How AI Will Supercharge Spear-Phishing
Dark Reading
OCTOBER 21, 2020
To keep pace with intelligent, unpredictable threats, cybersecurity will have to adopt an intelligent security of its own.
Dark Reading
OCTOBER 21, 2020
To keep pace with intelligent, unpredictable threats, cybersecurity will have to adopt an intelligent security of its own.
Data Breach Today
OCTOBER 20, 2020
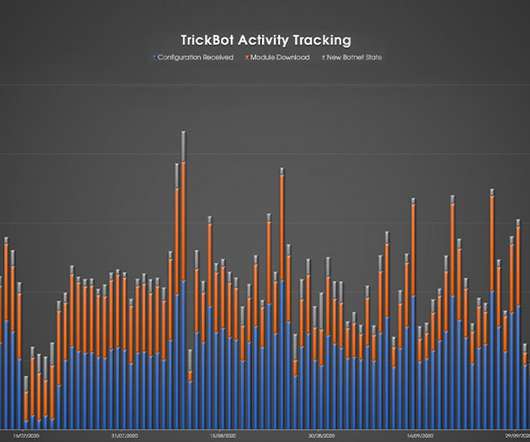
CrowdStrike: Botnet's Activity Has Already Picked Up The recent "takedown" of Trickbot by Microsoft and others had only a temporary effect; the botnet's activity levels have already rebounded, according to Crowdstrike and other security firms.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

WIRED Threat Level
OCTOBER 22, 2020
In an interview with WIRED, Facebook's chief privacy officers argue that the company has turned a corner. Again.

Security Affairs
OCTOBER 19, 2020
A hacker collective claims to have hacked over 50,000 home security cameras and published their footage online, some of them on adult sites. A group of hackers claims to have compromised over 50,000 home security cameras and published their private footage online. Some footages were published on adult sites, experts reported that crooks are offering lifetime access to the entire collection for US$150.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.
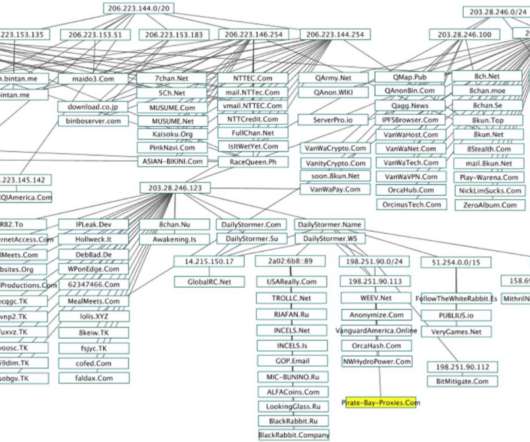
Krebs on Security
OCTOBER 22, 2020
Some of the world’s largest Internet firms have taken steps to crack down on disinformation spread by QAnon conspiracy theorists and the hate-filled anonymous message board 8chan. But according to a California-based security researcher, those seeking to de-platform these communities may have overlooked a simple legal solution to that end: Both the Nevada-based web hosting company owned by 8chan’s current figurehead and the California firm that provides its sole connection to the Inte
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

WIRED Threat Level
OCTOBER 19, 2020
The Department of Justice has named and charged six men for allegedly carrying out many of the most costly cyberattacks in history.

Security Affairs
OCTOBER 19, 2020
Researchers from the Ben-Gurion University of the Negev demonstrated how to fool self-driving cars by displaying virtual objects. A group of researchers from the Ben-Gurion University of the Negev demonstrated that it is possible to fool self-driving cars by displaying virtual objects (phantoms). The experts define as phantom a depthless visual object used to deceive ADASs and cause these systems to perceive it as real.

The Last Watchdog
OCTOBER 19, 2020
There is no shortage of innovative cybersecurity tools and services that can help companies do a much better job of defending their networks. Related: Welcome to the CyberXchange Marketplace In the U.S. alone, in fact, there are more than 5,000 cybersecurity vendors. For organizations looking to improve their security posture, this is causing confusion and vendor fatigue, especially for companies that don’t have a full time Chief Information Security Officer.

Data Breach Today
OCTOBER 20, 2020
DOJ: Russian GRU Officers Targeted 2018 Olympics, French Elections and More The U.S. Justice Department unsealed indictments against six Russian military officers on Monday, alleging that they carried out a series of major hacking operations, including deploying destructive NotPetya malware - tied to more than $10 billion in damages - and attacking the 2018 Olympics.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

WIRED Threat Level
OCTOBER 23, 2020
A report finds 50,000 cases where law enforcement agencies turned to outside firms to bypass the encryption on a mobile device.
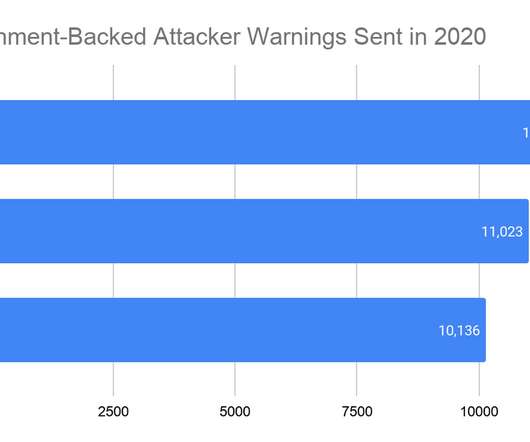
Security Affairs
OCTOBER 17, 2020
On Thursday, four JavaScript packages have been removed from the npm portal because they have been found containing malicious code. NPM staff removed four JavaScript packages from the npm portal because were containing malicious code. Npm is the largest package repository for any programming language. The four packages, which had a total of one thousand of downloads, are: plutov-slack-client nodetest199 nodetest1010 npmpubman . “Any computer that has this package installed or running sh

AIIM
OCTOBER 22, 2020
As you already know, people are more likely to follow your rules after they buy in to the reasons behind them. But you can take it one step further, and provide your “rules” as solutions instead of orders. Amazon’s Kindle publishing team understands this concept well. I was preparing the Kindle edition of my recent book , following the production of the softcover edition.

Data Breach Today
OCTOBER 21, 2020
Researchers Find Pfizer Drug Customer Messages Accessible on Internet For the second time within a week, it's been revealed that sensitive voice messages containing patients' information have been exposed on the internet. The latest discovery involves unsecured voice transcripts of patient calls to drug giant Pfizer's automated customer support system.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

WIRED Threat Level
OCTOBER 22, 2020
From targeted misinformation to manipulated data, these are the cybersecurity concerns election officials worry about most.
Security Affairs
OCTOBER 20, 2020
The Nefilim ransomware operators have posted a long list of files that appear to belong to Italian eyewear and eyecare giant Luxottica. Luxottica Group S.p.A. is an Italian eyewear conglomerate and the world’s largest company in the eyewear industry. As a vertically integrated company, Luxottica designs, manufactures, distributes and retails its eyewear brands, including LensCrafters, Sunglass Hut, Apex by Sunglass Hut, Pearle Vision, Target Optical, Eyemed vision care plan, and Glasses.com.

AIIM
OCTOBER 21, 2020
In this episode of AIIM On Air , I speak with Sue Trombley, Managing Director of Thought Leadership for Iron Mountain. We discuss the biggest impacts on the workplace from Covid-19 and the challenges and opportunities of the new normal of business today. While remote work is a new reality for many organizations and workers, not all people and positions can work from home.

Data Breach Today
OCTOBER 21, 2020
Indictments Are Just a First Step Toward a Crackdown The U.S. indictment charging that six Russian GRU military intelligence officers were responsible for numerous cyberattacks highlights Moscow's seemingly unending appetite for online destruction. Experts say more than indictments will be required to curb such activity.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
OCTOBER 23, 2020
The message is meant to deter any similar attack against US infrastructure.

Security Affairs
OCTOBER 23, 2020
French IT outsourcer Sopra Steria hit by ‘cyberattack’, Ryuk ransomware suspected. French IT outsourcer Sopra Steria has been hit by a ransomware attack, while the company did not reveal the family of malware that infected its systems, local media speculate the involvement of the Ryuk ransomware. “A cyber attack was detected on the Sopra Steria computer network on the evening of October 20.

AIIM
OCTOBER 20, 2020
Before we start, let’s take a minute to address the big elephant in the room. You’re probably thinking, “ Where are you going with this sales angle, Sean? I work with records and information, and my job is all about managing, protecting, and storing it. I don’t sell a thing! ”. Well, what we’re going to cover today will show you that you ARE, in fact, in the business of selling when it comes to Information Governance – it’s just a slightly different model than we’re all used to.

Data Breach Today
OCTOBER 19, 2020
DOJ: Russian GRU Officers Targeted 2018 Olympics, French Elections and More The U.S. Justice Department unsealed indictments against six Russian military officers on Monday, alleging that they carried out a series of major hacking operations, including deploying NotPetya ransomware - causing over $10 billion in damages - and attacking the 2018 Olympics.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

WIRED Threat Level
OCTOBER 17, 2020
Plus: Barnes and Noble got hacked, Zoom adds real end-to-end encryption, and more of the week's top security news.

Security Affairs
OCTOBER 22, 2020
According to the ENISA Threat Landscape Report 2020, cyberattacks are becoming more sophisticated, targeted, and in many cases undetected. I’m proud to present the ENISA Threat Landscape Report 2020 , the annual report published by the ENISA that provides insights on the evolution of cyber threats for the period January 2019-April 2020. The 8th annual ENISA Threat Landscape (ETL) report was compiled by the European Union Agency for Cybersecurity (ENISA), with the support of the European Commiss
Schneier on Security
OCTOBER 19, 2020
Researchers are tricking autopilots by inserting split-second images into roadside billboards. Researchers at Israel’s Ben Gurion University of the Negev … previously revealed that they could use split-second light projections on roads to successfully trick Tesla’s driver-assistance systems into automatically stopping without warning when its camera sees spoofed images of road signs or pedestrians.

Data Breach Today
OCTOBER 22, 2020
US Indictment Airs Russian Military's Dirty Laundry Although Russia's elite nation-state hackers are capable of waging destructive attacks, the GRU military intelligence Sandworm operators have not been able to remain in the shadows, a U.S.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Dark Reading
OCTOBER 19, 2020
The testing firm's website says it has 'ceased operations' as of Oct. 15.

Security Affairs
OCTOBER 23, 2020
The US government declared that Russia-linked APT group Energetic Bear has breached US government networks and exfiltrated data. A joint security advisory published by The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) revealed that Russia-linked APT group Energetic Bear has breached US government networks and exfiltrated data.

Threatpost
OCTOBER 22, 2020
Up to 50,000 Office 365 users are being targeted by a phishing campaign that purports to notify them of a "missed chat" from Microsoft Teams.
Let's personalize your content