4 Clues to Spot a Bot Network
Dark Reading
JANUARY 27, 2021
Protect against misinformation and disinformation campaigns by learning how to identify the bot networks spreading falsehoods.

Dark Reading
JANUARY 27, 2021
Protect against misinformation and disinformation campaigns by learning how to identify the bot networks spreading falsehoods.

WIRED Threat Level
JANUARY 24, 2021
Zombie versions of Adobe’s troubled software can still cause problems in systems around the world. Security Security / Security News
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Krebs on Security
JANUARY 27, 2021
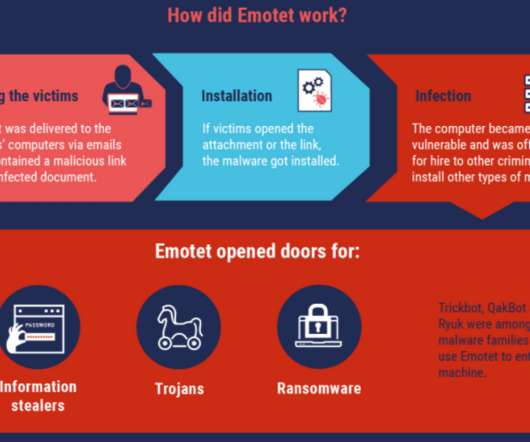
Authorities across Europe on Tuesday said they’d seized control over Emotet , a prolific malware strain and cybercrime-as-service operation. Investigators say the action could help quarantine more than a million Microsoft Windows systems currently compromised with malware tied to Emotet infections. First surfacing in 2014, Emotet began as a banking trojan, but over the years it has evolved into one of the more aggressive platforms for spreading malware that lays the groundwork for ransomwa

Security Affairs
JANUARY 27, 2021
A joint operation of U.S. and EU law enforcement authorities allowed the seizure of the leak sites used by NetWalker ransomware operators. Law enforcement authorities in the U.S. and Europe have seized the dark web sites used by NetWalker ransomware operators. The authorities also charged a Canadian national involved in the NetWalker ransomware operations. “The Department of Justice today announced a coordinated international law enforcement action to disrupt a sophisticated form of ransom

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.
Data Breach Today
JANUARY 25, 2021
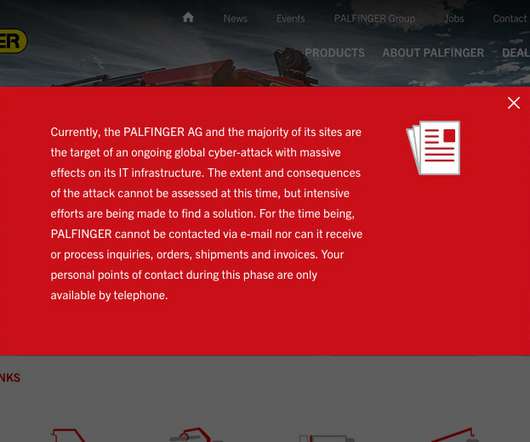
Unknown Attack Has Disrupted the Company's Global IT Infrastructure The Austrian construction equipment manufacturing firm Palfinger AG reports being hit with a cyberattack that has knocked the majority of its worldwide IT infrastructure offline, eliminating its ability to use email and conduct business.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Krebs on Security
JANUARY 29, 2021
The unprecedented volume of unemployment insurance fraud witnessed in 2020 hasn’t abated, although news coverage of the issue has largely been pushed off the front pages by other events. But the ID theft problem is coming to the fore once again: Countless Americans will soon be receiving notices from state regulators saying they owe thousands of dollars in taxes on benefits they never received last year.
Security Affairs
JANUARY 28, 2021
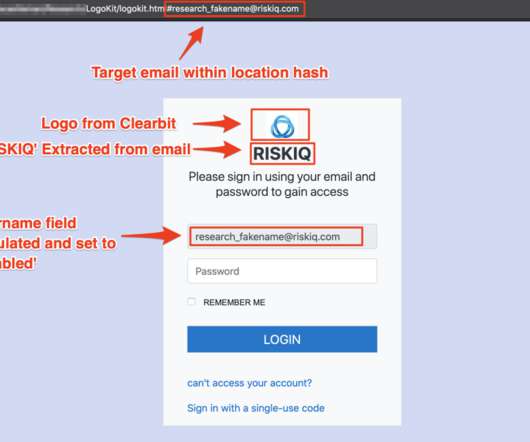
Researchers from RiskIQ have discovered a new phishing kit dubbed LogoKit that dynamically compose phishing content. Researchers from RiskIQ discovered a new phishing kit that outstands for its ability to dynamically create phishing messages to target specific users. LogoKit has a modular structure that makes it easy to implement a phishing-as-as-Service model.
Data Breach Today
JANUARY 29, 2021
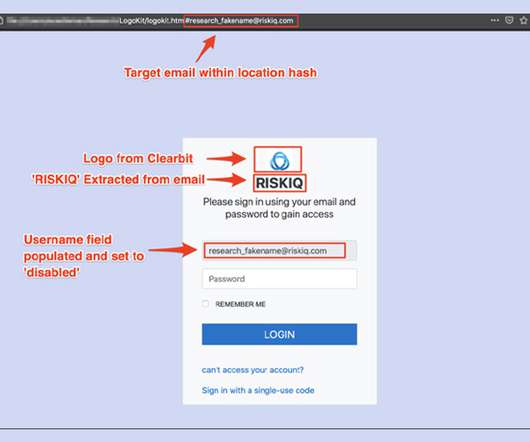
Researchers: 'LogoKit' Found on 700 Domains Researchers at the security firm RiskIQ have discovered a phishing kit they call "LogoKit" that fraudsters can use to easily change lures, logos and text in real time to help trick victims into opening up messages and clicking on malicious links.

WIRED Threat Level
JANUARY 29, 2021
A new California law prohibits efforts to trick consumers into handing over data or money. A bill in Washington state copies the language.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m
Krebs on Security
JANUARY 27, 2021
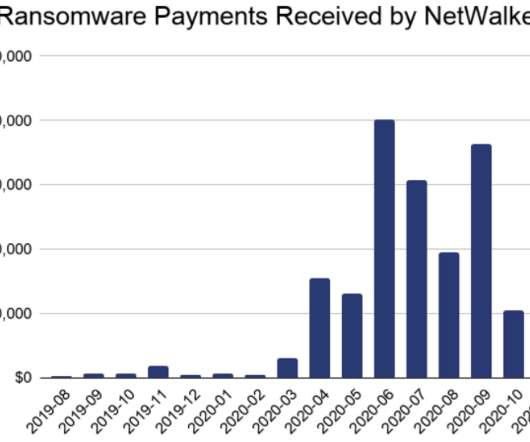
U.S. and Bulgarian authorities this week seized the darkweb site used by the NetWalker ransomware cybercrime group to publish data stolen from its victims. In connection with the seizure, a Canadian national suspected of extorting more than $27 million through the spreading of NetWalker was charged in a Florida court. The victim shaming site maintained by the NetWalker ransomware group, after being seized by authorities this week.
Security Affairs
JANUARY 25, 2021
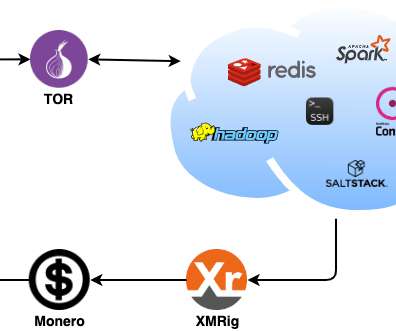
Zscaler’s research team recently spotted a Linux-based malware family, tracked as DreamBus botnet, targeting Linux servers. Researchers at Zscaler’s ThreatLabZ research team recently analyzed a Linux-based malware family, tracked as DreamBus Botnet, which is a variant of SystemdMiner. The bot is composed of a series of Executable and Linkable Format (ELF) binaries and Unix shell scripts. .

Data Breach Today
JANUARY 27, 2021
Banning Ransom Payments and Unleashing Offensive Hacking Teams Being Mooted With ransomware continuing to fuel a massive surge in illicit profits, some experts have been calling on governments to launch offensive hacking teams to target cybercrime cartels. They're also calling for a review of cyber insurance payouts being used to fund ransoms.

WIRED Threat Level
JANUARY 26, 2021
What if things escalated? What if communications were knocked out? What if cyberwar was just the start? A note about this special six-part series.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

The Last Watchdog
JANUARY 25, 2021
SolarWinds and Mimecast are long-established, well-respected B2B suppliers of essential business software embedded far-and-wide in company networks. Related: Digital certificates destined to play key role in securing DX. Thanks to a couple of milestone hacks disclosed at the close of 2020 and start of 2021, they will forever be associated with putting supply-chain vulnerabilities on the map.

Security Affairs
JANUARY 27, 2021
Apple has addressed three zero-day vulnerabilities in its iOS operating system that have been exploited in the wild. Apple has addressed three zero-day vulnerabilities in iOS that have been exploited in the wild with the release of security updates (iOS 14.4). The first zero-day issue, tracked as CVE-2021-1782, is a race condition that resides in the iOS operating system kernel. “A malicious application may be able to elevate privileges.
Data Breach Today
JANUARY 29, 2021
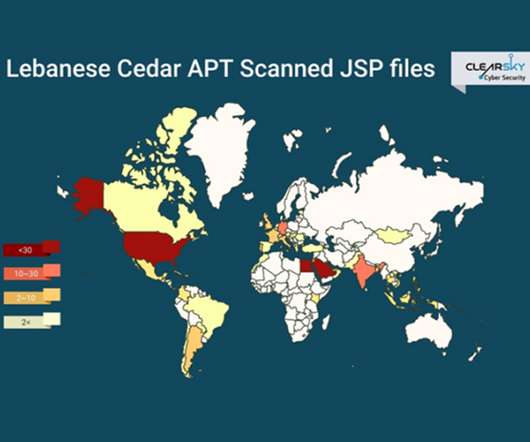
Researchers: Lebanese Cedar's Campaigns Expand Beyond Middle East An APT group known as Lebanese Cedar has launched a cyberespionage campaign targeting telecommunication companies and ISPs, according to the Israeli security firm ClearSky, which says the attacks have spread beyond the Middle East to the U.S. and Europe.

WIRED Threat Level
JANUARY 29, 2021
Researchers from Brown University have developed a system that could keep track of firearms while preserving privacy.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

AIIM
JANUARY 26, 2021
The workplace in 2021 will demand a different set of skills. Now more than ever, organizations need to embrace disruption as a springboard for competitive advantage and adopt new ways of working that invigorate organizational performance. But making the transition isn't just about the technology involved; success requires the ability to effectively manage change itself.

Security Affairs
JANUARY 23, 2021
The Hacker News reported in exclusive that the security firm SonicWall was hacked as a result of a coordinated attack on its internal systems. TheHackerNews revealed in an exclusive that the security provider SonicWall was hacked on Friday. The company was targeted with a coordinated attack on its internal systems, threat actors exploited zero-day vulnerabilities in their VPN solutions, such as NetExtender VPN client version 10.x and Secure Mobile Access ( SMA ). “The San Jose-based compa

Data Breach Today
JANUARY 23, 2021
Incident Forced Intel to Release Results Earlier Than Planned Intel is investigating an incident in which an unauthorized person accessed a portion of the company's latest quarterly financial report, forcing the chipmaker to release its earnings slightly earlier than planned.

WIRED Threat Level
JANUARY 27, 2021
A global operation has taken down the notorious botnet in a blow to cybercriminals worldwide.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

AIIM
JANUARY 28, 2021
"How do we translate an interactive in-person conference experience into a virtual experience?". This was the big question that immediately hit me at exactly at 5:00PM on March 5th, 2020. I remember the moment – we had just closed off a fantastic week with the AIIM Tribe in Dallas, Texas, for The AIIM Conference 2020. I've been leading the events team to produce and coordinate The AIIM Conference for a long time.

Security Affairs
JANUARY 25, 2021
Indian cryptocurrency exchange Buyucoin suffered a security incident, threat actors leaked sensitive data of 325K users. A new incident involving a cryptocurrency exchange made the headlines, the India-based cryptocurrency exchange suffered a security incident, threat actors leaked sensitive data of 325K users on the Dark Web. Leaked data includes names, e-mails, mobile numbers, encrypted passwords, user wallet details, order details, bank details, KYC details (PAN number, passport numbers) and

Data Breach Today
JANUARY 29, 2021
The latest edition of the ISMG Security Report features an analysis of this week’s police takedowns of Emotet and Netwalker cybercrime operations. Also featured: Updates on passwordless authentication and the use of deception technology.

WIRED Threat Level
JANUARY 26, 2021
“We've got a ship in duress that hasn't sent out a distress signal. Something doesn't add up.”.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Schneier on Security
JANUARY 26, 2021
I think this is the largest data breach of all time: 220 million people. ( Lots more stories are in Portuguese.).

Security Affairs
JANUARY 25, 2021
Packaging giant WestRock disclosed a ransomware attack that impacted its information technology (IT) and operational technology (OT) systems. American corrugated packaging company WestRock announced it was the victim of a ransomware attack that impacted its information technology (IT) and operational technology (OT) systems. WestRock did not share details about the security incident, it only confirmed that its staff discovered the attack on January 23.

Data Breach Today
JANUARY 25, 2021
Researchers: 33,000 Vulnerable Servers Could Be Used to Amplify Attacks Threat actors are exploiting vulnerable Microsoft Remote Desktop Protocol servers to amplify DDoS attacks, according to a report from Netscout, which offers mitigation advice.
Let's personalize your content