3 Cybersecurity Myths to Bust
Dark Reading
MAY 11, 2021
Deeply rooted cybersecurity misconceptions are poisoning our ability to understand and defend against attacks.

Dark Reading
MAY 11, 2021
Deeply rooted cybersecurity misconceptions are poisoning our ability to understand and defend against attacks.

Security Affairs
MAY 13, 2021
The recent Colonial Pipeline attack highlights the dangers that are facing Critical Infrastructure worldwide. The attack perpetrated by hackers on oil company Colonial Pipeline highlights the dangers that are facing Industrial Control Systems (ICS) and the need for change in the information security landscape, The attack took place on May 7th where hackers used ransomware to cripple the defense of the company.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

WIRED Threat Level
MAY 9, 2021
There's a battle raging over how advertisers can target us on the web—or whether they should be able to target us at all.

Krebs on Security
MAY 14, 2021
The DarkSide ransomware affiliate program responsible for the six-day outage at Colonial Pipeline this week that led to fuel shortages and price spikes across the country is running for the hills. The crime gang announced it was closing up shop after its servers were seized and someone drained the cryptocurrency from an account the group uses to pay affiliates. “Servers were seized (country not named), money of advertisers and founders was transferred to an unknown account,” reads a

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Data Breach Today
MAY 8, 2021
Attackers have Co-Opted Malware For Data Exfiltration and Ransom, Group-IB Finds Attackers have co-opted the Hancitor malware downloader and recently used it to deliver Cuba ransomware as part of an email spam campaign for data exfiltration and ransom extortion, a new report by security firm Group-IB finds.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

WIRED Threat Level
MAY 8, 2021
An attack has crippled the company’s operations—and cut off a large portion of the East Coast’s fuel supply—in an ominous development for critical infrastructure.
Krebs on Security
MAY 10, 2021
How much is your payroll data worth? Probably a lot more than you think. One financial startup that’s targeting the gig worker market is offering up to $500 to anyone willing to hand over the payroll account username and password given to them by their employer, plus a regular payment for each month afterwards in which those credentials still work.

Data Breach Today
MAY 10, 2021
Report: DarkSide Ransomware Gang Infected Fuel Supplier Colonial Pipeline Company has restored smaller pipelines that ship fuels to the U.S. East Coast after a ransomware incident, but its larger ones are still offline as it assesses safety. Citing U.S. officials, the Associated Press reports the company was infected by the DarkSide ransomware group.

Security Affairs
MAY 11, 2021
Adobe confirmed that a zero-day vulnerability affecting Adobe Reader for Windows has been exploited in the wild in limited attacks. Adobe security updates for May 2021 address at least 43 CVEs in Experience Manager, InDesign, Illustrator, InCopy, Adobe Genuine Service, Acrobat and Reader, Magento, Creative Cloud Desktop, Media Encoder, Medium, and Animate.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

WIRED Threat Level
MAY 10, 2021
Emails from the Epic Games lawsuit show Apple brass discussing how to handle a 2015 iOS hack. The company never directly notified affected users.

Krebs on Security
MAY 11, 2021
Microsoft today released fixes to plug at least 55 security holes in its Windows operating systems and other software. Four of these weaknesses can be exploited by malware and malcontents to seize complete, remote control over vulnerable systems without any help from users. On deck this month are patches to quash a wormable flaw, a creepy wireless bug, and yet another reason to call for the death of Microsoft’s Internet Explorer (IE) web browser.

Data Breach Today
MAY 10, 2021
Pharmacy Administration Vendor, EMR Hosting Firm Among Latest Victims Two companies that serve the healthcare sector have reported disruptive cyber incidents affecting their clients, the latest in a string of similar supply chain incidents.

Security Affairs
MAY 9, 2021
U.S. CISA has published an analysis of the FiveHands ransomware, the same malware that was analyzed a few days ago by researchers from FireEye’s Mandiant experts. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published an analysis of the FiveHands ransomware that was recently detailed by FireEye’s Mandiant. At the end of April, researchers from FireEye’s Mandiant revealed that a sophisticated cybercrime gang tracked as UNC2447 has exploited a zero-day issue ( CVE-2021-2001

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

WIRED Threat Level
MAY 14, 2021
Stopping payments would go a long way to stopping ransomware. But the choice is never quite so easy.

AIIM
MAY 11, 2021
A staple of many Information Technology (IT) policy suites is the Acceptable Use Policy (AUP), intended to govern what people working in the organization can and cannot do with the technology we provide them. IIM professionals and consultants push to have these kinds of policies in place, and countless templates and best practices are available on the Internet to use as a starting point if we don't have one already.

Data Breach Today
MAY 11, 2021
City Shuts Down Websites, Systems Tulsa city officials shut down systems and websites after a Sunday ransomware attack, making it impossible for residents to gain online access to many services.
Security Affairs
MAY 9, 2021
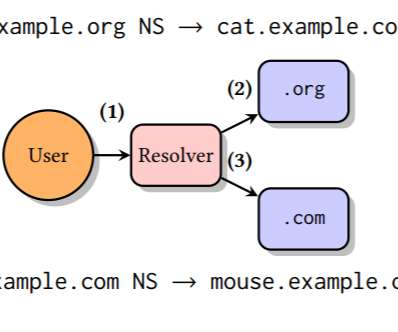
A flaw in some DNS resolvers, tracked as TsuNAME, can allow attackers to launch DDoS attacks against authoritative DNS servers. Researchers at SIDN Labs (the R&D team of the registry for.nl domains), InternetNZ (the registry for.nz domains), and the Information Science Institute at the University of Southern California has discovered a vulnerability, named TsuNAME, in some DNS resolvers.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
MAY 11, 2021
As the White House gets involved in the response, the group behind the malware is scrambling.

The Last Watchdog
MAY 12, 2021
A permissions glut is giving rise to an explosion of new exposures in modern business networks. Related: Securing digital identities. Companies are adopting multi-cloud and hybrid cloud infrastructures and relying on wide-open app development like never before. In doing so, permissions to make myriad software connections are proliferating. Taken together these man-to-machine and machine-to-machine connections result in cool new digital services.

Data Breach Today
MAY 14, 2021
Colonial Pipeline Attack Used DarkSide Malware The gang behind DarkSide ransomware, which U.S. authorities say was used in the attack against Colonial Pipeline Co., says it's closed its ransomware-as-a-service operation after losing access to part of its infrastructure.

Security Affairs
MAY 10, 2021
The U.S. FBI confirmed that the attack against the Colonial Pipeline over the weekend was launched by the Darkside ransomware gang. The U.S. Federal Bureau of Investigation confirmed that the Colonial Pipeline was shut down due to a cyber attack carried out by the Darkside ransomware gang. “The FBI confirms that the Darkside ransomware is responsible for the compromise of the Colonial Pipeline networks.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

WIRED Threat Level
MAY 9, 2021
The tech giant wants to push its billions of users—and the rest of the industry—to enable multifactor authentication by default.

The Last Watchdog
MAY 11, 2021
By patiently slipping past the best cybersecurity systems money can buy and evading detection for 16 months, the perpetrators of the SolarWinds hack reminded us just how much heavy lifting still needs to get done to make digital commerce as secure as it needs to be. Related: DHS launches 60-day cybersecurity sprints. Obviously, one change for the better would be if software developers and security analysts paid much closer attention to the new and updated coding packages being assembled and depl

Data Breach Today
MAY 14, 2021
The Debate Over Impact of Colonial Pipeline's Apparent Ransom Payment Some cybersecurity experts question the contentions of Speaker of the House Nancy Pelosi and another member of Congress, who say a $5 million ransom reportedly paid by Colonial Pipeline Co. after being hit by DarkSide ransomware would serve as a catalyst for attacks on other critical infrastructure providers.

Security Affairs
MAY 8, 2021
A cyberattack forced the shutdown of one of the largest pipelines in the United States, the Colonial Pipeline facility in Pelham, Alabama. The Colonial Pipeline facility in Pelham, Alabama was hit by a cybersecurity attack, its operators were forced to shut down its systems. The pipeline allows carrying 2.5 million barrels of refined gasoline and jet fuel each day up the East Coast from Texas to New York, it covers 45 percent of the East Coast’s fuel supplies. “The operator of the system,

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

WIRED Threat Level
MAY 13, 2021
The so-called Frag Attack vulnerabilities could let hackers steal data or compromise connected gadgets.

The Last Watchdog
MAY 10, 2021
The value of sharing threat intelligence is obvious. It’s much easier to blunt the attack of an enemy you can clearly see coming at you. Related: Supply chains under siege. But what about trusted allies who unwittingly put your company in harm’s way? Third-party exposures can lead to devastating breaches, just ask any Solar Winds first-party customer.

Data Breach Today
MAY 11, 2021
Acting CISA Director Tells Lawmakers FBI, Not Company, Alerted Agency CISA is still awaiting more technical details from Colonial Pipeline about the Friday ransomware attack that forced it to shut down its operations, Brandon Wales, the agency's acting director, told a Senate committee that's probing the attack and other cybersecurity incidents.
Let's personalize your content