Good Cyber Hygiene in a Post-Pandemic World Starts with Us
Dark Reading
JUNE 26, 2020
Three ways that security teams can improve processes and collaboration, all while creating the common ground needed to sustain them.

Dark Reading
JUNE 26, 2020
Three ways that security teams can improve processes and collaboration, all while creating the common ground needed to sustain them.

Dark Reading
JUNE 24, 2020
Sensitivity of customer information and time-to-detection determine financial blowback of cybersecurity breaches.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dark Reading
JUNE 23, 2020
Why embracing, not fighting, decentralization will pave the way to smoother cloud migrations.

Security Affairs
JUNE 26, 2020
A man accused to have developed distributed denial of service (DDoS) botnets based on the Mirai botnet was sentenced to 13 months in federal prison. Kenneth Currin Schuchman, 22, of Vancouver, Washington, was sentenced to 13 months in federal prison because it has developed distributed denial of service (DDoS) botnets based on the source code of Mirai botnet.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

WIRED Threat Level
JUNE 22, 2020
The so-called BlueLeaks collection includes internal memos, financial records, and more from over 200 state, local, and federal agencies.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
JUNE 25, 2020
Superseding Indictment Expands Scope of Case, But Doesn't Add Charges The U.S Department of Justice unsealed a superseding indictment against WikiLeaks founder Julian Assange that expands the scope of the government's case against him. Federal prosecutors now allege that Assange conspired with the Anonymous and LulzSec groups to obtain classified information to publish.
Security Affairs
JUNE 21, 2020
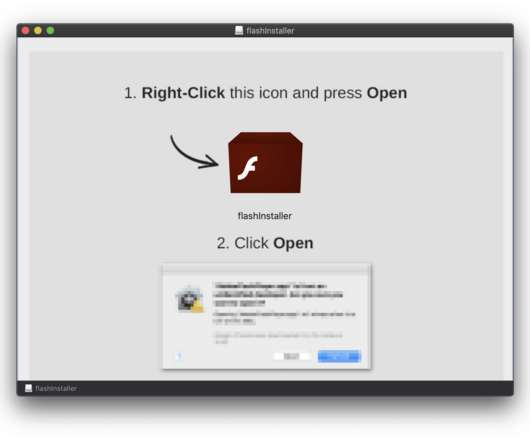
Shlayer Mac malware is back, the Mac threat is now spreading through new black SEO operations. Researchers spotted a new version of the Shlayer Mac malware that is spreading via poisoned Google search results. Researchers at security firm Intego observed the new variant being spread masqueraded as a fake Adobe Flash Player installer (.DMG disk image) and implementing fresh advanced evasion capabilities. “The new malware tricks victims into bypassing Apple’s built-in macOS security protecti

WIRED Threat Level
JUNE 26, 2020
After releasing over a million hacked law enforcement files, DDoSecrets got banned from Twitter. But it has no plans to slow down.
AIIM
JUNE 25, 2020
In recent years, nothing has sparked more controversy in the information management industry than the 2017 Gartner post officially retiring the term “Enterprise Content Management (ECM)” in favor of a new term, content services. Here at AIIM, we’ve been providing independent research, educational training, and certification for over 70 years. For a good majority of that time, the focus has been on ECM and the practices associated with ECM to capture, store, manage, and preserve information.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

Data Breach Today
JUNE 23, 2020
New Risks Could Emerge as More Practices Reopen Four recent cybersecurity incidents that may have involved ransomware demonstrate the ongoing threats facing the sector during the COVID-19 pandemic. They also serve as a warning that extra watchfulness is needed as physicians reopen their clinics.
Security Affairs
JUNE 24, 2020
U.S. business consulting firm Frost & Sullivan suffered a data breach, a threat actor is offering for sale its databases on a hacker forum. U.S. firm Frost & Sullivan suffered a data breach, data from an unsecured backup that were exposed on the Internet was sold by a threat actor on a hacker forum. Frost & Sullivan is a business consulting firm involved in market research and analysis, growth strategy consulting, and corporate training across multiple industries.

WIRED Threat Level
JUNE 21, 2020
Thinking of boosting your SMS security by switching to Signal? These tips make sure your messages come with you—even to a new phone.

The Last Watchdog
JUNE 21, 2020
Ransomware is undoubtedly one of the most unnerving phenomena in the cyber threat landscape. Numerous strains of this destructive code have been the front-page news in global computer security chronicles for almost a decade now, with jaw-dropping ups and dramatic downs accompanying its progress. Related: What local government can do to repel ransomware Ransomware came into existence in 1989 as a primitive program dubbed the AIDS Trojan that was spreading via 5.25-inch diskettes.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Data Breach Today
JUNE 26, 2020
Senior Care Facility Operator Describes Investigation Why are some breach notifications delayed for months? This week, a company that operates senior care facilities in North Carolina and South Carolina issued a statement offering a step-by-step explanation.

Security Affairs
JUNE 26, 2020
German Police have arrested 32 individuals and detained 11 after a series of raids targeting users of an illegal underground economy forum. According to prosecutors in Frankfurt and Bamberg, the German Police have arrested 32 individuals and detained 11 after a series of raids targeting users of the “ crimenetwork.co ” illegal underground economy forum.

WIRED Threat Level
JUNE 24, 2020
Starting today, the search giant will make a previously opt-in auto-delete feature the norm.

AIIM
JUNE 23, 2020
There may be no other industry that could benefit more from automation than the mortgage banking industry. This industry is full of time-consuming, error-prone, and paper and labor-intensive processes, all perfectly-suited for automation. And with huge volumes of loans being generated each year (nearly 5 million new consumer mortgages alone), it may soon become impossible to move forward without the use of automation.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Data Breach Today
JUNE 22, 2020
Campaign Targets Unpatched Software and Weak Authentication, Defenders Warn Hackers wielding Nefilim ransomware are targeting unpatched or poorly secured Citrix remote-access technology, then stealing data, unleashing crypto-locking malware and threatening to dump data to try to force payment, New Zealand's national computer emergency response team warns.

Security Affairs
JUNE 22, 2020
Researchers at Amnesty International collected evidence that a Moroccan journalist was targeted with network injection attacks using NSO Group ‘s spyware. In October 2019, security experts at Amnesty International’s Security Lab have uncovered targeted attacks against Moroccan human rights defenders Maati Monjib and Abdessadak El Bouchattaoui that employed NSO Group surveillance tools.

WIRED Threat Level
JUNE 21, 2020
Computers constantly give off more information than you might realize—which hackers can use to pry out their secrets.

The Guardian Data Protection
JUNE 23, 2020
Local health chiefs say real-time information is crucial to monitor spread of disease Coronavirus – latest updates See all our coronavirus coverage Local outbreaks of Covid-19 could grow undetected because the government is failing to share crucial testing data, council leaders and scientists have warned. More than a month after being promised full details of who has caught the disease in their areas, local health chiefs are still desperately lobbying the government’s testing chief, Lady Harding

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

Data Breach Today
JUNE 24, 2020
How to Avoid Addressing Problems 'Too Far Downstream' Greg van der Gaast, head of information security at the University of Salford in the United Kingdom, has strong opinions on why some security investments aren't reaping maximum benefits. "We are addressing problems too far downstream," he says.

Security Affairs
JUNE 22, 2020
New Zealand police had frozen NZ$140 million (US$90 million) in assets linked to a Russian cyber criminal. New Zealand police announced that they had frozen NZ$140 million (US$90 million) in assets linked to the Russian nation Alexander Vinnik. Alexander Vinnik is currently in France to face a charge of money laundering for organised crime using crypto-currency.

WIRED Threat Level
JUNE 20, 2020
Plus: OnlyFans pirates, a nasty Netgear bug, and more of the week's top security news.

Threatpost
JUNE 25, 2020
Several high-severity flaws in Nvidia's GPU display drivers for Windows users could lead to code-execution, DoS and more.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Data Breach Today
JUNE 24, 2020
Researchers: Cybercrime Group, Formerly Known for Dridex, Is Not Exfiltrating Data The Evil Corp cybercrime group, originally known for the Dridex banking Trojan, is now using new ransomware called WastedLocker, demanding ransom payments of $500,000 to $1 million, according to security researchers at NCC Group's Fox-IT.

Security Affairs
JUNE 20, 2020
Malicious Chrome browser extensions were employed in a surveillance campaign on a large scale, millions of users potentially impacted. Malicious Chrome browser extensions were used in a massive surveillance campaign aimed at users working in the financial services, oil and gas, media and entertainment, healthcare, government organizations, and pharmaceuticals.

WIRED Threat Level
JUNE 23, 2020
At WWDC, the company detailed a litany of privacy-friendly improvements to its software.
Let's personalize your content