up without much forethought. SharePoint, however, is a sophisticated content management system. As a leader in the content management space, it offers a robust set of capabilities.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

WIRED Threat Level
JULY 16, 2021
The security researchers used an infrared photos and third-party hardware to best Microsoft's facial recognition tech.

Data Breach Today
JULY 16, 2021
Report: Cooperation Is Required to Protect US Critical Infrastructure A greater level of cooperation is needed between the DOD and DHS to ensure that U.S. critical infrastructure is protected against various cyberthreats, according to an inspector general's report. The SolarWinds attack showed the need for more coordination between the two departments.

Security Affairs
JULY 15, 2021
Security researchers have linked a new ransomware strain called Diavol to the Wizard Spider threat group behind the Trickbot botnet. BleepingComputer noted the ransomware families utilize the same I/O operations for file encryption queueing and use nearly identical command-line parameters for the same functionality. There may be some similarities, but as they’ve explained and SpearTip has validated, there are two interesting differences that make the direct connection improbable.

Schneier on Security
JULY 14, 2021
China is making sure that all newly discovered zero-day exploits are disclosed to the government. Under the new rules, anyone in China who finds a vulnerability must tell the government, which will decide what repairs to make. No information can be given to “overseas organizations or individuals” other than the product’s manufacturer.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
JULY 13, 2021
In response to mass protests, the country has been blocking social media and communication platforms since Sunday—an increasingly common action worldwide.

Data Breach Today
JULY 10, 2021
The oil and gas industry is yet again a victim of Agent Tesla malware A sophisticated campaign that uses remote access Trojans and malware-as-a-service threats for cyber espionage purposes has been targeting large international energy companies for at least a year, according to cybersecurity company Intezer.
Security Affairs
JULY 12, 2021
Researchers from Cyber News Team have spotted threat actors offering for sale 600 million LinkedIn profiles scraped from the platform, again. Original post: [link]. For the third time in the past four months, LinkedIn seems to have experienced another massive data scrape conducted by a malicious actor. Once again, an archive of data collected from hundreds of millions of LinkedIn user profiles surfaced on a hacker forum, where it’s currently being sold for an undisclosed sum.

Schneier on Security
JULY 12, 2021
Motherboard got its hands on one of those Anom phones that were really FBI honeypots. The details are interesting.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

WIRED Threat Level
JULY 12, 2021
Attackers are increasingly attuned to the power and potential of remote management software.

Data Breach Today
JULY 11, 2021
On-Premises Software Patched, SaaS to Come Online Again Miami-based software company Kaseya released patches on Sunday for its monitoring and management software that was exploited by a ransomware group. The patches take care of the last three vulnerabilities out of seven reported to Kaseya in early April but had yet to be fixed.

Security Affairs
JULY 10, 2021
Mint Mobile discloses a data breach, an unauthorized attacker gained access to subscribers’ account information and ported phone numbers. Mint Mobile is an American telecommunications company which sells mobile phone services and operates as an MVNO on T-Mobile’s cellular network in the United States. BleepingComputer reported that Mint Mobile has disclosed a data breach that exposed subscribers’ account information and ported phone numbers to another carrier.

Schneier on Security
JULY 15, 2021
First California. Then Virginia. Now Colorado. Here’s a good comparison of the three states’ laws.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

WIRED Threat Level
JULY 11, 2021
What you look for online is up to you—just make sure no one else is taking a peek.

Data Breach Today
JULY 16, 2021
Company Also Plans to Upgrade All Page Loads to HTTPS Google will soon release a security update to address eight vulnerabilities in its Chrome browser, including a high-severity zero-day flaw that's being exploited in the wild. It also plans to upgrade all Chrome page loads to HTTPS.

Security Affairs
JULY 16, 2021
Google Chrome 91.0.4472.164 addresses seven security vulnerabilities, including a high severity zero-day flaw exploited in the wild. Google has released Chrome 91.0.4472.164 for Windows, Mac, and Linux that addresses seven vulnerabilities, including a high severity zero-day vulnerability, tracked as CVE-2021-30563, that has been exploited in the wild.
Let's personalize your content