PayPal Phishing Scam Uses Invoices Sent Via PayPal
Krebs on Security
AUGUST 18, 2022
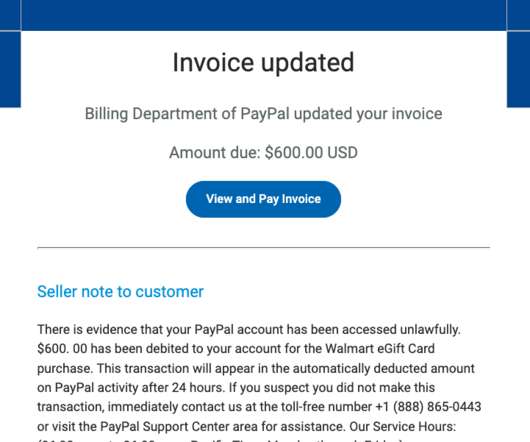
Scammers are using invoices sent through PayPal.com to trick recipients into calling a number to dispute a pending charge. The missives — which come from Paypal.com and include a link at Paypal.com that displays an invoice for the supposed transaction — state that the user’s account is about to be charged hundreds of dollars. Recipients who call the supplied toll-free number to contest the transaction are soon asked to download software that lets the scammers assume remote cont






































Let's personalize your content