11 Cybersecurity Vendors to Watch in 2021
Dark Reading
JUNE 10, 2021
The cybersecurity landscape continues to spawn new companies and attract new investments. Here is just a sampling of what the industry has to offer.

Dark Reading
JUNE 10, 2021
The cybersecurity landscape continues to spawn new companies and attract new investments. Here is just a sampling of what the industry has to offer.

Micro Focus
JUNE 9, 2021
Technology can play a key role in helping to reduce an organization’s environmental impact. At Micro Focus, our aim is to make sustainable and responsible business part of the way we operate. From lowering our energy consumption and waste materials, to helping our customers address their carbon footprint and adopt carbon friendly IT strategies –.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

WIRED Threat Level
JUNE 6, 2021
It's a growing threat for individual users and businesses alike—but there are ways to protect yourself.
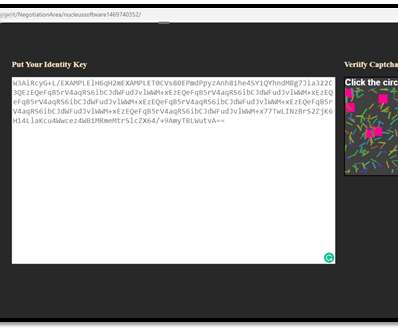
Security Affairs
JUNE 5, 2021
Cyble researchers investigated a recent attack on an India-based IT firm that was hit by the BlackCocaine Ransomware gang. Recently Cyber researchers for Cyble investigated an attack suffered by on May 30, 2021, by Nucleus Software, an India-based IT company in the Banking and Financial Services sector. The company reported the security breach to the Bombay Stock Exchange (BSE) and the National Stock Exchange of India (NSEI).

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Data Breach Today
JUNE 5, 2021
Dr. Claudia Natanson Describes Vision of U.K.’s New Self-Regulatory Body U.K. Cyber Security Council is a new self-regulatory body for the profession. It is tasked by the U.K. Government to execute their vision for the U.K. to be one of the safest places to work and do business online, says the chair of the Council’s Board of Trustees, Dr. Claudia Natanson.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

WIRED Threat Level
JUNE 11, 2021
The agency spent years running a secure phone network for criminals. So much for “going dark.”.

Security Affairs
JUNE 6, 2021
The REvil ransomware operators said in an interview on the “Russian OSINT” Telegram channel that they accidentally targeted United States-based firms. The recent attack against JBS Foods conducted by REvil ransomware gang (aka Sodinokibi) triggered the response of US authorities, US DoJ announced its decision to equate investigations into ransomware attacks with investigations into terrorism in the wake of the recent hacks.

Data Breach Today
JUNE 10, 2021
New Stand-Alone Firm Is Tasked With Combatting Digital Commerce Fraud RSA Security LLC has spun off its fraud and risk intelligence business into a stand-alone company named Outseer. The new company will be led by Reed Taussig as CEO, and it will serve a worldwide customer and partner community.
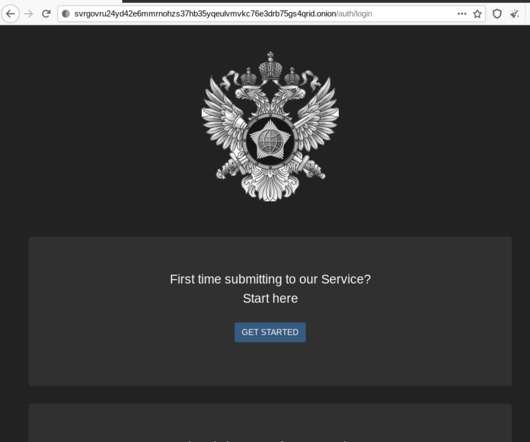
Krebs on Security
JUNE 7, 2021
KrebsOnSecurity recently had occasion to contact the Russian Federal Security Service (FSB), the Russian equivalent of the U.S. Federal Bureau of Investigation (FBI). In the process of doing so, I encountered a small snag: The FSB’s website said in order to communicate with them securely, I needed to download and install an encryption and virtual private networking (VPN) appliance that is flagged by at least 20 antivirus products as malware.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

WIRED Threat Level
JUNE 8, 2021
The company is enlisting your Echo and Ring devices into an internet-sharing mesh network starting Monday. It's not too late to opt out.

Security Affairs
JUNE 10, 2021
Google this week addressed 14 vulnerabilities in the Chrome browser, including a zero-day flaw that has been exploited in the wild. Google released security updates to address 14 vulnerabilities in the Chrome browser, including a zero-day issue that has been exploited in the wild. The most severe of these flaws, tracked as CVE-2021-30544, is a critical use-after-free issue that impacts BFCache.

Data Breach Today
JUNE 7, 2021
Decision to Pay Highlights Healthcare Sector Challenges The recent decision by a Massachusetts-based hospital to pay a ransom in exchange for promises by the attackers to destroy stolen data spotlights the difficult choices many healthcare entities face in the wake of cyberattacks.

AIIM
JUNE 8, 2021
The amount of data organizations must manage today is truly mind-boggling. Research shows that there are 2.5 quintillion bytes of data created each and every day. During the last two years alone 90% of the data in the world was generated. It’s no wonder that many organizations struggle to simply keep pace. And moving mountains of data from older legacy systems to modern cloud-based repositories can seem out of reach for most, regardless of the potential advantages of modernization.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

WIRED Threat Level
JUNE 7, 2021
LineStar Integrity Services was hacked around the same time as Colonial Pipeline, but radical transparency activists have brought the attack to light.

Security Affairs
JUNE 7, 2021
Cybercriminals in Russian underground forums have been invited to take part in competitions for hacking cryptocurrency and NFT. Several Russian underground forums have launched competitions for hacking cryptocurrency schema and Non-fungible token (NFT). “Over the past month, operators of one of the top Russian-language cybercrime forums have been running a “contest,” calling for the community to submit papers that examine how to target cryptocurrency-related technology.” reads a post
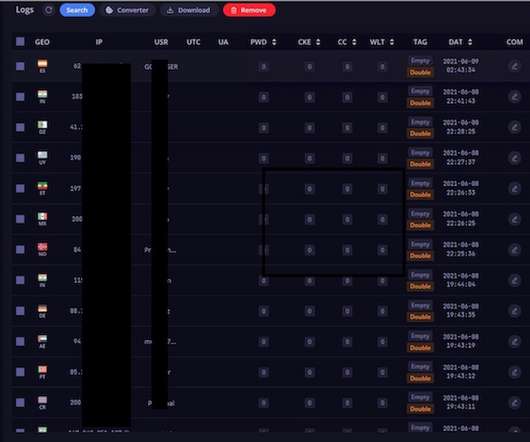
Data Breach Today
JUNE 10, 2021
Data Includes 1.5M Facebook Passwords, Valid Cookies Some 26 million passwords were exposed in a 1.2 terabyte batch of data found by NordLocker, a security company. It's workaday botnet data but highlights a hostile malware landscape, particularly for people still inclined to download pirated software.

The Last Watchdog
JUNE 9, 2021
Data leaks and data theft are part and parcel of digital commerce, even more so in the era of agile software development. Related: GraphQL APIs stir new exposures. Many of the high-profile breaches making headlines today are the by-product of hackers pounding away at Application Programming Interfaces (APIs) until they find a crease that gets them into the pathways of the data flowing between an individual user and myriad cloud-based resources.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
JUNE 8, 2021
You may not have heard of Fastly, but you felt its impact when sites didn’t load around the world Tuesday morning.

Security Affairs
JUNE 11, 2021
The Avaddon ransomware gang has shut down its operations and released the decryption keys to allow victims to recover their files for free. Good news for the victims of the Avaddon ransomware gang , the cybercrime group has shut down its operations and provided the decryption keys to BleepingComputer website. The group has also shut down its servers and deleted profiles on hacking forums, they also shut down their leak site.
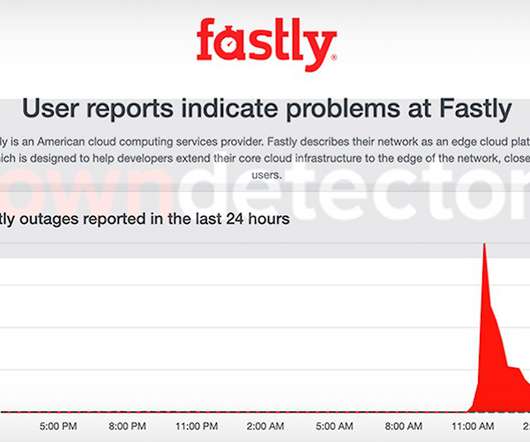
Data Breach Today
JUNE 8, 2021
Access to Amazon, Google, Twitter and Others Disrupted by Content Delivery Network Amazon, Google, Spotify and Twitter were among the sites that were unreachable Tuesday morning due to a configuration error at widely used content delivery network Fastly, which said the problem was resolved after about an hour, after which the disruptions would begin to abate.

AIIM
JUNE 10, 2021
As late as 2010, many end-users and solution providers viewed SharePoint as useful for project groups and document sharing – but more of an interesting tangent to the world of content management than “real” ECM. However, standalone ECM solutions at that time came at a very high cost. Many of these ECM solutions were built for high-volume scanning/capture applications and priced accordingly.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

WIRED Threat Level
JUNE 11, 2021
The credentials were part of a trove containing 1.2 terabytes of sensitive data extracted between 2018 and 2020.

Security Affairs
JUNE 6, 2021
Check Point Research (CPR) said that the Chinese APT group SharpPanda spent three years developing a new backdoor to spy on Asian governments. . Researchers from Check Point Research (CPR) discovered a new backdoor while investigating a cyber espionage campaign conducted by Chinese APT group SharpPanda and aimed at Southeast Asian government’s Ministry of Foreign Affairs.

Data Breach Today
JUNE 11, 2021
Experts Say Odd Case Offers Forewarning to Others The chief operating officer of a network security firm serving the healthcare sector has been charged by federal prosecutors with crimes stemming from an alleged cyberattack on an Atlanta, Georgia-area medical center in 2018. Some legal experts say the unusual case offers forewarnings to others.

Schneier on Security
JUNE 8, 2021
“If you think any of these systems are going to work as expected in wartime, you’re fooling yourself.” That was Bruce’s response at a conference hosted by U.S. Transportation Command in 2017, after learning that their computerized logistical systems were mostly unclassified and on the internet. That may be necessary to keep in touch with civilian companies like FedEx in peacetime or when fighting terrorists or insurgents.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

WIRED Threat Level
JUNE 10, 2021
The video game publisher confirmed the breach, which could be a boon to the shadowy world of cheat-makers.

Security Affairs
JUNE 9, 2021
The Spanish Ministry of Labor and Social Economy (MITES) was hit by a cyberattack and is working to restore impacted services. Spain’s Ministry of Labor and Social Economy (MITES) was hit by a cyberattack on Wednesday and is working to restore impacted services. MITES is a ministerial department with an annual budget of almost €39 million, charged with coordinating and supervising Spain’s employment, social economy, and corporate social responsibility policies.

Data Breach Today
JUNE 9, 2021
Without Resiliency Plans, Cloud Infrastructure Can Become Single Point of Failure Content delivery network Fastly says its global outage on Tuesday was caused by an unanticipated software bug, which it has now patched. IT experts caution that content delivery networks and other cloud services can become single points of failure if they go down, unless users have resiliency plans.
Let's personalize your content