4 Clues to Spot a Bot Network
Dark Reading
JANUARY 27, 2021
Protect against misinformation and disinformation campaigns by learning how to identify the bot networks spreading falsehoods.

Dark Reading
JANUARY 27, 2021
Protect against misinformation and disinformation campaigns by learning how to identify the bot networks spreading falsehoods.

WIRED Threat Level
JANUARY 24, 2021
Zombie versions of Adobe’s troubled software can still cause problems in systems around the world. Security Security / Security News
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Krebs on Security
JANUARY 27, 2021
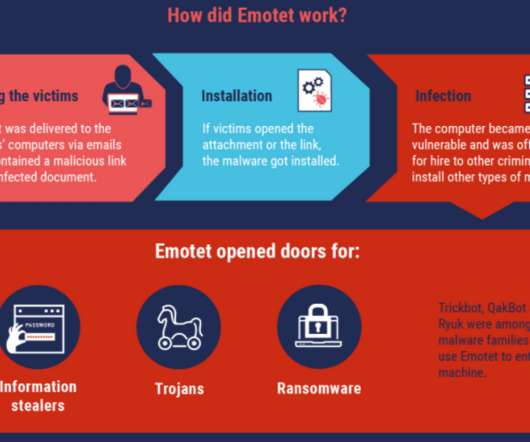
Authorities across Europe on Tuesday said they’d seized control over Emotet , a prolific malware strain and cybercrime-as-service operation. Investigators say the action could help quarantine more than a million Microsoft Windows systems currently compromised with malware tied to Emotet infections. First surfacing in 2014, Emotet began as a banking trojan, but over the years it has evolved into one of the more aggressive platforms for spreading malware that lays the groundwork for ransomwa
Data Breach Today
JANUARY 25, 2021
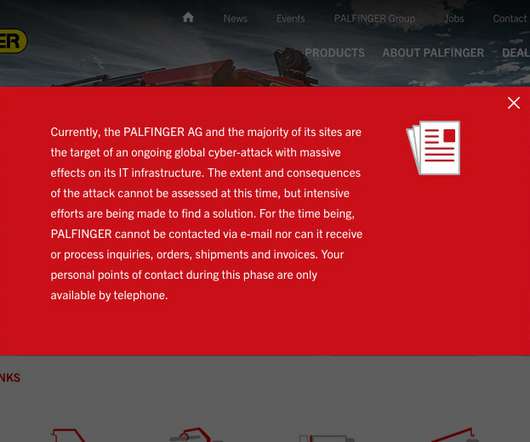
Unknown Attack Has Disrupted the Company's Global IT Infrastructure The Austrian construction equipment manufacturing firm Palfinger AG reports being hit with a cyberattack that has knocked the majority of its worldwide IT infrastructure offline, eliminating its ability to use email and conduct business.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, CTO of Betterworks, will explore a practical framework to transform Generative AI prototypes into

The Last Watchdog
JANUARY 25, 2021
SolarWinds and Mimecast are long-established, well-respected B2B suppliers of essential business software embedded far-and-wide in company networks. Related: Digital certificates destined to play key role in securing DX. Thanks to a couple of milestone hacks disclosed at the close of 2020 and start of 2021, they will forever be associated with putting supply-chain vulnerabilities on the map.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Krebs on Security
JANUARY 29, 2021
The unprecedented volume of unemployment insurance fraud witnessed in 2020 hasn’t abated, although news coverage of the issue has largely been pushed off the front pages by other events. But the ID theft problem is coming to the fore once again: Countless Americans will soon be receiving notices from state regulators saying they owe thousands of dollars in taxes on benefits they never received last year.
Data Breach Today
JANUARY 29, 2021
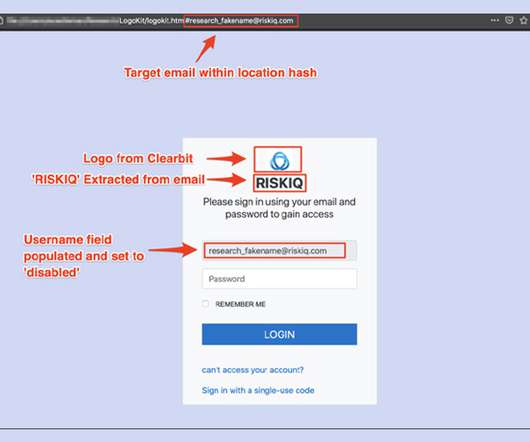
Researchers: 'LogoKit' Found on 700 Domains Researchers at the security firm RiskIQ have discovered a phishing kit they call "LogoKit" that fraudsters can use to easily change lures, logos and text in real time to help trick victims into opening up messages and clicking on malicious links.
Thales Cloud Protection & Licensing
JANUARY 26, 2021
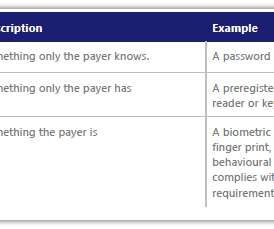
The Future of Payments Security. madhav. Tue, 01/26/2021 - 09:17. Criminals use a wide range of methods to commit fraud. The increasing trend of using mobile payments for in-store purchases (especially during the pandemic) is leading criminals to increasingly focus their efforts on defrauding people through online fraud and scams. Fraud and scams move to the web.

AIIM
JANUARY 28, 2021
"How do we translate an interactive in-person conference experience into a virtual experience?". This was the big question that immediately hit me at exactly at 5:00PM on March 5th, 2020. I remember the moment – we had just closed off a fantastic week with the AIIM Tribe in Dallas, Texas, for The AIIM Conference 2020. I've been leading the events team to produce and coordinate The AIIM Conference for a long time.

Advertisement
Generative AI is upending the way product developers & end-users alike are interacting with data. Despite the potential of AI, many are left with questions about the future of product development: How will AI impact my business and contribute to its success? What can product managers and developers expect in the future with the widespread adoption of AI?
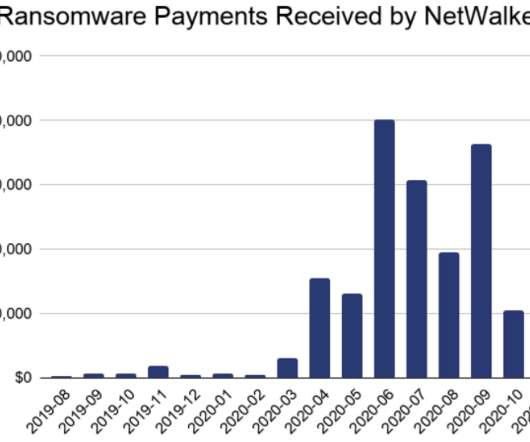
Krebs on Security
JANUARY 27, 2021
U.S. and Bulgarian authorities this week seized the darkweb site used by the NetWalker ransomware cybercrime group to publish data stolen from its victims. In connection with the seizure, a Canadian national suspected of extorting more than $27 million through the spreading of NetWalker was charged in a Florida court. The victim shaming site maintained by the NetWalker ransomware group, after being seized by authorities this week.

Data Breach Today
JANUARY 27, 2021
Banning Ransom Payments and Unleashing Offensive Hacking Teams Being Mooted With ransomware continuing to fuel a massive surge in illicit profits, some experts have been calling on governments to launch offensive hacking teams to target cybercrime cartels. They're also calling for a review of cyber insurance payouts being used to fund ransoms.
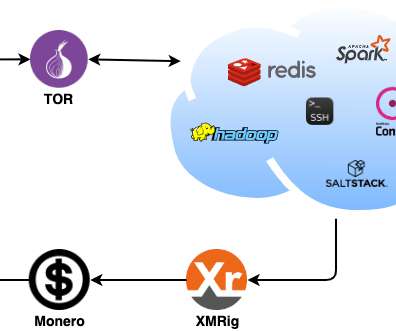
Security Affairs
JANUARY 25, 2021
Zscaler’s research team recently spotted a Linux-based malware family, tracked as DreamBus botnet, targeting Linux servers. Researchers at Zscaler’s ThreatLabZ research team recently analyzed a Linux-based malware family, tracked as DreamBus Botnet, which is a variant of SystemdMiner. The bot is composed of a series of Executable and Linkable Format (ELF) binaries and Unix shell scripts. .

The Guardian Data Protection
JANUARY 26, 2021
Information commissioner says data was voluntarily deleted amid concerns about ‘weak’ enforcement The Conservative party acted illegally when it collected data on the ethnic backgrounds of 10 million voters before the 2019 general election, the information commissioner has told a committee of MPs. However, Elizabeth Denham insisted there had been no need to issue an enforcement notice against the party, as it had voluntarily deleted the data it held after a “recommendation” from her office.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Threatpost
JANUARY 27, 2021
Researchers publicly disclosed flaws in ADT's LifeShield DIY HD Video Doorbell, which could have allowed local attackers to access credentials, video feeds and more.
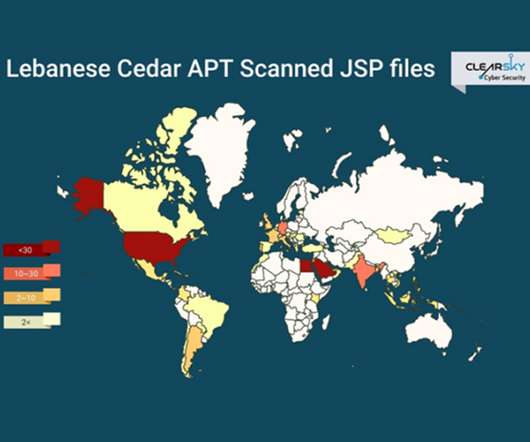
Data Breach Today
JANUARY 29, 2021
Researchers: Lebanese Cedar's Campaigns Expand Beyond Middle East An APT group known as Lebanese Cedar has launched a cyberespionage campaign targeting telecommunication companies and ISPs, according to the Israeli security firm ClearSky, which says the attacks have spread beyond the Middle East to the U.S. and Europe.

Security Affairs
JANUARY 25, 2021
Packaging giant WestRock disclosed a ransomware attack that impacted its information technology (IT) and operational technology (OT) systems. American corrugated packaging company WestRock announced it was the victim of a ransomware attack that impacted its information technology (IT) and operational technology (OT) systems. WestRock did not share details about the security incident, it only confirmed that its staff discovered the attack on January 23.

Schneier on Security
JANUARY 26, 2021
I think this is the largest data breach of all time: 220 million people. ( Lots more stories are in Portuguese.).

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Threatpost
JANUARY 27, 2021
An anonymous researcher identified bugs in the software’s kernel and WebKit browser engine that are likely part of an exploit chain.

Data Breach Today
JANUARY 23, 2021
Incident Forced Intel to Release Results Earlier Than Planned Intel is investigating an incident in which an unauthorized person accessed a portion of the company's latest quarterly financial report, forcing the chipmaker to release its earnings slightly earlier than planned.

Security Affairs
JANUARY 23, 2021
The Hacker News reported in exclusive that the security firm SonicWall was hacked as a result of a coordinated attack on its internal systems. TheHackerNews revealed in an exclusive that the security provider SonicWall was hacked on Friday. The company was targeted with a coordinated attack on its internal systems, threat actors exploited zero-day vulnerabilities in their VPN solutions, such as NetExtender VPN client version 10.x and Secure Mobile Access ( SMA ). “The San Jose-based compa
Daymark
JANUARY 26, 2021
As COVID forced organizations around the world to send their workforce home, creating the work from home (WFH) phenomenon, IT and security teams rapidly focused on Zero Trust approaches to security to mitigate challenges of enabling secure remote work. Modern workplace employees are getting their work done any way they can these days – using personal devices, sharing data through new services, maxing out home WiFi, and collaborating outside the confines of traditional corporate network security.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Rocket Software
JANUARY 29, 2021
“Women belong in all places where decisions are made.” –Ruth Bader Ginsburg. Although this statement may have been revolutionary at the time, the number of women in the workforce is rapidly changing; in the U.S., it’s risen by 47 percent in 2020 alone. Over the past few years, thanks to the help of revolutionary women such as Ruth Bader Ginsburg, women are making bigger strides in all industries—including into the White House.

Data Breach Today
JANUARY 25, 2021
Researchers: 33,000 Vulnerable Servers Could Be Used to Amplify Attacks Threat actors are exploiting vulnerable Microsoft Remote Desktop Protocol servers to amplify DDoS attacks, according to a report from Netscout, which offers mitigation advice.
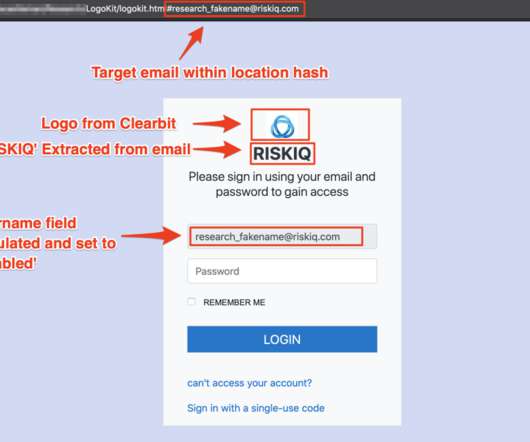
Security Affairs
JANUARY 28, 2021
Researchers from RiskIQ have discovered a new phishing kit dubbed LogoKit that dynamically compose phishing content. Researchers from RiskIQ discovered a new phishing kit that outstands for its ability to dynamically create phishing messages to target specific users. LogoKit has a modular structure that makes it easy to implement a phishing-as-as-Service model.

Dark Reading
JANUARY 28, 2021
Even today, on Data Privacy Day, privacy professionals give you permission to admit you actually love targeted ads.

Advertisement
Start-ups & SMBs launching products quickly must bundle dashboards, reports, & self-service analytics into apps. Customers expect rapid value from your product (time-to-value), data security, and access to advanced capabilities. Traditional Business Intelligence (BI) tools can provide valuable data analysis capabilities, but they have a barrier to entry that can stop small and midsize businesses from capitalizing on them.

OpenText Information Management
JANUARY 27, 2021
Legalweek(year), like everything else in our lives at present, will look different this year. We won’t be gathering in NYC to socialize and have face-to-face conversations; we won’t be going out for dinner or drinks. You might be asking yourself – why attend? During your busy work schedule, why set time aside to engage in … The post Go further, faster without leaving your home office appeared first on OpenText Blogs.

Data Breach Today
JANUARY 29, 2021
The latest edition of the ISMG Security Report features an analysis of this week’s police takedowns of Emotet and Netwalker cybercrime operations. Also featured: Updates on passwordless authentication and the use of deception technology.

Security Affairs
JANUARY 27, 2021
A joint operation of U.S. and EU law enforcement authorities allowed the seizure of the leak sites used by NetWalker ransomware operators. Law enforcement authorities in the U.S. and Europe have seized the dark web sites used by NetWalker ransomware operators. The authorities also charged a Canadian national involved in the NetWalker ransomware operations. “The Department of Justice today announced a coordinated international law enforcement action to disrupt a sophisticated form of ransom
Let's personalize your content