3 security gadgets I never leave home without via ZDNet
IG Guru
FEBRUARY 6, 2023
These gadgets give you a huge advantage over the hackers.

IG Guru
FEBRUARY 6, 2023
These gadgets give you a huge advantage over the hackers.
WIRED Threat Level
FEBRUARY 9, 2023
People in Europe are making GDPR requests to have their private messages erased, but Elon’s team is ignoring them.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
FEBRUARY 10, 2023
Social news aggregation platform Reddit suffered a security breach, attackers gained unauthorized access to internal documents, code, and some business systems. Reddit announced it was hit by a sophisticated and highly-targeted attack that took place on February 5, 2023. A highly-targeted phishing attack hit the employees of the company. The company pointed out that Reddit user passwords and accounts were not compromised.

KnowBe4
FEBRUARY 7, 2023
With the introduction of OpenAI's Chat GPT, artificial intelligence is no longer considered part of science fiction. It has presented a new problem for cybersecurity professionals, as AI-generated malware and hacks can be challenging to detect. AI is undoubtedly having an impact on society, whether it is benefiting or threatening our organizations.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Dark Reading
FEBRUARY 7, 2023
A broken access control vulnerability could have led to dangerous follow-on attacks for users of the money-management app.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Krebs on Security
FEBRUARY 5, 2023
Julius “Zeekill” Kivimäki, a 25-year-old Finnish man charged with extorting a local online psychotherapy practice and leaking therapy notes for more than 22,000 patients online, was arrested this week in France. A notorious hacker convicted of perpetrating tens of thousands of cybercrimes, Kivimäki had been in hiding since October 2022, when he failed to show up in court and Finland issued an international warrant for his arrest.

Security Affairs
FEBRUARY 10, 2023
A ransomware attack hit the City of Oakland this week, forcing it to take all systems offline in response to the incident. The City of Oakland disclosed a ransomware attack, the security breach began on Wednesday night. In an abundance of caution, the City of Oakland has taken impacted systems offline, while they work to secure the impacted infrastructure. “The City of Oakland has learned that it was recently subject to a ransomware attack that began on Wednesday night.

WIRED Threat Level
FEBRUARY 10, 2023
A review of the FBI’s access to foreign intelligence reveals troubling misuse of powerful surveillance tech.

Data Breach Today
FEBRUARY 6, 2023
Data Leaked from a Thrid-Party Vendor U.S. wireless telecom USCellular says a data breach at a third party vendor resulted in a leak of 52,000 named and email addresses. The company confirmed that data from the leak is available for download on a criminal data breach forum.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m
Krebs on Security
FEBRUARY 7, 2023
KrebsOnSecurity will likely have a decent amount of screen time in an upcoming Hulu documentary series about the 2015 megabreach at marital infidelity site Ashley Madison. While I can’t predict what the producers will do with the video interviews we shot, it’s fair to say the series will explore compelling new clues as to who may have been responsible for the attack.

Security Affairs
FEBRUARY 10, 2023
The TA886 hacking group targets organizations in the United States and Germany with new spyware tracked as Screenshotter. A recently discovered threat actor, tracked as TA886 by security firm Proofpoint, is targeting organizations in the United States and Germany with new malware dubbed Screenshotter. The experts first spotted the attacks attributed to this threat actor in October 2022, they believe that the group is financially motivated.

WIRED Threat Level
FEBRUARY 7, 2023
Biden’s speech proves that protecting personal info is no longer a fringe issue. Now, Congress just needs to do something about it.

Data Breach Today
FEBRUARY 6, 2023
Aleksanteri Kivimaki Charged With Mental Health Patient Data Breach and Extortion French police arrested hacker Aleksanteri Kivimäki, 25, who's suspected of hacking and extorting a Finnish mental health service provider, leaking patient data and extorting 25,000 patients. The suspect was formerly convicted of disrupting thousands of websites when he was a teenager.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Krebs on Security
FEBRUARY 9, 2023
Authorities in the United States and United Kingdom today levied financial sanctions against seven men accused of operating “ Trickbot ,” a cybercrime-as-a-service platform based in Russia that has enabled countless ransomware attacks and bank account takeovers since its debut in 2016. The U.S. Department of the Treasury says the Trickbot group is associated with Russian intelligence services, and that this alliance led to the targeting of many U.S. companies and government entities.

Security Affairs
FEBRUARY 10, 2023
North Korea-linked APT groups conduct ransomware attacks against healthcare and critical infrastructure facilities to fund its activities. Ransomware attacks on critical infrastructure conducted by North Korea-linked hacker groups are used by the government of Pyongyang to fund its malicious cyber operations, U.S. and South Korean agencies warn. US CISA published a Cybersecurity Advisory (CSA) to provide information about the threat actors to network defenders.

The Last Watchdog
FEBRUARY 7, 2023
Throughout 2022, we saw hackers become far more sophisticated with their email-based cyber attacks. Using legitimate services and compromised corporate email addresses became a norm and is likely to continue in 2023 and beyond. Related: Deploying human sensors Additionally, with tools like ChatGPT, almost anyone can create new malware and become a threat actor.

Data Breach Today
FEBRUARY 8, 2023
Hackers Actively Scanning for Backups to Steal Access Credentials, Researchers Warn Researchers at Sansec warn that 12% of e-commerce sites they studied publicly expose private backups and that hackers are actively scanning for them. Such backups can give attackers customer data, passwords and other details required to gain remote, administrator-level access to an environment.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
FEBRUARY 4, 2023
Plus: The FTC cracks down on GoodRx, Microsoft boots “verified” phishing scammers, researchers disclose EV charger vulnerabilities, and more.

Security Affairs
FEBRUARY 9, 2023
Researchers reported that the top-of-the-line Android mobile devices sold in China are shipped with malware. China is currently the country with the largest number of Android mobile devices, but a recent study conducted by researchers from the University of Edinburgh and the Trinity College of Dublin revealed that top-of-the-line Android devices sold in the country are shipped with spyware.

The Last Watchdog
FEBRUARY 8, 2023
Arguably one of the biggest leaps forward an enterprise can make in operational reliability, as well as security, is to shore up its implementations of the Public Key Infrastructure. Related: Why the ‘Matter’ standard matters Companies have long relied on PKI to deploy and manage the digital certificates and cryptographic keys that authenticate and protect just about every sensitive digital connection you can name.
Data Breach Today
FEBRUARY 9, 2023
Updates by Attacker Block Decryption Workaround and Tracking, Researchers Warn Attackers targeting unpatched VMware ESXi hypervisors to hit virtual machines have reportedly modified their ESXiArgs ransomware to prevent victims from using decryption workarounds identified by researchers. The campaign has already amassed nearly 3,000 known victims and could have many more.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

WIRED Threat Level
FEBRUARY 6, 2023
Moscow promised residents lower crime rates through an expansive smart city project. Then Vladimir Putin invaded Ukraine.

Security Affairs
FEBRUARY 9, 2023
Experts warn of new ESXiArgs ransomware attacks using an upgraded version that makes it harder to recover VMware ESXi virtual machines. Experts spotted a new variant of ESXiArgs ransomware targeting VMware ESXi servers, authors have improved the encryption process, making it much harder to recover the encrypted virtual machines. The new variant was spotted less than a week after the first alert was launched by CERT-FR warning of an ESXi ransomware targeting thousands of VMware servers in a globa

Weissman's World
FEBRUARY 8, 2023
It’s no secret that infogov and records management can be difficult and frustrating – increasingly so as traditional areas like policy development, process improvement, compliance, retention, and destruction have begun banging into once-separate and quickly growing disciplines like privacy and security. What seems to be lesser-known, though, is that there’s a remarkably universal strategic recipe… Read More » Same Recipe, Different Clientele Cooking Up Effective Programs for Records,

Data Breach Today
FEBRUARY 8, 2023
Twitter Falters After Post Length for Twitter Blue Users Rises to 4,000 Characters Three of the planet's largest social media platforms suffered outages Wednesday, blocking some users at Twitter, Instagram and YouTube from accessing their accounts. At Twitter, many users received a message Wednesday saying they were "over the daily limit" and were unable to post.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

WIRED Threat Level
FEBRUARY 8, 2023
Biden’s speech calling for better data protections got a standing ovation from both sides of the aisle. So, where’s a federal privacy law?
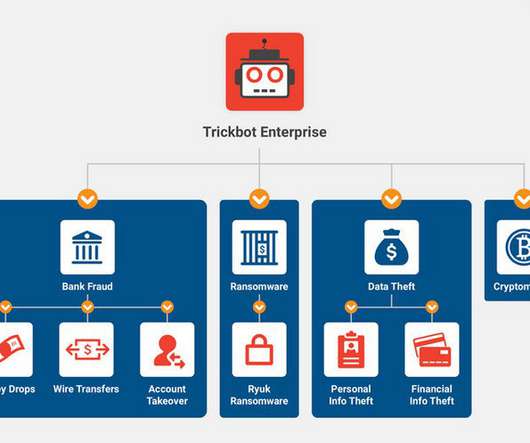
Security Affairs
FEBRUARY 9, 2023
The US and the UK have sanctioned seven Russian individuals for their involvement in the TrickBot operations. The US and the UK authorities have sanctioned seven Russian individuals for their involvement in the TrickBot operations. The US Treasury has frozen the assets belonging to the individuals and imposed travel bans against them. The US Treasury points out that persons that engage in certain transactions with the sanctioned individuals may themselves be exposed to designation. “Today,
Troy Hunt
FEBRUARY 9, 2023
I think I've pretty much captured it all in the title of this post but as of about a day ago, Pwned Passwords now has full parity between the SHA-1 hashes that have been there since day 1 and NTLM hashes. We always had both as a downloadable corpus but as of just over a year ago with the introduction of the FBI data feed , we stopped maintaining downloadable behemoths of data.
Let's personalize your content