The 5 Love Languages of Cybersecurity
Dark Reading
FEBRUARY 14, 2020
When it comes to building buy-in from the business, all cybersecurity needs is love -- especially when it comes to communication.

Dark Reading
FEBRUARY 14, 2020
When it comes to building buy-in from the business, all cybersecurity needs is love -- especially when it comes to communication.

Data Breach Today
FEBRUARY 11, 2020
Researchers Say Trojan's Developers Devising Ways to Spread Trojan to More Devices Security researchers have found that the developers of the Emotet Trojan have created a new way to spread it to more victims - attackers are using unsecured WiFi networks as a way to deliver the malware to more devices.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Adam Levin
FEBRUARY 10, 2020
As if cybersecurity weren’t already a red-letter issue, the United States and, most likely, its allies–in other words, the global economic community–are in Iran’s cyber sites, a major player in cyber warfare and politically divisive disinformation campaigns. The “slap” as Ayatollah Ali Khamenei described it was a ballistic missile attack on a target that had three hours to get out of harm’s way.

Security Affairs
FEBRUARY 13, 2020
The popular Italian hacktivist collective LulzSec ITA claimed via Twitter to have hacked three Italian universities. The popular Italian hacktivist collective LulzSec ITA has announced via Twitter the hack of three Italian universities, highlighting the importance of the cybersecurity for our society. Abbiamo fatto visita a @UnivRoma3 , nella speranza che oltre alla sicurezza, possa migliorare anche il futuro dei nostri giovani!

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

WIRED Threat Level
FEBRUARY 14, 2020
The encryption app is putting a $50 million infusion from WhatsApp cofounder Brian Acton to good use, building out features to help it go mainstream.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Krebs on Security
FEBRUARY 11, 2020
Microsoft today released updates to plug nearly 100 security holes in various versions of its Windows operating system and related software, including a zero-day vulnerability in Internet Explorer (IE) that is actively being exploited. Also, Adobe has issued a bevy of security updates for its various products, including Flash Player and Adobe Reader/Acrobat.

Security Affairs
FEBRUARY 13, 2020
Huawei can secretly tap into communications through the networking equipment, states a U.S. official , while White House urge allies to ban the Chinese giant. This week The Wall Street Journal reported that U.S. officials say Huawei can covertly access telecom networks where its equipment is installed. “U.S. officials say Huawei Technologies Co. can covertly access mobile-phone networks around the world through “back doors” designed for use by law enforcement, as Washington tries to persua

WIRED Threat Level
FEBRUARY 13, 2020
New research from MIT shows that the Voatz app appears to have some glaring security holes.

Data Breach Today
FEBRUARY 12, 2020
Security Researcher Finds Emails and Internal Company IT Logs Were Accessible An unsecured, internet-facing database belonging to cosmetic giant Estee Lauder exposed over 440 million company records, including email addresses and IT logs, a researcher discovered. What can be done to prevent such mishaps?

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m
Krebs on Security
FEBRUARY 10, 2020
The U.S. Justice Department today unsealed indictments against four Chinese officers of the People’s Liberation Army (PLA) accused of perpetrating the 2017 hack against consumer credit bureau Equifax that led to the theft of personal data on nearly 150 million Americans. DOJ officials said the four men were responsible for carrying out the largest theft of sensitive personal information by state-sponsored hackers ever recorded.

Security Affairs
FEBRUARY 14, 2020
A Russian court fined Twitter and Facebook 4 million rubles each for refusing to store the personal data of Russian citizens on local servers. At the end of January, Russia’s telecommunications watchdog Roskomnadzor instituted administrative proceedings against Facebook and Twitter after they refused to store data of Russian users on servers located in the country.

WIRED Threat Level
FEBRUARY 11, 2020
Equifax. Anthem. Marriott. OPM. The data that China has amassed about US citizens will power its intelligence activities for a generation.
Data Breach Today
FEBRUARY 14, 2020
Irish Data Protection Authority Questions Impact of New Service Any lonely hearts in Europe hoping to meet the person of their dreams via Facebook's dating service on Valentine's Day this year will have to wait a little longer. The social network has delayed the EU rollout of its dating service, following a Monday "dawn raid" by Irish privacy investigators.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Krebs on Security
FEBRUARY 14, 2020
In May 2013, the U.S. Justice Department seized Liberty Reserve , alleging the virtual currency service acted as a $6 billion financial hub for the cybercrime world. Prompted by assurances that the government would one day afford Liberty Reserve users a chance to reclaim any funds seized as part of the takedown, KrebsOnSecurity filed a claim shortly thereafter to see if and when this process might take place.
Security Affairs
FEBRUARY 10, 2020
Malaysia’s MyCERT issued a security alert to warn of a hacking campaign targeting government officials that was carried out by the China-linked APT40 group. Malaysia’s Computer Emergency Response Team (MyCERT) warns of a cyber espionage campaign carried out by the China-linked APT40 group aimed at Malaysian government officials. The attackers aimed at stealing confidential documents from government systems after having infected them with malware. “ MyCERT observed an increase i
AIIM
FEBRUARY 12, 2020
In today's digital era of information technology, a company needs to consider several factors to decide how to manage their data and documents online. A large share of companies have now adopted cloud-based infrastructure, but many still rely on the tried-and-true legacy of on-premises document management software programs. If you, too, are in a dilemma as to which solution is right for your business, stick around as here is a detailed comparison between cloud and on-premises document solutions.

Data Breach Today
FEBRUARY 13, 2020
Coronavirus Will Not Alter Plans for Event in San Francisco While public health concerns over the spread of the coronavirus are leading to the cancellation of some international events, the RSA Conference 2020 will proceed as scheduled in San Francisco Feb. 24-28.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
FEBRUARY 11, 2020
One analysis of news outlets found that the median popular right-wing site planted 73 percent more cookies than its left-wing counterpart.

Security Affairs
FEBRUARY 9, 2020
Iran comes under cyber-attack again, a massive offensive brought down a large portion of the Iranian access to the Internet. Iran infrastructures are under attack, a massive cyberattack brought down a large portion of the Iranian access to the Internet, according to the experts the national connectivity fell to 75%. The N etBlocks internet observatory, which tracks disruptions and shutdowns, observed yesterday (February 8, 2019) a massive outage of the country’s connectivity to the Interne

AIIM
FEBRUARY 11, 2020
I recently watched a webinar by Jason Baron called " Vanishing Acts: The Challenge of Dealing with Ephemeral and Self-Destructing Messaging Apps in the Workplace. " Jason's a really smart guy and has written about ephemeral messaging in business before. While I agree with him generally, I think information professionals, and especially those in government or highly regulated sectors, really need to think about the risks involved with the use of these apps.

Data Breach Today
FEBRUARY 10, 2020
Class Action Suits Would Focus on PIH Health Breach That Affected 200,000 Several law firms are racing to be among the first to file class action lawsuits against PIH Health in the wake of the California-based regional healthcare network reporting last month that a 2019 phishing breach affected nearly 200,000 individuals. Why the rush?

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

WIRED Threat Level
FEBRUARY 10, 2020
The Department of Justice has pinned the hack on China. Here's how it was done, according to the indictment.
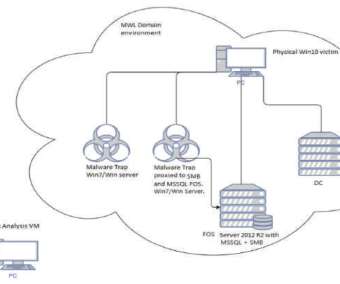
Security Affairs
FEBRUARY 8, 2020
Hackers have infected with a piece of malware some IoT devices running Windows 7 designed by three of the world’s largest manufacturers. Security experts from TrapX reported that some IoT devices running Windows 7 have been infected with a piece of malware, is it a supply chain attack? The experts reported that several IoT devices at some major manufacturers have been infected with a cryptocurrency miner in October 2019.

erwin
FEBRUARY 13, 2020
When an organization’s data governance and metadata management programs work in harmony, then everything is easier. Data governance is a complex but critical practice. There’s always more data to handle, much of it unstructured; more data sources, like IoT, more points of integration, and more regulatory compliance requirements. Creating and sustaining an enterprise-wide view of and easy access to underlying metadata is also a tall order.

Data Breach Today
FEBRUARY 11, 2020
Researchers Describe a Wide Variety of Tactics As fears about the coronavirus continue to spread, cybercriminals are using the health crisis to send phishing emails using a variety of tactics to a broader range of targets.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

WIRED Threat Level
FEBRUARY 8, 2020
Machine-learning programs are analyzing websites, news reports, and social media posts for signs of symptoms, such as fever or breathing problems. .

Security Affairs
FEBRUARY 14, 2020
The Federal Bureau of Investigation (FBI) and Cybersecurity and Infrastructure Security Agency (CISA) released reports on North Korea-linked HIDDEN COBRA malware. The FBI, the US Cyber Command, and the Department of Homeland Security have published technical details of a new North-Korea linked hacking operation. The government experts released new and updated Malware Analysis Reports (MARs) related to new malware families involved in new attacks carried out by North Korea-linked HIDDEN COBRA gro

OpenText Information Management
FEBRUARY 11, 2020
Cloud computing is now touching all aspects of information technology, and document and data archiving is no exception. When it comes to security, cost savings, reliable services and scalability, there is no bigger advantage than storing your most valuable assets in the cloud. But migrating to the cloud is more complex than simply moving your … The post 5 key things to consider when migrating to the cloud appeared first on OpenText Blogs.
Let's personalize your content