FBI Warns of AI-Assisted Phishing Campaigns
KnowBe4
MAY 15, 2024
The US Federal Bureau of Investigation’s (FBI’s) San Francisco division warns that threat actors are increasingly using AI tools to improve their social engineering attacks.

KnowBe4
MAY 15, 2024
The US Federal Bureau of Investigation’s (FBI’s) San Francisco division warns that threat actors are increasingly using AI tools to improve their social engineering attacks.

Data Breach Today
MAY 15, 2024
What It Means, Who Is Affected by It and How to Overcome It Imposter syndrome is a psychological phenomenon in which individuals doubt their accomplishments and have an internalized fear of being exposed as a fraud. Employees can overcome these fears by finding mentors, documenting achievements and engaging in continuous learning.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
MAY 16, 2024
Meeting the demands of the modern-day SMB is one of the challenges facing many business leaders and IT operators today. Traditional, office-based infrastructure was fine up until the point where greater capacity was needed than those servers could deliver, vendor support became an issue, or the needs of a hybrid workforce weren’t being met. Related: SMB brand spoofing In the highly competitive SMB space, maintaining and investing in a robust and efficient IT infrastructure can be one of the ways

Security Affairs
MAY 12, 2024
Black Basta ransomware affiliates have breached over 500 organizations between April 2022 and May 2024, FBI and CISA reported. The FBI, CISA, HHS, and MS-ISAC have issued a joint Cybersecurity Advisory (CSA) regarding the Black Basta ransomware activity as part of the StopRansomware initiative. Black Basta has targeted at least 12 critical infrastructure sectors, including Healthcare and Public Health.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

WIRED Threat Level
MAY 13, 2024
Amid a rising tide of adversary drones and missile attacks, laser weapons are finally poised to enter the battlefield.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Krebs on Security
MAY 13, 2024
Last week, the United States joined the U.K. and Australia in sanctioning and charging a Russian man named Dmitry Yuryevich Khoroshev as the leader of the infamous LockBit ransomware group. LockBit’s leader “ LockBitSupp ” claims the feds named the wrong guy, saying the charges don’t explain how they connected him to Khoroshev.
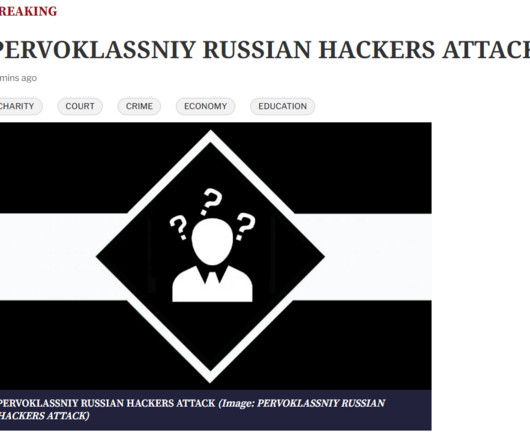
Security Affairs
MAY 13, 2024
A group of hackers that defines itself as “first-class Russian hackers” claims the defacement of hundreds of local and regional British newspaper websites. A group claiming to be “first-class Russian hackers” defaced numerous local and regional British newspaper websites owned by Newsquest Media Group. The group defaced the home pages of the targeted websites and posted the message “PERVOKLASSNIY RUSSIAN HACKERS ATTACK.” The following image shows an archived version of t

WIRED Threat Level
MAY 14, 2024
A coalition of digital rights groups is demanding the US declassify records that would clarify just how expansive a major surveillance program really is.
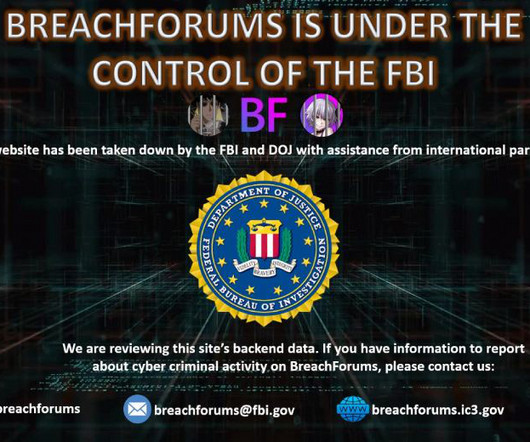
Data Breach Today
MAY 15, 2024
Website of BreachForums Administrator 'Baphomet' Also Appears to Be Down An international law enforcement operation shut down BreachForums, a criminal forum where hackers posted and sold the contents of hacked databases. The website of the criminal forum in its clear and dark web domains displays a seizure notice stating that it is "under the control of the FBI.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m
Krebs on Security
MAY 14, 2024
Microsoft today released updates to fix more than 60 security holes in Windows computers and supported software, including two “zero-day” vulnerabilities in Windows that are already being exploited in active attacks. There are also important security patches available for macOS and Adobe users, and for the Chrome Web browser, which just patched its own zero-day flaw.
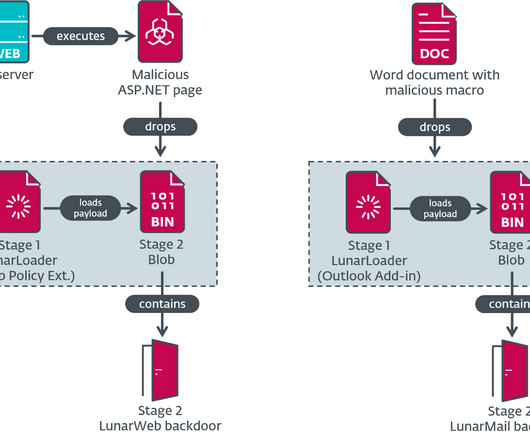
Security Affairs
MAY 17, 2024
Russia-linked Turla APT allegedly used two new backdoors, named Lunar malware and LunarMail, to target European government agencies. ESET researchers discovered two previously unknown backdoors named LunarWeb and LunarMail that were exploited to breach European ministry of foreign affairs. The two backdoors are designed to carry out a long-term compromise in the target network, data exfiltration, and maintaining control over compromised systems.

WIRED Threat Level
MAY 13, 2024
Tuesday’s verdict in the trial of Alexey Pertsev, a creator of crypto-privacy service Tornado Cash, is the first in a string of cases that could make it much harder to skirt financial surveillance.

Data Breach Today
MAY 16, 2024
Law Enforcment Arrests an Arizona Woman and a Ukrainian National U.S. law enforcement swept up two people and possibly hundreds of laptops used in scams by North Korean IT workers to obtain remote employment, including as contractors for an unnamed U.S. cybersecurity company. Prosecutors say one scam run by an Arizona woman netted Pyongyang at least $6.8 million.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Collaboration 2.0
MAY 13, 2024
We tested the best travel VPNs that offer solid security and fast connections while you're on the road, working remotely, or vacationing.

Security Affairs
MAY 13, 2024
Apple rolled out urgent security updates to address code execution vulnerabilities in iPhones, iPads, and macOS. Apple released urgent security updates to address multiple vulnerabilities in iPhones, iPads, macOS. The company also warns of a vulnerability patched in March that the company believes may have been exploited as a zero-day. The issue impacts older iPhone devices, it is tracked as CVE-2024-23296 and is a memory corruption flaw in the RTKit.

WIRED Threat Level
MAY 13, 2024
NYC mayor Eric Adams wants to test Evolv’s gun-detection tech in subway stations—despite the company saying it’s not designed for that environment. Emails obtained by WIRED show how the company still found an in.

Data Breach Today
MAY 16, 2024
Also: Turla Targets European Missions and Google Patches Chrome Zero-Days This week, hackers used a Linus backdoor and a Microsoft client management tool; Santander Bank, the Helsinki Education Division, an Australian energy provider and auction house Christie's were breached; hackers targeted European missions in the Middle East; and Google patched a zero-day flaw.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Elie
MAY 17, 2024
Exploring the societal impact of the GenAI workforce entering the market.

Security Affairs
MAY 16, 2024
The Spanish bank Santander disclosed a data breach at a third-party provider that impacted customers in Chile, Spain, and Uruguay. The Spanish financial institution Santander revealed a data breach involving a third-party provider that affected customers in Chile, Spain, and Uruguay. The bank recently became aware of unauthorized access to one of its databases hosted by a third-party provider.
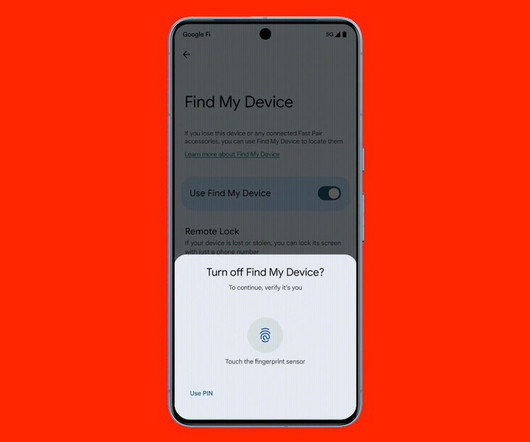
WIRED Threat Level
MAY 15, 2024
Google is introducing new AI-powered safety tools in Android 15 that can lock down your phone if thieves nab it.

Data Breach Today
MAY 14, 2024
UK GCHQ Director Calls Chinese Hacking a 'Top Priority' Chinese-backed espionage and cyber disruption pose a major threat to global critical infrastructure as Beijing races for global edge, British and U.S. cyber officials warned Tuesday. Responding to the scale and complexity of Chinese hacking is a top British priority.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

The Last Watchdog
MAY 16, 2024
Hardware-based cybersecurity solutions are needed to help defend company networks in a tumultuous operating environment. Related: World’s largest bank hit by ransomware attack While software solutions dominated RSA Conference 2024 and are essential for multi-layered defense of an expanding network attack surface, hardware security solutions can serve as a last line of defense against unauthorized access to sensitive data and tampering with systems.

Security Affairs
MAY 15, 2024
An international law enforcement operation coordinated by the FBI led to the seizure of the notorious BreachForums hacking forum. BreachForums is a cybercrime forum used by threat actors to purchase, sell, and exchange stolen data, including credentials, and personal and financial information. The authorities also seized the Telegram page for the hacking forum The website currently displays a message that informs visitors it was seized by law enforcement.

WIRED Threat Level
MAY 11, 2024
Plus: China is suspected in a hack targeting the UK’s military, the US Marines are testing gun-toting robotic dogs, and Dell suffers a data breach impacting 49 million customers.

Data Breach Today
MAY 17, 2024
Covered Financial Institutions Have 30 Days to Notify Customers of Data Breaches The Securities and Exchange Commission unanimously approved updated regulations for covered financial institutions requiring entities such as fund companies and investment advisers to notify customers within 30 days of a cyber incident that compromised their data.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.
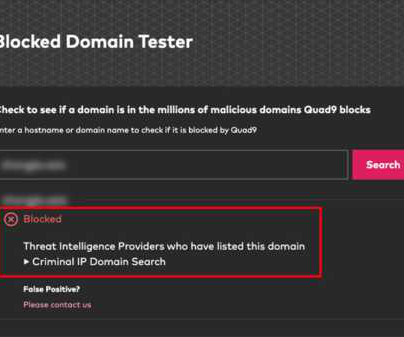
The Last Watchdog
MAY 13, 2024
Torrance, Calif., May 13, 2024, CyberNewsWire — Criminal IP, a renowned Cyber Threat Intelligence (CTI) search engine developed by AI SPERA, has recently signed a technology partnership to exchange threat intelligence data based on domains and potentially on the IP address to protect users by blocking threats to end users. Criminal IP underwent rigorous data evaluation to integrate with Quad9’s threat-blocking service, demonstrating high data uniqueness and accuracy.

Security Affairs
MAY 14, 2024
Google released emergency security updates to address an actively exploited Chrome zero-day vulnerability. Google has released emergency security updates to address a high-severity zero-day vulnerability vulnerability, tracked as CVE-2024-4761, in the Chrome browser. The vulnerability is an out-of-bounds write issue that resides in the V8 JavaScript engine of the Google web browser.

Schneier on Security
MAY 14, 2024
Google has patched another Chrome zero-day: On Thursday, Google said an anonymous source notified it of the vulnerability. The vulnerability carries a severity rating of 8.8 out of 10. In response, Google said, it would be releasing versions 124.0.6367.201/.202 for macOS and Windows and 124.0.6367.201 for Linux in subsequent days. “Google is aware that an exploit for CVE-2024-4671 exists in the wild,” the company said.
Let's personalize your content