6 Free Cybersecurity Training and Awareness Courses
Dark Reading
MAY 12, 2020
Most are designed to help organizations address teleworking risks related to COVID-19 scams.

Dark Reading
MAY 12, 2020
Most are designed to help organizations address teleworking risks related to COVID-19 scams.
Data Breach Today
MAY 11, 2020
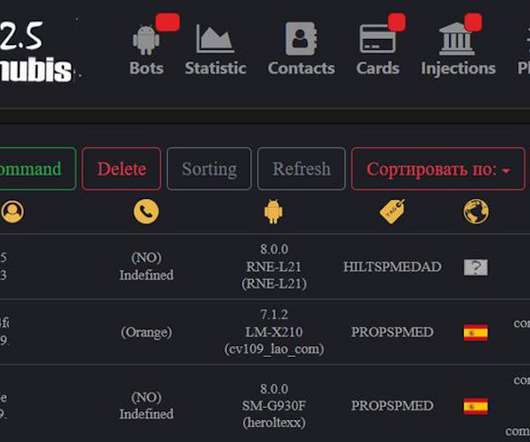
Powerful Platform Can Spot If Victim Is Looking at the Screen Anubis, one of the most potent Android botnets, apparently is getting a refresh a year after its source code was leaked, security researchers say. The changes could help fraudsters more closely monitor activity on hacked devices.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
MAY 12, 2020
Researchers Say New Features and Functionality Added The operators behind the Zeus Sphinx malware have added new features and functionality to the Trojan, and more cybercriminals have deployed it within phishing campaigns that use the COVID-19 crisis as a lure, according to IBM X-Force. The Trojan has become more efficient at stealing banking data.

Jamf
MAY 12, 2020
If the upfront cost is more, how can Mac be less expensive than PC? We examine the numbers and put the Mac versus PC in the enterprise myths to bed.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, CTO of Betterworks, will explore a practical framework to transform Generative AI prototypes into

WIRED Threat Level
MAY 10, 2020
Pick who sees your tweets, posts, and stories—and choose what you want to see, too.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
MAY 13, 2020
FBI, CISA Issue Joint Warning to Organizations Conducting Research Hacking groups linked to China's government are targeting research and healthcare facilities that are working on developing vaccines, testing procedures and treatments for COVID-19, the FBI and the U.S. Cybersecurity and Infrastructure Security Agency warn in an alert.

Data Breach Today
MAY 13, 2020
Australian Shipping Giant, Hit With Nefilim Ransomware, Vows to Not Pay Ransom Australian shipping giant Toll Group has vowed to again not pay a ransom after suffering its second ransomware attack of the year. In the latest incident, however, the company warns that attackers also stole corporate data - and it may get leaked.

Threatpost
MAY 11, 2020
The infostealer has gone above and beyond in its new anti-analysis and obfuscation tactics.

Krebs on Security
MAY 11, 2020
Diebold Nixdorf , a major provider of automatic teller machines (ATMs) and payment technology to banks and retailers, recently suffered a ransomware attack that disrupted some operations. The company says the hackers never touched its ATMs or customer networks, and that the intrusion only affected its corporate network. Canton, Ohio-based Diebold [ NYSE: DBD ] is currently the largest ATM provider in the United States, with an estimated 35 percent of the cash machine market worldwide.

Advertisement
Generative AI is upending the way product developers & end-users alike are interacting with data. Despite the potential of AI, many are left with questions about the future of product development: How will AI impact my business and contribute to its success? What can product managers and developers expect in the future with the widespread adoption of AI?
The Last Watchdog
MAY 13, 2020
Chief Information Security Officers were already on the hot seat well before the COVID-19 global pandemic hit, and they are even more so today. Related: Why U.S. cybersecurity policy needs to match societal values CISOs must preserve and protect their companies in a fast-changing business environment at a time when their organizations are under heavy bombardment.
Data Breach Today
MAY 14, 2020
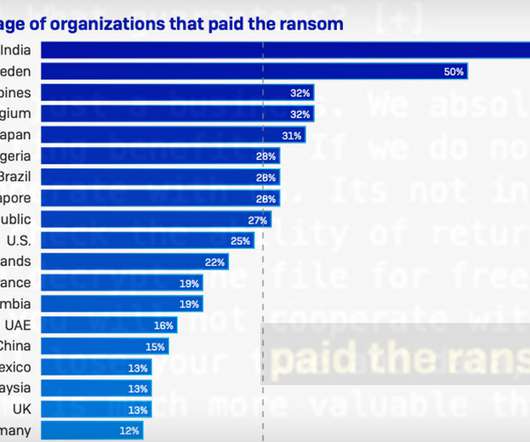
Funding Criminals Perpetuates Cybercrime Security experts and law enforcement officials have long argued that paying ransoms doesn't pay. For starters, it directly funds the cybercrime ecosystem and makes it attractive for criminals to keep launching ransomware attacks.

AIIM
MAY 12, 2020
Each year brings a rapid increase in technological advancements that can benefit both your personal and professional life. Constant tech advancements can make it feel hard to keep up with competing businesses if your company isn't adapting fast enough. In this day and age, digital transformations are integral for a growing business's future, as technology changes the advancements and operations of every company.

Krebs on Security
MAY 12, 2020
Microsoft today issued software updates to plug at least 111 security holes in Windows and Windows-based programs. None of the vulnerabilities were labeled as being publicly exploited or detailed prior to today, but as always if you’re running Windows on any of your machines it’s time once again to prepare to get your patches on. May marks the third month in a row that Microsoft has pushed out fixes for more than 110 security flaws in its operating system and related software.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Hunton Privacy
MAY 12, 2020
The Dutch Data Protection Authority ( Autoriteit Persoonsgegevens , the “Dutch DPA”) recently imposed a €750,000 fine on a company for unlawful processing of employees’ fingerprints for attendance taking and time registration purposes. Biometric data, such as fingerprints, qualify as sensitive personal data under the EU General Data Protection Regulation (the “GDPR”) and their processing is subject to more stringent requirements.

Data Breach Today
MAY 14, 2020
Another Example of How Cybercriminals' Tactics Are Changing Magellan Health, a U.S. managed care company that focuses on specialty areas of healthcare, says it was hit by a ransomware attack that involved the exfiltration of data. Ransomware gangs are increasingly going beyond encrypting data, stealing information to put more pressure on victims to pay ransoms.

AIIM
MAY 14, 2020
We're now operating twenty years into a new millennium. But despite the futuristic potential, many organizations continue to operate with systems and software that are a decade or more behind the times. Organizations that continue to operate in the past will be challenged to keep pace today – and in the future. Think about the technology you use in your personal life.

IT Governance
MAY 14, 2020
With the UK slowly beginning to ease its lockdown measures, organisations have a lot to consider. Some employees who can’t work from home will be itching to get back into the office, in which case you’ll need to take the appropriate steps to make sure they are able to work safely and follow social distancing rules. Other employees will have come to appreciate the benefits of working from home and want to continue to do so.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

IBM Big Data Hub
MAY 12, 2020
AI is transforming how businesses operate and deliver value, while simultaneously improving efficiencies across the organization. Governments have taken an increasingly important role in the advent of COVID-19 as citizens look to government agencies for trusted information for their individual safety, well-being and beyond – to both support and benefit themselves socially, economically and emotionally.

Data Breach Today
MAY 15, 2020
Cybersecurity Expert Reviews Key Questions to Ask Organizations must carefully re-examine their security procedures to make sure they're adequate for the new work-from-home environment during the COVID-19 crisis, says Shelton Newsham, a British law enforcement official who specializes in cybersecurity. He reviews key questions to ask.

Security Affairs
MAY 11, 2020
During COVID-19 outbreak data processors have to be extra vigilant to maintain their compliance with data protection authorities like GDPR. COVID-19 has abruptly changed the world. It has imposed online learning and earning, which in turn has open new doors of cybersecurity threats and data breaches. Now the data processors have to be extra vigilant to maintain their compliance with data protection authorities like GDPR.

DLA Piper Privacy Matters
MAY 13, 2020
The Information Commissioner’s Office (“ ICO ”) has published guidance for employers on complying with data protection law when taking steps to manage Covid-19 health and safety risk in the workplace (“ Guidance ”). The Guidance focuses on ‘testing’ of employees (which includes collecting data about symptoms and the conducting of temperature checks, and well as collecting data about Covid-19 test results), but also touches on other measures which businesses might be considering in order to moni

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Micro Focus
MAY 14, 2020
Micro Focus Virtual Universe launches on May 19! There’s still time to register for this free event—join fellow technology leaders, innovators and Micro Focus solution experts and partners to see how we can help you drive value and innovate faster, with less risk, in the race to digital transformation. Here’s my Top 10 reasons: Top. View Article.

Data Breach Today
MAY 14, 2020
Connected Devices Could Allow Attackers to Target Industrial Systems, Trend Micro Reports The increasing use of internet-connected devices in manufacturing facilities is opening up new ways for hackers to target so-called "smart" factories with unconventional attack methods, according to an analysis by security firm Trend Micro and the Polytechnic University of Milan.

Security Affairs
MAY 15, 2020
Britain’s Ministry of Defence contractor Interserve has been hacked, intruders have stolen up to 100,000 past and present employees’ details. Interserve, a contractor for the Britain’s Ministry of Defence suffered a security breach, hackers have stolen up to 100,000 of past and current employees details. The company currently has around 53,000 employees.

DXC Technology
MAY 13, 2020
Enterprise clients have looked to automate IT support for several years. With millions of employees across the globe now working from home, support needs have increased dramatically, with many unprepared enterprises suffering from long service desk wait times and unhappy employees. Many companies may have already been on a gradual pace to exploit digital solutions […].

Advertisement
Start-ups & SMBs launching products quickly must bundle dashboards, reports, & self-service analytics into apps. Customers expect rapid value from your product (time-to-value), data security, and access to advanced capabilities. Traditional Business Intelligence (BI) tools can provide valuable data analysis capabilities, but they have a barrier to entry that can stop small and midsize businesses from capitalizing on them.

Threatpost
MAY 15, 2020
A new threat group uses NSIS as an installer to target industrial companies with revolving payloads, including LokiBot, FormBook, BetaBot, Agent Tesla and Netwire.

Data Breach Today
MAY 14, 2020
Microsoft Spots Malicious Messages Spreading LokiBot Infostealer Fraudsters are honing their phishing emails tied to the COVID-19 crisis, using fake messages about business continuity plans and new payment procedures to spread the LokiBot information stealer, Microsoft researchers report.

Security Affairs
MAY 13, 2020
The United States Cyber Command (USCYBERCOM) has uploaded five new North Korean malware samples to VirusTotal. The United States Cyber Command (USCYBERCOM) has shared five new malware samples attributed to the North Korea-linked Lazarus APT , it has uploaded the malicious code to VirusTotal. “On May 12, 2020, the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Department of Defense (DoD) released three Malware Analysis Reports (MA
Let's personalize your content