Securing Your Remote Workforce: A Coronavirus Guide for Businesses
Dark Reading
MARCH 30, 2020
Often the hardest part in creating an effective awareness program is deciding what NOT to teach.

Dark Reading
MARCH 30, 2020
Often the hardest part in creating an effective awareness program is deciding what NOT to teach.
Security Affairs
APRIL 3, 2020
Experts revealed that an unauthorized party compromised more than 200 million user records hosted somewhere within the U.S. in a Google Cloud database. . Many people are now so accustomed to cloud computing that they use it multiple times per day, whether to collaborate with co-workers, log into email accounts or do other everyday tasks. The convenience is undoubtedly one of its perks.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
APRIL 1, 2020
Daniel's Hosting, which hosts about 7,600 dark web portals for free, has been hacked and is down. It's unclear when, or if, it will be back up.

WIRED Threat Level
MARCH 31, 2020
The hotel chain has suffered its second major breach in 16 months. Here's how to find out if you're affected.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Data Breach Today
APRIL 2, 2020
Andy Bates of Global Cyber Alliance on 'Work From Home, Secure Your Business' The Global Cyber Alliance is one of 13 nonprofit organizations that have banded together to offer businesses security tips for their newly remote workforces. Andy Bates, executive director of the alliance, discusses the coalition's core guidelines for reducing cyber risk.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Security Affairs
MARCH 30, 2020
The Zeus Sphinx malware is back, operators are now spreading it exploiting the interest in the Coronavirus outbreak. The Zeus Sphinx malware is back, it was observed in a new wave of attacks attempting to exploit the interest in the Coronavirus outbreak. Experts from IBM X-Force uncovered a hacking campaign employing the Zeus Sphinx malware, as known as Zloader or Terdot , that focus on government relief payments. .
Security Affairs
MARCH 29, 2020
In this post, I decided to share the details of the Coronavirus-themed attacks launched from March 22 to March 28, 2020. Threat actors exploit the interest in the COVID19 outbreak while infections increase worldwide, experts are observing new campaigns on a daily bases. Below a list of attacks detected this week. March 23 – COVID19-themed campaign delivers a new variant of Netwalker Ransomware.
Krebs on Security
APRIL 2, 2020
As the Coronavirus pandemic continues to force people to work from home, countless companies are now holding daily meetings using videoconferencing services from Zoom. But without the protection of a password, there’s a decent chance your next Zoom meeting could be “Zoom bombed” — attended or disrupted by someone who doesn’t belong.

Data Breach Today
MARCH 30, 2020
Privacy Gaffe Blamed on Facebook's iOS Software Development Kit Zoom has apologized for sharing large sets of user data by default with Facebook, blaming the social network's software development kit, which it has removed from its iOS app. With COVID-19 driving unprecedented levels of remote working, video conferencing software is under the privacy and security microscope.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

WIRED Threat Level
APRIL 1, 2020
A class action lawsuit. Rampant zoombombing. And as of today, two new zero-day vulnerabilities.
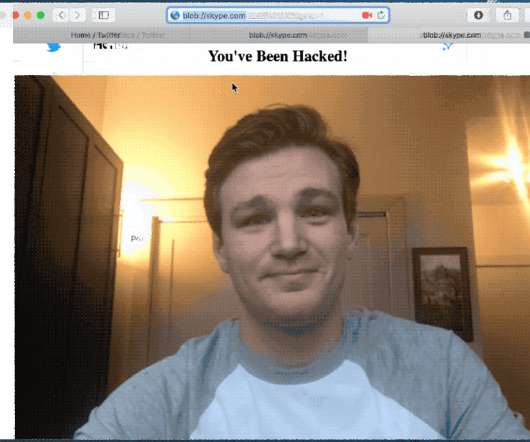
Security Affairs
APRIL 3, 2020
Bad news for Apple iPhone or MacBook users, attackers could hack their device’s camera by tricking them into visiting a website. The ethical hacker Ryan Pickren demonstrated that it is possible to hack Apple iPhone or MacBook users by simply tricking them into visiting a website with the Safari browser. Pickren reported seven vulnerabilities to Apple that rewarded him with a $75,000 bounty.
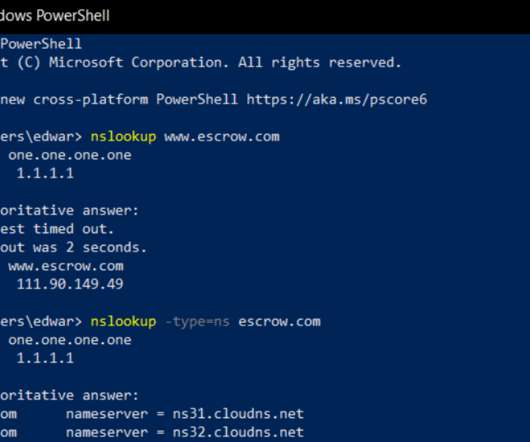
Krebs on Security
MARCH 31, 2020
A spear-phishing attack this week hooked a customer service employee at GoDaddy.com , the world’s largest domain name registrar, KrebsOnSecurity has learned. The incident gave the phisher the ability to view and modify key customer records, access that was used to change domain settings for a half-dozen GoDaddy customers, including transaction brokering site escrow.com.

Data Breach Today
APRIL 1, 2020
Strangers Could Start a Chat with Someone Using Same Email Domain Popular teleconferencing software Zoom is continuing to fall under scrutiny as questions are raised over its privacy and security practices. The latest issue: a feature that inadvertently reveals strangers' email addresses and profile photos.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

AIIM
MARCH 31, 2020
Many of us find ourselves working from home – often rather suddenly and unexpectedly. Organizations of all sizes and in all industries are now in the position of figuring out how to ensure that the business of the business continues while staff stay home and practice effective social distancing. The good news is that the technology needed for effective working from home exists and is generally mature – though some providers have found that the sudden surge in volume can cause issues with particu
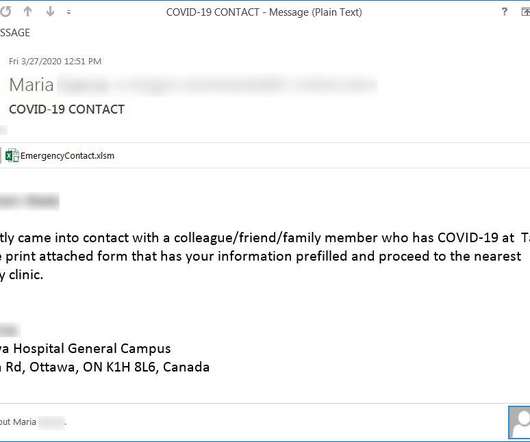
Security Affairs
MARCH 30, 2020
Security experts uncovered a new Coronavirus-themed phishing campaign, the messages inform recipients that they have been exposed to the virus. Experts continue to spot Coronavirus-themed attack, a new phishing campaign uses messages that pretend to be from a local hospital informing the victims they have been exposed to the virus and that they need urgently to be tested.
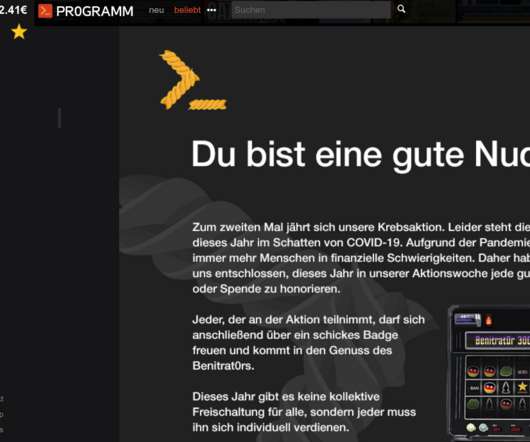
Krebs on Security
MARCH 30, 2020
In 2018, KrebsOnSecurity unmasked the creators of Coinhive — a now-defunct cryptocurrency mining service that was being massively abused by cybercriminals — as the administrators of a popular German language image-hosting forum. In protest of that story, forum members donated hundreds of thousands of euros to nonprofits that combat cancer (Krebs means “cancer” in German).

Data Breach Today
MARCH 30, 2020
Will Hacking Incidents, Other Breaches Continue to Rise During COVID-19 Pandemic? The total number of health data breaches - and individuals affected - on the 2020 tally has more than doubled in recent weeks. Here are the details.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
APRIL 3, 2020
They've been patched, but the Safari vulnerabilities would have given an alarming amount of access.
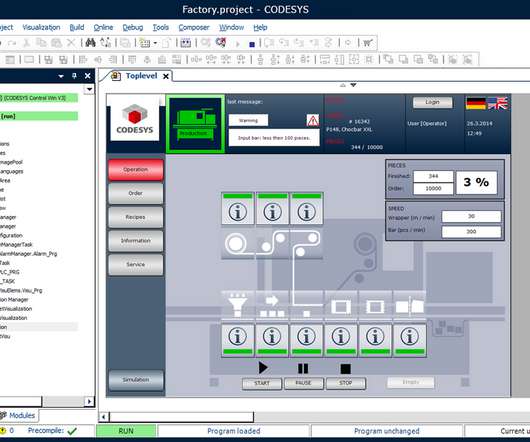
Security Affairs
MARCH 28, 2020
Experts discovered an easily exploitable heap-based buffer overflow flaw, tracked as CVE-2020-10245, that exists in the CODESYS web server. A critical heap-based buffer overflow flaw in a web server for the CODESYS automation software for engineering control systems could be exploited by a remote, unauthenticated attacker to crash a server or execute arbitrary code.

The Last Watchdog
MARCH 31, 2020
DevOps is now table stakes for any company hoping to stay competitive. Speed and agility is the name of the game. And everyone’s all-in. Related: A firewall for microservices DevSecOps arose to insert security checks and balances into DevOps, aiming to do so without unduly degrading speed and agility. If you’re thinking that speed and security are like oil and water, you’re right.

Data Breach Today
MARCH 31, 2020
Wide Variety of Personal Information Exposed Marriott acknowledged Tuesday that a recent data breach exposed the personal records of millions of hotel guests. It's the second major breach reported by the hotel giant in two years.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

WIRED Threat Level
APRIL 3, 2020
The service's mixed messages have frustrated cryptographers, as the US government and other sensitive organizations increasingly depend on it.

Security Affairs
MARCH 31, 2020
Marriott disclosed a new security breach detected at the end of February 2020 that could impact up to 5.2 million of its guests. Marriott International discloses a data breach that exposed the personal information of roughly 5.2 million hotel guests, the incident was detected at the end of February 2020. “At the end of February 2020, we identified that an unexpected amount of guest information may have been accessed using the login credentials of two employees at a franchise property.

The Last Watchdog
APRIL 1, 2020
Deploying the latest, greatest detection technology to deter stealthy network intruders will take companies only so far. Related: What we’ve learned from the massive breach of Capitol At RSA 2020 , I learned about how one of the routine daily chores all large organizations perform — data governance — has started to emerge as something of a cybersecurity multiplier.
Data Breach Today
MARCH 31, 2020
Remote Desktop Protocol: Experts See No Apocalypse, But Urge Better Defenses As the coronavirus drives a massive upsurge in remote working, a review of remote desktop protocol usage suggests RDP adoption hasn't spiked. But as IT teams rely more heavily on remote access, experts warn that too many RDP systems remain internet-exposed.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

WIRED Threat Level
MARCH 28, 2020
Plus: A Windows zero day, an iOS watering hole, and more of the week's top security news.
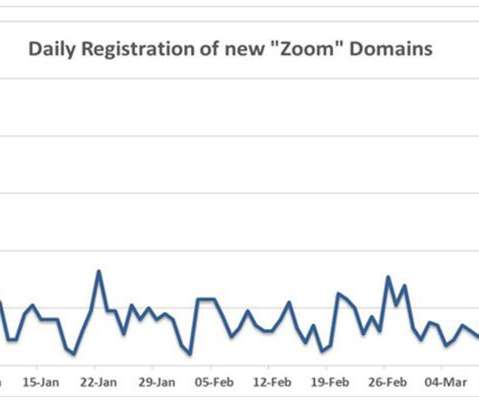
Security Affairs
MARCH 30, 2020
Online communication platforms such as Zoom are essential instruments at the time of Coronavirus outbreak, and crooks are attempting to exploit their popularity. The Coronavirus outbreak is changing our habits and crooks are attempting to take advantage of the popularity of online communication platforms such as Zoom that are used by businesses, school classrooms and normal users.

The Last Watchdog
MARCH 30, 2020
Agile software innovation is the order of the day. Wonderous digital services are the result. Related: Micro-segmentation taken to the personal device level The flip side, of course, is that an already wide-open attack surface – one that has been getting plundered for the past two decades by criminal hacking groups — is getting scaled up, as well.
Let's personalize your content