Microsoft's Dream of Decentralized IDs Enters the Real World
WIRED Threat Level
MARCH 2, 2021
The company will launch a public preview of its identification platform this spring—and has already tested it at the UK's National Health Service.

WIRED Threat Level
MARCH 2, 2021
The company will launch a public preview of its identification platform this spring—and has already tested it at the UK's National Health Service.

erwin
MARCH 4, 2021
Modern data governance is a strategic, ongoing and collaborative practice that enables organizations to discover and track their data, understand what it means within a business context, and maximize its security, quality and value. It is the foundation for regulatory compliance and de-risking operations for competitive differentiation and growth. However, while digital transformation and other data-driven initiatives are desired outcomes, few organizations know what data they have or where it i
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Threatpost
MARCH 1, 2021
A snapshot of the 2020 mobile threat landscape reveals major shifts toward adware and threats to online banks.
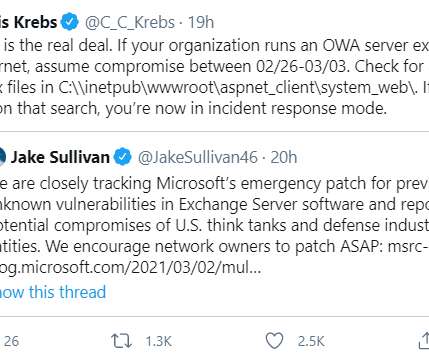
Krebs on Security
MARCH 5, 2021
At least 30,000 organizations across the United States — including a significant number of small businesses, towns, cities and local governments — have over the past few days been hacked by an unusually aggressive Chinese cyber espionage unit that’s focused on stealing email from victim organizations, multiple sources tell KrebsOnSecurity.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

WIRED Threat Level
MARCH 5, 2021
A single group appears to have infiltrated tens of thousands of Microsoft Exchange servers in an ongoing onslaught.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Security Affairs
MARCH 3, 2021
Cybersecurity firm Qualys seems to have suffered a data breach, threat actors allegedly exploited zero-day flaw in their Accellion FTA server. Cybersecurity firm Qualys is the latest victim of a cyber attack, the company was likely hacked by threat actors that exploited a zero-day vulnerability in their Accellion FTA server. A couple of weeks ago, security experts from FireEye linked a series of cyber attacks against organizations running Accellion File Transfer Appliance (FTA) servers to the c
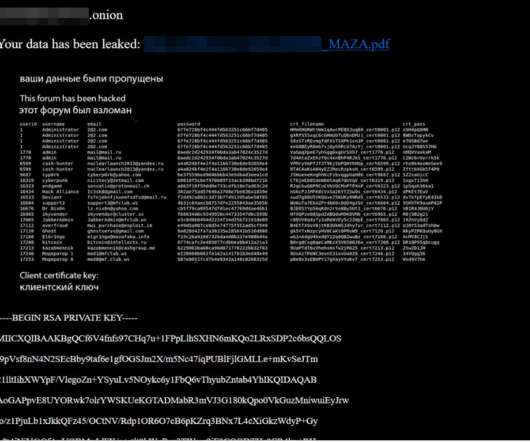
Krebs on Security
MARCH 4, 2021
Over the past few weeks, three of the longest running and most venerated Russian-language online forums serving thousands of experienced cybercriminals have been hacked. In two of the intrusions, the attackers made off with the forums’ user databases, including email and Internet addresses and hashed passwords. Members of all three forums are worried the incidents could serve as a virtual Rosetta Stone for connecting the real-life identities of the same users across multiple crime forums.

WIRED Threat Level
FEBRUARY 28, 2021
The transparency group DDoSecrets says it will make the 70GB of passwords, private posts, and more available to researchers, journalists, and social scientists.

Data Breach Today
MARCH 1, 2021
Flaw Could Enable Access to Secret Encryption Key A critical authentication bypass vulnerability could enable hackers to remotely compromise programmable logic controllers made by industrial automation giant Rockwell Automation, according to the cybersecurity company Claroty. Rockwell has issued mitigation recommendations.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m
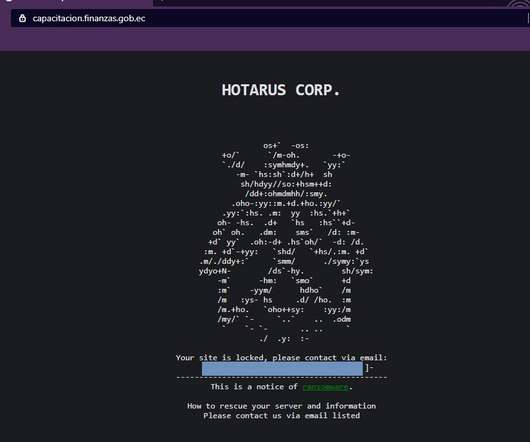
Security Affairs
FEBRUARY 27, 2021
‘Hotarus Corp’ Ransomware operators hacked Ecuador’s largest private bank, Banco Pichincha, and the country’s Ministry of Finance. ?A cybercrime group called ‘Hotarus Corp’ has breached the Ecuador’s largest private bank, Banco Pichincha, and the local Ministry of Finance (the Ministerio de Economía y Finanzas de Ecuador).

Krebs on Security
MARCH 2, 2021
Microsoft Corp. today released software updates to plug four security holes that attackers have been using to plunder email communications at companies that use its Exchange Server products. The company says all four flaws are being actively exploited as part of a complex attack chain deployed by a previously unidentified Chinese cyber espionage group.

WIRED Threat Level
FEBRUARY 27, 2021
Plus: Firefox blocks more tracking, how to fight a robodog, and more of the week’s top security news.

Data Breach Today
MARCH 3, 2021
Sophisticated Attackers Took the Time to Master a 20-Year-Old Product, FireEye Says Using a nearly 20-year-old file-transfer product: What could go wrong? Among the many lessons to be learned from the Accellion File Transfer Application mess is this: Attackers will devote substantial resources to reverse engineering hardware, software or a service if there's a financial upside.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Security Affairs
MARCH 5, 2021
US managed service provider CompuCom was the victim of a cyberattack that partially disrupted its operations, experts believe it was a ransomware attack. US managed service provider CompuCom was the victim of a cyberattack that partially disrupted its services and some of its operations. Even if the company initially did not provide technical details about the attack, security experts speculated the involvement of ransomware due to the observed effects.
Krebs on Security
MARCH 2, 2021
PrismHR , a company that sells technology used by other firms to help more than 80,000 small businesses manage payroll, benefits, and human resources, has suffered what appears to be an ongoing ransomware attack that is disrupting many of its services. Hopkinton, Mass.-based PrismHR handles everything from payroll processing and human resources to health insurance and tax forms for hundreds of “professional employer organizations” (PEOs) that serve more than two million employees.

WIRED Threat Level
MARCH 4, 2021
It's the digital equivalent of leaving your windows or doors open when you leave the house—and in some cases, leaving them open all the time.

Data Breach Today
MARCH 4, 2021
Microsoft, FireEye Find Additional Payloads Used During Supply Chain Attack Researchers with Microsoft and FireEye are disclosing additional malware used by the hacking group that targeted SolarWinds in December. These second-stage malware variants appear to have been deployed after organizations downloaded the "Sunburst" backdoor hidden in a software update.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Security Affairs
MARCH 3, 2021
A researcher received a $50,000 bug bounty by Microsoft for having reported a vulnerability that could’ve allowed to hijack any account. Microsoft has awarded the security researcher Laxman Muthiyah $50,000 for reporting a vulnerability that could have allowed anyone to hijack users’ accounts without consent. According to the expert, the vulnerability only impacts consumer accounts.

AIIM
MARCH 2, 2021
Have you ever wondered how companies like Amazon and Netflix recommend content based on our past viewing or purchasing? Recommendation engines are fueled by techniques in Machine Learning and AI. There are many benefits to consumers and companies, but what are the dangers and downsides of recommendation engines? That is the subject of my newest AIIM On Air interview with Michael Schrage.

WIRED Threat Level
MARCH 5, 2021
The 75-year-old antivirus entrepreneur faces up to 80 years in prison if convicted.

Data Breach Today
MARCH 2, 2021
Hackers Threatened to Leak Sensitive Data The cryptocurrency company Tether has refused to pay a ransom of 500 bitcoins ($24 million) after hackers threatened to leak sensitive data if the company failed to pay.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

Security Affairs
FEBRUARY 27, 2021
A critical authentication bypass vulnerability could be exploited by remote attackers to Rockwell Automation programmable logic controllers (PLCs). A critical authentication bypass vulnerability, tracked as CVE-2021-22681 , can be exploited by remote attackers to compromise programmable logic controllers (PLCs) manufactured by Rockwell Automation. The vulnerability was independently reported to Rockwell by researchers at the Soonchunhyang University in South Korea, Claroty , and Kaspersky. ̶

AIIM
MARCH 4, 2021
To succeed on the Digital Transformation journey, requires a strategy, planning, and the design of a better information ecosystem - what we refer to as Intelligent Information Management (IIM). The first step on this journey is to get all of your information into the information ecosystem. This is a practice called Capture. Let’s take a deeper look at this first step of digital transformation.

WIRED Threat Level
MARCH 4, 2021
The full extent of the Solarwinds hack and Hafnium's attack on Microsoft Exchange Server may never be known.

Data Breach Today
MARCH 4, 2021
Forecast Calls for Backdoored Email and Possibly Ransomware, Cryptominers One day after Microsoft disclosed four serious flaws in Microsoft Exchange email servers, attackers are going on a wide hunt for vulnerable machines, experts say. There's not only a risk of backdoored email accounts, but also ransomware and cryptominers.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Security Affairs
MARCH 4, 2021
Group-IB published a report titled “Ransomware Uncovered 2020-2021 ”. analyzes ransomware landscape in 2020 and TTPs of major threat actors. Group-IB , a global threat hunting and adversary-centric cyber intelligence company, has presented its new report “Ransomware Uncovered 2020-2021 ”. The research dives deep into the global ransomware outbreak in 2020 and analyzes major players’ TTPs (tactics, techniques, and procedures).

Schneier on Security
MARCH 1, 2021
Early in 2020, cyberspace attackers apparently working for the Russian government compromised a piece of widely used network management software made by a company called SolarWinds. The hack gave the attackers access to the computer networks of some 18,000 of SolarWinds’s customers, including US government agencies such as the Homeland Security Department and State Department, American nuclear research labs, government contractors, IT companies and nongovernmental agencies around the world.

WIRED Threat Level
MARCH 1, 2021
One couple living in Yangon explain the impact of the military coup's terrifying censorship measures.
Let's personalize your content