Malicious PDFs Flood the Web, Lead to Password-Snarfing
Threatpost
JUNE 15, 2021
SolarMarker makers are using SEO poisoning, stuffing thousands of PDFs with tens of thousands of pages full of SEO keywords & links to redirect to the malware.

Threatpost
JUNE 15, 2021
SolarMarker makers are using SEO poisoning, stuffing thousands of PDFs with tens of thousands of pages full of SEO keywords & links to redirect to the malware.
Security Affairs
JUNE 16, 2021
How AI is Transforming Data Governance? Consumers are becoming more aware of their rights, making data governance more relevant across organizations. Data governance is a set of standards, metrics, and processes that allow organizations to responsibly use consumer data.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
JUNE 16, 2021
TorrentFreak surveyed nineteen VPN providers, asking them questions about their privacy practices: what data they keep, how they respond to court order, what country they are incorporated in, and so on. Most interesting to me is the home countries of these companies. Express VPN is incorporated in the British Virgin Islands. NordVPN is incorporated in Panama.

Data Breach Today
JUNE 16, 2021
U.S Wants 16 Critical Infrastructure Entities Off-Limits to Attack At their Geneva summit meeting Wednesday, U.S. President Joe Biden told Russian President Vladimir Putin that if Russia continued to wage cyberattacks against the U.S., it would face retaliation.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Krebs on Security
JUNE 16, 2021
Authorities in Ukraine this week charged six people alleged to be part of the CLOP ransomware group , a cybercriminal gang said to have extorted more than half a billion dollars from victims. Some of CLOP’s victims this year alone include Stanford University Medical School , the University of California , and University of Maryland. A still shot from a video showing Ukrainian police seizing a Tesla, one of many high-end vehicles seized in this week’s raids on the Clop gang.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

WIRED Threat Level
JUNE 12, 2021
Before you use it to cartoonify your face, consider the risks to your data.

Data Breach Today
JUNE 14, 2021
Service Employees International Union 775 Benefits Group: PII and PHI Deleted A Seattle-based benefits administrator for unionized home healthcare and nursing home workers has reported a hacking incident affecting 140,000 individuals that involved deleting certain data.
Krebs on Security
JUNE 15, 2021
The U.S. Department of Justice (DOJ) last week announced the arrest of a 55-year-old Latvian woman who’s alleged to have worked as a programmer for Trickbot , a malware-as-a-service platform responsible for infecting millions of computers and seeding many of those systems with ransomware. Just how did a self-employed web site designer and mother of two come to work for one of the world’s most rapacious cybercriminal groups and then leave such an obvious trail of clues indicating her

Security Affairs
JUNE 12, 2021
McDonald’s fast-food chain disclosed a data breach, hackers have stolen information belonging to customers and employees from the US, South Korea, and Taiwan. McDonald’s, the world’s largest restaurant chain by revenue, has disclosed a data breach that impacted customers and employees from the US, South Korea, and Taiwan. The hackers compromised the system of the company and have stolen business contact info belonging to US employees and franchises, the company pointed out that

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

AIIM
JUNE 17, 2021
The notion of Artificial Intelligence has pervaded both the business world and popular culture. And, while Hollywood often portrays AI in a future world of smart robots with super-human characteristics, the truth is that AI technologies are already at work fueling important changes in the way business is conducted every day. Artificial Intelligence provides the potential to reengineer and improve core business processes that drive the success of any enterprise organization.

Data Breach Today
JUNE 16, 2021
Database Contains Website Visitor Activity Logs, But Not Personal Information The discovery of an unsecured database containing over 1 billion records related to CVS Health website visitor activity illustrates yet again how security missteps can potentially leave sensitive data exposed, some security experts say.

Krebs on Security
JUNE 18, 2021
In May 2019, KrebsOnSecurity broke the news that the website of mortgage settlement giant First American Financial Corp. [ NYSE:FAF ] was leaking more than 800 million documents — many containing sensitive financial data — related to real estate transactions dating back 16 years. This week, the U.S. Securities and Exchange Commission settled its investigation into the matter after the Fortune 500 company agreed to pay a paltry penalty of less than $500,000.

Security Affairs
JUNE 12, 2021
An authentication bypass flaw in the polkit auth system service used on most Linux distros can allow to get a root shell. An authentication bypass vulnerability in the polkit auth system service, tracked as CVE-2021-3560 , which is used on most Linux distros can allow an unprivileged attacker to get a root shell. “A flaw was found in polkit. When a requesting process disconnects from dbus-daemon just before the call to polkit_system_bus_name_get_creds_sync starts, the process cannot get a

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

WIRED Threat Level
JUNE 16, 2021
The company best known for its search engine is launching a new set of tools aimed at creating an “easy button” for protecting your data online.

Data Breach Today
JUNE 15, 2021
Data Was Left Unsecured by Unidentified Marketing Services Company Volkswagen and its Audi subsidiary are notifying 3.3 million people in the U.S and Canada of a breach of personal information by a marketing services supplier. Volkswagen says 90,000 of those affected may have also had their driver's license number, loan data and other personal information exposed.

AIIM
JUNE 15, 2021
In last week's article, we talked about the changing role of M365 within organizations, how it is governed, and how it connects with other content management solutions. Given its rapid evolution and adoption – particularly with the maturation of Office 365 and Cloud versions of SharePoint, we probably should have made a few points about brand terminology.

Security Affairs
JUNE 17, 2021
Researchers discovered an unprotected database belonging to CVS Health that was exposed online containing over a billion records. This week WebsitePlanet along with the researcher Jeremiah Fowler discovered an unsecured database, belonging to the US healthcare and pharmaceutical giant CVS Health, that was exposed online. The database was accessible to everyone without any type of authentication. “On March 21st, 2021 the WebsitePlanet research team in cooperation with Security Researcher

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
JUNE 15, 2021
Digital driver’s licenses have had a slow start in the US so far, but iOS 15 Wallet will give the nascent technology a serious push.

Data Breach Today
JUNE 13, 2021
Joint Effort with US to Maintain a Black List of Hackers Among Plan proposals The U.K. says it plans to turn the country into a global leader in cybersecurity, in partnership with the U.S, to counter threats ranging from ransomware to critical infrastructure attacks, according to a report by U.K. newspaper the Telegraph.
eSecurity Planet
JUNE 18, 2021
There’s a never ending cycle between the measures cybersecurity providers introduce to prevent or remediate cyber threats and the tactics cyber criminals use to get around these security measures. As soon as a security company develops a way to mitigate the latest threat, attackers develop a new threat to take its place. Artificial intelligence has emerged as a critical tool cybersecurity companies leverage to stay ahead of the curve.

Security Affairs
JUNE 15, 2021
The source code for the Paradise Ransomware has been released on a hacking forum allowing threat actors to develop their customized variant. The source code for the Paradise Ransomware has been released on the hacking forum XSS allowing threat actors to develop their own customized ransomware operation. The news of the availability of the source code was first reported by Tom Malka , a senior threat intelligence analyst for security firm Security, that reported it to BleepingComputer and The Rec

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

WIRED Threat Level
JUNE 13, 2021
Improvements designed to keep your email private, crack down on data stealing apps, and help you find lost devices are on their way.

Data Breach Today
JUNE 17, 2021
16 Critical Infrastructure Sectors Especially Off Limits - Or Else, President Warns U.S. President Joe Biden issued a clear warning to Russian President Vladimir Putin at their Geneva summit this week, saying that should Russia continue to launch cyberattacks against U.S. critical infrastructure sectors, or hack software supply chains, then Moscow should expect to see retaliation.

Schneier on Security
JUNE 17, 2021
General Packet Radio Service (GPRS) is a mobile data standard that was widely used in the early 2000s. The first encryption algorithm for that standard was GEA-1, a stream cipher built on three linear-feedback shift registers and a non-linear combining function. Although the algorithm has a 64-bit key, the effective key length is only 40 bits, due to “an exceptional interaction of the deployed LFSRs and the key initialization, which is highly unlikely to occur by chance.” GEA-1 was d
Security Affairs
JUNE 15, 2021
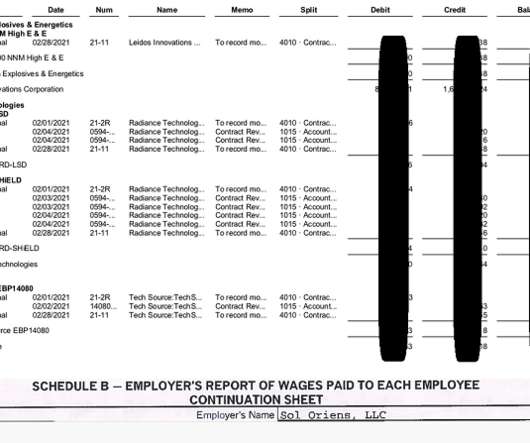
The REvil ransomware gang made the headlines again, the group hit the US nuclear weapons contractor Sol Oriens and stole the victim’s data. US nuclear weapons contractor Sol Oriens was hit by a cyberattack carried out by the REvil ransomware operators, which claims to have stolen data. Sol Orien provides consultant services to the National Nuclear Security Administration (NNSA), it confirmed to have suffered a cyber attack via Twitter.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

WIRED Threat Level
JUNE 12, 2021
While major carriers like AXA have backed away from covering ransoms, don't expect the industry at large to break the vicious cycle.

Data Breach Today
JUNE 18, 2021
Guidance Spells Out Best Risk Mitigation Practices The U.S. National Security Agency has released new guidance to help federal agencies as well as business enterprises protect their unified communications channels and voice/video over IP calls from cyberthreats.

Troy Hunt
JUNE 14, 2021
Today I'm very happy to welcome the Finnish government to Have I Been Pwned by granting their National Cyber Security Centre full and free access to query their government domains. API access to query their domains will give them greater visibility into the impact of data breaches on the Finnish government. Finland is now the 5th Nordic country and 21st national CERT to be onboarded with many more from around the globe to be announced shortly.
Let's personalize your content