Hidden Costs of a Data Breach
Dark Reading
FEBRUARY 22, 2022
Don't consider just the initial costs. Hidden factors include remediation, revenue loss, reputational harm, national security — even human life.

Dark Reading
FEBRUARY 22, 2022
Don't consider just the initial costs. Hidden factors include remediation, revenue loss, reputational harm, national security — even human life.

Krebs on Security
FEBRUARY 22, 2022
Missouri Governor Mike Parson made headlines last year when he vowed to criminally prosecute a journalist for reporting a security flaw in a state website that exposed personal information of more than 100,000 teachers. But Missouri prosecutors now say they will not pursue charges following revelations that the data had been exposed since 2011 — two years after responsibility for securing the state’s IT systems was centralized within Parson’s own Office of Administration.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
FEBRUARY 24, 2022
A reported loss of $171 Million. Huge sum, right? Related: Supply-chain hacks prove worrisome. Yes, and that is what Sony exactly lost when they were hacked and the personal info of every one of its customers leaked in 2011. This came to the news because Sony is one of the biggest names on the planet. Every second, even while you are reading this article, a hacker is trying to hack a site.

Security Affairs
FEBRUARY 24, 2022
US and UK cybersecurity agencies provided details of a new malware used by Iran-linked MuddyWater APT. CISA, the FBI, the US Cyber Command’s Cyber National Mission Force (CNMF), UK’s National Cyber Security Centre (NCSC-UK), and the NSA, and law enforcement agencies have published a joint advisory on new malware used by Iran-linked MuddyWater APT group (aka SeedWorm and TEMP.Zagros ) in attacks aimed at critical infrastructure worldwide.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

WIRED Threat Level
FEBRUARY 23, 2022
Western intelligence services are raising alarms about Cyclops Blink, the latest tool at the notorious group’s disposal.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

The Last Watchdog
FEBRUARY 21, 2022
The headlines are disturbing: Breach of patient records ; Surgeries and appointments cancelled due to IT outage ; and even, Death attributed to ransomware attack on hospital. Related: High-profile healthcare hacks in 2021. The risks are real, and the impact of cybersecurity events continues to grow. A cyber catastrophe may seem inevitable, but there are basic practices and actionable steps any healthcare organization can take to begin reducing the clear and present risk of being impacted by a cy

Security Affairs
FEBRUARY 19, 2022
The U.S. CISA has created a list of free cybersecurity tools and services that can help organizations increase their resilience. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) announced this week that it has compiled a list of free cybersecurity tools and services that can help organizations to reduce cybersecurity risk and increase resilience.

WIRED Threat Level
FEBRUARY 24, 2022
By promising a response “never seen” in history if other countries interfere in Ukraine, the Russian leader upended decades of relative stability.

Dark Reading
FEBRUARY 25, 2022
A lot of the recommended preparation involves measures organizations should have in place already.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m
eSecurity Planet
FEBRUARY 24, 2022
Professional penetration testers , or pen testers, are akin to “white hat” or ethical hackers, adversaries with an explicit authorization to attack a network. During this simulation of real-world conditions, they put an IT system to the test to identify vulnerabilities. The goal is to patch these vulnerabilities to prevent cybercriminals from exploiting them.
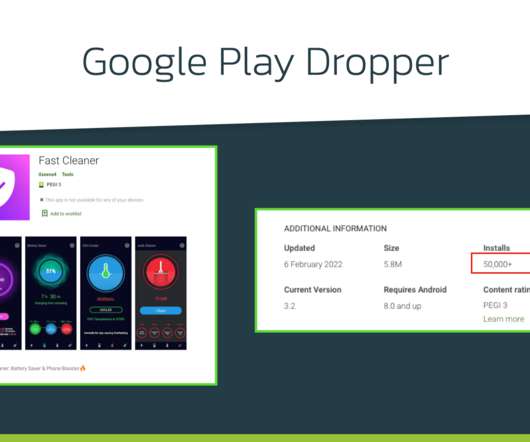
Security Affairs
FEBRUARY 21, 2022
Xenomorph Android trojan has been observed distributed via the official Google Play Store targeting 56 European banks. Researchers from ThreatFabric have spotted a new Android banking trojan, dubbed Xenomorph , distributed via the official Google Play Store that has over 50,000 installations. The banking Trojan was used to target 56 European banks and steal sensitive information from the devices of their customers.

WIRED Threat Level
FEBRUARY 22, 2022
Anything from a metallic Rubik’s cube to an aluminum trash can inside a room could give away your private conversations.

Schneier on Security
FEBRUARY 23, 2022
A Berlin-based company has developed an AirTag clone that bypasses Apple’s anti-stalker security systems. Source code for these AirTag clones is available online. So now we have several problems with the system. Apple’s anti-stalker security only works with iPhones. (Apple wrote an Android app that can detect AirTags, but how many people are going to download it?

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.
IT Governance
FEBRUARY 22, 2022
Information security management is a way of protecting an organisation’s sensitive data from threats and vulnerabilities. The process is typically embedded via an ISMS (information security management system) , which provides the framework for managing information security. At the centre of the framework is information risk management in, which organisations assess risks and the ways that they can compromise the confidentiality, integrity and availability of information.

Security Affairs
FEBRUARY 23, 2022
Iranian national media corporation, Islamic Republic of Iran Broadcasting (IRIB), was hit by a wiper malware in late January 2022. An investigation into the attack that hit the Islamic Republic of Iran Broadcasting (IRIB) in late January, revealed the involvement of a disruptive wiper malware along with other custom-made backdoors, and scripts and configuration files used to install and configure the malicious executables.

WIRED Threat Level
FEBRUARY 19, 2022
Plus: A crypto crime crackdown, Roblox ripoffs, and more of the week’s top security news.

Hunton Privacy
FEBRUARY 24, 2022
On February 23, 2022, the European Commission adopted a Proposal for a Regulation designed to harmonize rules on the fair access to and use of data generated in the EU across all economic sectors (the “Data Act”). The Data Act is intended to “ensure fairness in the digital environment, stimulate a competitive data market, open opportunities for data-driven innovation and make data more accessible for all.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Schneier on Security
FEBRUARY 22, 2022
The US National Cyber Director Chris Inglis wrote an essay outlining a new social contract for the cyber age: The United States needs a new social contract for the digital age — one that meaningfully alters the relationship between public and private sectors and proposes a new set of obligations for each. Such a shift is momentous but not without precedent.
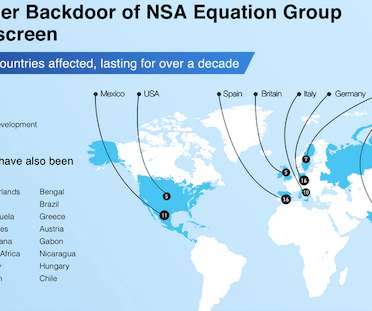
Security Affairs
FEBRUARY 23, 2022
Pangu Lab researchers disclosed details of the Bvp47 backdoor that was used by the US NSA Equation Group. Researchers from The China’s Pangu Lab have disclosed details of a Linux top-tier APT backdoor, tracked as Bvp47, which is associated with the U.S. National Security Agency (NSA) Equation Group. The name “ Bvp47 ” comes form numerous references to the string “Bvp” and the numerical value “0x47” used in the encryption algorithm.

WIRED Threat Level
FEBRUARY 20, 2022
You get a safer, more secure browser experience, but Google gets a lot more data about you.

eSecurity Planet
FEBRUARY 23, 2022
How can a hospital protect an MRI machine with an unchangeable password and still connect it to the network? How can an industrial recycler safely secure its $400,000 hard drive recertification rack with control software that only runs on Windows XP? These are not uncommon risks. The devices themselves can’t be secured, but that doesn’t mean we can’t use basic IT techniques to reduce our security risks.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

Dark Reading
FEBRUARY 25, 2022
Ukraine's Computer Emergency Response Team calls out UNIC1151 nation-state hacking group out of Belarus as behind the attacks.

Security Affairs
FEBRUARY 24, 2022
Cybersecurity experts discovered a new data wiper malware that was used in attacks against hundreds of machines in Ukraine. The threat of hybrid warfare is reality, Russia-linked APT group have supported the operations of the Russian army while preparing for the invasion. Researchers from cybersecurity firms ESET and Broadcom’s Symantec discovered a new data wiper malware that was employed in a recent wave of attacks that hit hundreds of machines in Ukraine.

WIRED Threat Level
FEBRUARY 23, 2022
Researchers at iSTARE have to think like the bad guys, finding critical flaws before processors go to production.

eSecurity Planet
FEBRUARY 25, 2022
Rainbow table attacks are an older but still effective tactic for threat actors targeting password database vulnerabilities. Today’s advanced persistent threats might elect for more sophisticated methods like remote desktop protocol (RDP) attacks, but cryptanalytic attacks – the inspection of cryptographic systems for vulnerabilities – remain a legitimate concern in the landscape of cybersecurity threats.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Troy Hunt
FEBRUARY 24, 2022
I feel the need, the need for speed. Faster, Faster, until the thrill of speed overcomes the fear of death. If you're in control, you're not going fast enough. And so on and so forth. There's a time and a place for going fast, and there's no better place to do that than when querying Have I Been Pwned's Pwned Passwords service.

Security Affairs
FEBRUARY 22, 2022
US cookware distributor giant Meyer Corporation discloses a data breach that affected thousands of its employees. Meyer Corporation, the second-largest cookware distributor globally, has disclosed a data breach that affects thousands of its employees. The attack took place on October 25, 2021, as reported by the data breach notification letter shared with the U.S.

WIRED Threat Level
FEBRUARY 19, 2022
The mandatory patch addressed a critical vulnerability in a widely used plugin that allowed untrusted visitors to download a website's backups.
Let's personalize your content